"Malicious hardware" that Google engineers tongues as "Satanic as wise" appears
ByBruce Guenter
In security issues, the word "Malware (Malicious + Software)" often comes up, but the research team at the University of Michigan "Malicious hardwareIt is pointed out the existence of.
A2: Analog Malicious Hardware
(PDF file)http://www.impedimenttoprogress.com/storage/publications/A2_SP_2016.pdf

This 'Demonically Clever' Backdoor Hides In a Tiny Slice of a Computer Chip | WIRED
https://www.wired.com/2016/06/demonically-clever-backdoor-hides-inside-computer-chip/
This is the Department of Computer Science, University of MichiganTodd AustinProfessor,Matthew HicksIn a study by Mr. et al., The paper was published at the IEEE Security & Privacy Conference in 2016Recognition as a "remarkable paper"I received.
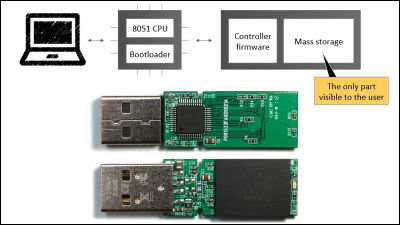
"Malicious hardware" specifically means "a processor with a hard backdoor that can not be blocked", which is built into the computer from the beginning.
In the first place, as the cost of chip design increased due to the use of smaller transistors, manufacturers frequently ordered chip design from overseas and third-party design makers to "malicious hardware" It is one cause of birth. The design maker who received the order performs a pre-manufacture check as to whether or not a problem-free design has been made, but if a malicious attacker enters this stage and places an unlikely order of attack trigger, the test device Can not be detected as "malicious hardware".
Also, the processor created in this mannerLogic gateIt is impossible to notice that it is "malicious hardware" even if you are using it because there is one extra added and it does not behave strangely at normal times. That difficulty is "to find a lurking needle from the hay of the hay".
ByTwechie
This "malicious hardware", for example, receives a trigger that is sent when accessing a site where a specific script is loaded on a PC, accumulates the electric charge in the capacitor in the logic gate, and outputs it when the threshold is exceeded It is structured. Since analog methods such as "how to take over the current through the transistor" are used here, Professor Austin and his colleagues use this hardware as an university Ann Arbor and an analog attack I hooked it and named it "A2".
According to Professor Austin, according to Professor Austin, this stage is already over when the output from A2 is done, and malware can get full access to the OS via the backdoor, it is already " Such a processor is made and it is operating in somewhere. " Indeed, professorsOR 1200 processorI made this backdoor and confirmed that I could attack.
Google engineer Yonatan Zunger who saw this paper said, "This is the most" smartly wise "computer security attack I have seen in the last few years."
This is the most demonically clever computer security attack I've seen in years.
https://plus.google.com/+YonatanZunger/posts/ayXVWrFpQus
Related Posts: