Developed a device "Introspection Engine" to prevent that Snowden from specifying location information from smartphone

US National Security Agency(NSA)In order to prevent 'leakage of information from smartphone' that Mr. Edward Snowden who exposed the fact that private information was gathered with the cooperation of private Internet and IT companies is happening before the user is aware of it We published a new study of.
Edward Snowden's New Research Aims to Keep Smartphones From Betraying Their Owners
https://theintercept.com/2016/07/21/edward-snowdens-new-research-aims-to-keep-smartphones-from-betraying-their-owners/
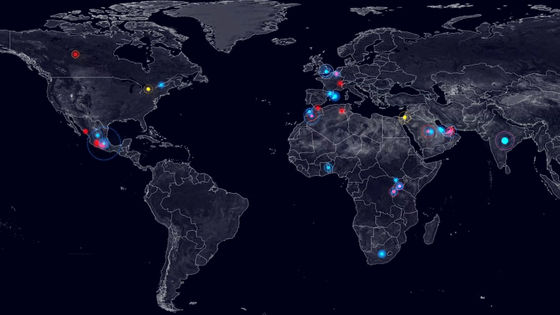
In early 2012, he was an international journalist and belonged to the London Sunday TimesMary KolvinHe joined Syria's Homs as he interviewed conflict zones. Mr. Kolvin said about the route entering Syria, "It seems to be a route for smuggling importers, I can not clarify the details, but in the dark we flew over the walls and fell into the mud only groove "It is revealing that we entered Syria with a harsh route.
Although Mr. Korvin secretly entered Syria, the Syrian army ordered soldiers "kill any journalists who stepped on Syria's land," and bombarded the media center where Mr. Corbin was actually working. In February 2012, Mr. Kolvin and other journalists who were interviewing by anti-government forces died after receiving government cannonballs. The details of how the Syrian Army discovered the location information of Mr. Kolvin, who should have acted secretly, is unknown, but the American net mediaThe Intercept"It may be that he succeeded in locating the position from Mr. Corbin's cell phone."
The Syrian Military Intelligence Division seems to be using a signal intercepting device to monitor communications of satellite broadcasting antennas and mobile phones and to track journalists. For dangerous lands like Syria in a state of confusion in the war, smartphones are an indispensable tool for journalists and activists. However, this also becomes a powerful tracker at the same time, which also leads to informing the owner's whereabouts.

ByVincent Diamante
In order to solve this situation, Mr. Edward Snowden is working on new research in cooperation with famous hacker Andrew Buny Huang. They said that they are developing a countermeasure to the potential risks of smartphones "where smartphones created anywhere can be monitored as long as wireless communication is used". And two of them insist that the user interface (UI) of the smartphone "does not convey the correct state of the wireless communication", and it is precisely the right thing to correctly tell this is to take measures against the dangers of the smartphone I believe that.
Mr. Hoangreverse engineeringIt is a person who has surveyed many Microsoft's Xbox and other hardware so far. From such experience, Mr. Hoang seems to have studied various forms of encryption. Mr. Snowden says, "He is a very important research partner" about Mr. Hoang.
Smartphones can send and receive various wireless communications such as GMS, LTE, and other Bluetooth mobile communication standards such as Wi-Fi. And by intercepting these wireless communications you can identify the source. Therefore, if you want to prevent location identification, you need to turn off any wireless communication on the smartphone. However, according to Mr. Snowden and Mr. Hoang, "There are malware packages sold at a price that one individual can sell, turn on the wireless communication function without causing any change on the UI of the smartphone There are things that you can do, believing in the airplane mode display of a hacked phone is similar to driving a car drunk. "
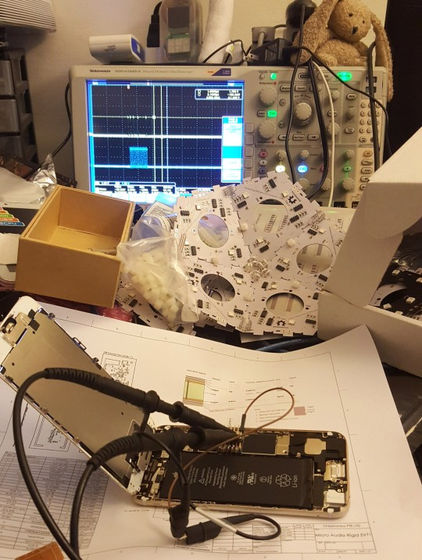
Since the UI of the smartphone can falsify the state of wireless communication, the goal of Mr. Snowden et al. Is to "provide a tool that can directly observe and investigate the wireless condition of the terminal irrespective of the hardware etc. of the smartphone" . In other words, they are attached to smartphones, they sense a suspicious radio emission of the terminal and warn you, they are totally separate devices from smartphones, so the two people call this "Introspection Engine" .
The Introspection Engine is a terminal with a built-in battery, and it is used by attaching it to a smartphone. When installed it looks like a smartphone wearing a case with an external battery. However, the Introspection Engine has a dedicated screen, where the "real radio status" of the installed terminal is displayed. When the Introspection Engine detects some kind of radio waves from the terminal, it can also warn the user with an audible alarm sound, forcibly drop the power of the terminal.
Modeling image of Introspection Engine

According to Mr. Snowden, Introspection Engine will be developed under full open source. Also, for example, even if the terminal is hacked and some sort of eavesdropping software is installed, it seems that the Introspection Engine will operate without problems. Furthermore, it seems to aim at what can be easily used even by people who use it for the first time with an intuitive interface. The Introspection Engine is still in the process of developing a prototype.
Mr. Snowden and Mr. Hoang reported the results to MIT Media Research Institute's "Forbidden Research(Prohibited research) "in the event that(PDF)Details announceddoing.
Related Posts: