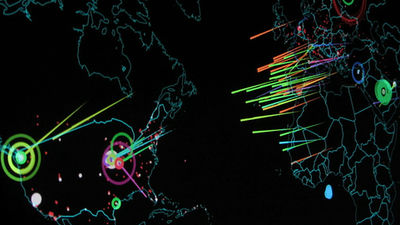
Existence of US electronic warfare plan ``NITRO ZEUS'' against Iran revealed
by Christiaan Colen
In 2010, the `` Staxnet '' worm used in a cyber attack targeting nuclear fuel facilities in Iran was used as a worm to attack air defense networks, communication systems, power grids, and other important facilities. It was revealed that it was part of an electronic warfare plan against Iran called ``. Since then, Stuxnet infection cases have been found outside of Iran, but this was an ``unexpected situation'' that could have exposed the plan, and the United States and Israel, who had been on a united front in this matter. It was also revealed that this was because the pace between the two was disrupted.
Exclusive: Israel's rash behavior blew operation to sabotage Iran's computers, US officials say - Middle East - Jerusalem Post
http://www.jpost.com/Middle-East/Iran/Israels-rash-behavior-blew-operation-to-sabotage-Irans-computers-US-officials-say-444970
US Had Cyberattack Plan if Iran Nuclear Dispute Led to Conflict - The New York Times
http://www.nytimes.com/2016/02/17/world/middleeast/us-had-cyberattack-planned-if-iran-nuclear-negotiations-failed.html
US Hacked Into Iran's Critical Civilian Infrastructure For Massive Cyberattack, New Film Claims - BuzzFeed News
http://www.buzzfeed.com/jamesball/us-hacked-into-irans-critical-civilian-infrastructure-for-ma
Massive US-planned cyberattack against Iran went well beyond Stuxnet | Ars Technica
http://arstechnica.com/tech-policy/2016/02/massive-us-planned-cyberattack-against-iran-went-well-beyond-stuxnet/
The shocking truth was revealed in the documentary film ` `Zero Days' ' by director Alex Gibney, which was shown at the 2016 Berlin International Film Festival. A number of new facts were revealed in interviews conducted with military and intelligence officials who appear in the main story.
The New York Times reported in 2012 that the evil worm ``Staxnet'' was created jointly by the American National Security Agency (NSA) and Israel's intelligence agency Unit 8200. The following year, in 2013, former NSA employee Edward Snowden acknowledged this fact when interviewed by the German weekly news magazine Der Spiegel.
Operation ``Nitro Zeus'' was a large-scale cyber attack plan to disrupt the activities of Iran's important infrastructure such as government, power plants, and power grids, and one of its components was ``Staxnet.'' This name was given by researchers, and it seems that the attacks using this worm were called Operation Olympic Games among those involved.
The program began in 2006 when President George W. Bush wanted to thwart Iran's nuclear program. According to Michael Hayden , who served as director of the NSA from 1999 to 2005 and director of the CIA from 2006 to 2009, President Bush did not want to leave the choice of ``to bomb or be bombed.'' , it was said that this was the result of thinking about whether there was any way to interfere with the nuclear facilities in Iran, especially the computers inside the facilities.
In the attack, a sophisticated replica of the uranium enrichment centrifuge at Natanz , Iran, was built at the National Laboratory in Oak Ridge, Tennessee, and Dimona , Israel, and Stuxnet was used to destroy its rotor. A test was conducted. The test was successful, and President Bush, who saw the destroyed rotor, approved the operation, and the cyber attack was finally carried out.
Cyberattacks have become even more aggressive under the Obama administration, but President Obama was worried that China and Russia would carry out cyberattacks like the one they were conducting against Iran. . However, the biggest fear was that Israel, led by Prime Minister Netanyahu and Defense Minister Barak , would take military action against Iran, and the United States would be dragged into a state of war.
In Israel, under pressure from Prime Minister Benjamin Netanyahu for results, the intelligence agency Mossad, with technical support from Unit 8200, modified Staxnet to more aggressive specifications. This improved version of Stuxnet was then mixed into products from two Taiwanese manufacturers that had business ties to Iran. As a result, approximately 8,400 uranium enrichment centrifuges at Natanz were rendered inoperable in September 2010.
However, due to the change in specifications, Stuxnet infections spread outside of Iran and were discovered by VirusBlokAda, a Belarusian antivirus software maker, in June 2010, just before the Natanz incident. If Israel had not taken this outrageous action, Stuxnet may have continued to operate as a worm that was only rampant in Iran and may have remained undetected.
In retaliation, Iran, which received a cyber attack by Stuxnet, improved its own attack tools and attacked 30,000 computers owned by Saudi oil company Aramco and American banks.
In the past, cyber-attacks were either carried out by skilled hackers (crackers) for their own entertainment or political purposes, by criminals for the purpose of fraud or theft, or by companies for the purpose of industrial espionage. However, the United States, Israel, and Iran are conducting cyber attacks against each other, and the world's first 'cyber war' between countries may have already begun.
Related Posts:
in Note, Posted by logc_nt







