Malware "Viking Horde" bought in a popular ranked free game app on Google Play forms a botnet

Security countermeasure companyCheck Point, A malware that builds a huge botnet prevalent on Android terminals "Viking Horde"It is clear that the existence of. According to Check Point, Viking Horde has the possibility of affecting 50,000 to 100,000 Android smartphones.
Viking Horde: A New Type of Android Malware on Google Play | Check Point Blog
http://blog.checkpoint.com/2016/05/09/viking-horde-a-new-type-of-android-malware-on-google-play/
Viking Horde Infects Phones Via Google Play: Check Point | Stock News & Stock Market Analysis - IBD
http://www.investors.com/news/technology/viking-horde-malware-zombifies-phones-on-google-play-check-point/
Check Point is a huge infectedBotnetWe have discovered a new type of malware "Viking Horde" to build. A botnet is a network constructed by terminals infected with malware, which are controlled by cybercriminals without being aware of being built in the botnet and have a risk of participating in cyber attacks. Viking Horde's botnet is mainly used to disguise advertisement clicks and increase unreasonable profits.
The infection route of Viking Horde has already been specified. The biggest source of infection was that the game application "Viking Jump" uploaded to the Google Play Store on April 15, 2016. This application is a built game such as being the most popular as a free application, I know that it has already been downloaded 50,000 to 100,000 times.

Other applications that mediated Viking Horde are known, and the oldest application called WiFi Plus was published on March 29, 2016. Because this WiFi Plus requests root authority, it seems that there were users who thought suspiciously.
When launching the application that becomes the infection source of Viking Horde, install the components used for exchanging data among malware such as "core.bin" "android.bin" outside the application directory. Next, Viking Horde checks whether the terminal is rooted, and if it is rooted, it will arrange the communication protocol with the server and add a component to monitor the process. After that, it establishes a TCP connection with the command & control server (C & C server) and starts communication. Furthermore, I will establish a proxy connection that keeps anonymity.
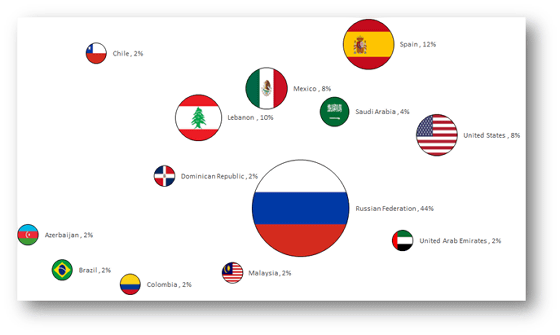
Check Point researchers are investigating the distribution of victims by Viking Horde based on data obtained from C & C servers managed by attackers who operate botnets. The most victims are Russia, followed by 44% of the total, followed by 12% Spain, 10% Lebanon, 8% America etc.
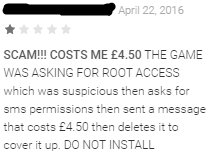
There is also a report that Viking Horde sent SMS saying "If you want to erase malware you pay 4.5 pounds (about 700 yen)" for app review. Check Point points out the possibility that Viking Horde can be used for various attacks such as DDoS attacks and spam delivery.
According to Check Point, Viking Horde has a function to reinstall without unnoticed by user even if it is uninstalled, and to install arbitrary program by downloading update program. Check point researcher Jeff Zakut said, "An attacker can turn on cameras and microphones of a terminal infected with Viking Horde and steal information from the terminal.When the root terminal infects Viking Horde, We should reset the hardware or otherwise replace it with a new smartphone. "
Related Posts: