FBI warns about keylogger monitoring the input contents of wireless keyboard

ByRobbert van der Steeg
Cyber Task Force of FBI mimics a USB charger and warns that a keylogger that is stealing a wireless keyboard input content is installed.
Wireless Keystroke Logger Disguised as USB Device Charger Targets Wireless Keyboards - Private Industry Notification
(PDF file)https://www.americanbar.org/content/dam/aba/administrative/cyberalert/keysweeper.authcheckdam.pdf
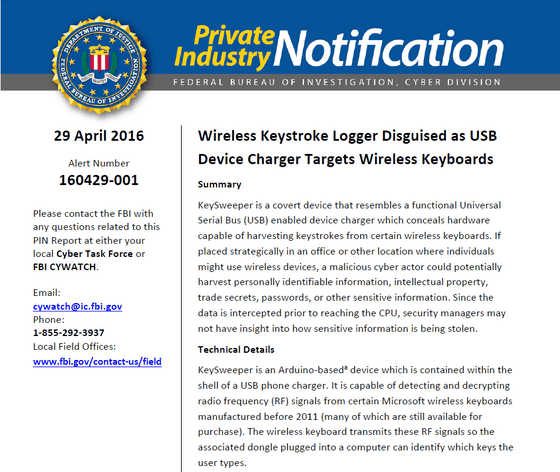
What I found is a terminal called "KeySweeper" that simulates the appearance of a USB charger to be plugged into an outlet, but the content is an Arduino-based keylogger (a tool to monitor and record the keystrokes on the keyboard).
This is a security expert and produced by a hacker, Samy Kamkar. In 2015 the existence was revealed.
"KeySweeper" disguised as a USB adapter and wiretapped the wireless keyboard

KeySweeper can detect and decode the wireless signal of the Microsoft made wireless keyboard manufactured before 2011. A communication module is built in, and when the website address etc. are input, the contents are sent as a text message somewhere. Also, if communication is not going well, we will accumulate data in the built-in flash memory. Also, even if pulled out from the outlet, it will continue to operate until the built-in lithium-ion battery runs out.
According to FBI, "Although not using a wireless keyboard" is cited as a countermeasure, according to Microsoft, the wireless keyboard using the 2.4 GHz band manufactured after 2011 is compatible with AES encryption technology and is damaged Nevertheless, I can also use the Bluetooth connection keyboard without problem.
Related Posts: