While the damage of malware "Gooligan" infected over 1 million Android phones is expanding, the target application list is

ByCyberHades
Malware that infects an Android terminal and acquires the root authority of the terminal illegallyGooligan"Check Point Software Technologies" survey of the security company has revealed that more than 1,000,000 Google accounts are damaged by the distribution of apps that are set up. This malware gains Root permission after infecting the terminal and steals data from 'Google Play', 'Gmail', 'Google Photos' etc by unauthorized access to the Google account by stealing the authentication token , It is said that the number of terminals that are damaged by pace of 13,000 units per day continues to increase even after the discovery.
More Than 1 Million Google Accounts Breached by Gooligan | Check Point Blog
http://blog.checkpoint.com/2016/11/30/1-million-google-accounts-breached-gooligan/
According to Check Point, the structure of Gooligan is shown in the figure below. An attacker puts Gooligan's code in an Android application and offers the application on a third-party Android app store or website that is not Google Play. When the user downloads and installs this application, Gooligan sends the terminal information to "Command & Control Server" prepared by the attacker and installs the tool kit to acquire root authority. And after obtaining Root, download malware from the server, put it in the terminal, steal the authentication token of the Gmail account, and click on "Google Play" "Gmail" "Google Photos" "Google Documents" "G Suite" "Google Drive" It is now possible to extract the data stored in the service.
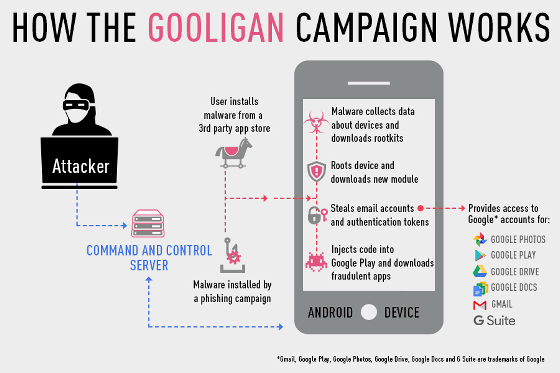
Furthermore, it is possible that malware can exploit maliciously by downloading an application illegally from Google Play, giving a high rating to a specific application, installing an advertisement application, and bringing advertisement revenue to an attacker. According to the survey, there are few cases where the user's data was actually extracted, and it is considered as the immediate object to spread the malware itself.
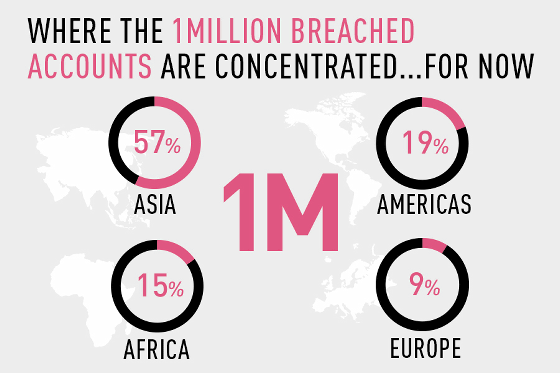
The device infected by Gooligan is equipped with Android 4 (Jelly Bean, KitKat) and Android 5 (Lollipop), and 74% of the Android terminals currently on the market fall under this category. Also, of the 1 million accounts damaged by this unauthorized access, we know that 57% or more were accounts of Asian users.
Check Point has already notified Google about this, and Google advises measures such as notifying the damaged account and invalidating the stolen token. Also, in third-party app store where you can get paid things for free, probability of infecting this malicious application is high, so we urge you not to use it easily.
List of apps with problems announced by Check Point as of November 30, 2016 are as follows.
· Perfect Cleaner
· Demo
· WiFi Enhancer
· Snake
· Gla.pev.zvh
· Html 5 Games
· Demm
· Memory booster
· แข่ง รถ สุด โหด
· StopWatch
· Clear
· BallSmove _ 004
· Flashlight Free
· Memory booste
· Touch Beauty
· Demoad
· Small Blue Point
· Battery Monitor
· Kiichiro
· UC Mini
· Shadow Crush
· Sex Photo
Small white spot
· Tub.ajy.ics
· Hip Good
· Memory Booster
· Phone booster
· SettingService
· Wifi Master
· Fruit Slots
· System Booster
· Dircet Browser
· FUNNY DROPS
· Puzzle Bubble-Pet Paradise
·GPS
· Light Browser
· Clean Master
· YouTube Downloader
· KXService
· Best Wallpapers
· Smart Touch
Light Advanced
· SmartFolder
· Youtubeplayer
· Beautiful Alarm
· PronClub
· Detecting instrument
· Calculator
· GPS Speed
· Fast Cleaner
· Blue Point
· CakeSweety
· Pedometer
· Compass Lite
· Fingerprint unlock
· PornClub
· Com.browser.provider
· Assistive Touch
· Sex Cademy
· OneKeyLock
· Wifi Speed Pro
· Minibooster
· Com.so.itouch
· Com.fabullacop.loudcallernameringtone
· Kiss Browser
· Weather
· Chrono Marker
· Slots Mania
· Multifunction Flashlight
· So Hot
· Google
· HotH5Games
· Swamm Browser
· Billiards
· TcashDemo
· Sexy hot wallpaper
· Wifi Accelerate
· Simple Calculator
· Daily Racing
· Talking Tom 3
· Com.example.ddeo
· Test
· Hot Photo
· QPlay
· Virtual
· Music Cloud
Related Posts:







