Password is stolen by Trend Micro's password management tool Remotely operated vulnerability

Password management software included in Trend Micro's security countermeasure software "Password Manager"Urgent patch was distributed on 1 January 2016 and a compulsory update was done. This update addresses the vulnerability that Password Manager has, with Google's security team "Project ZeroIt was taken as a starting point that it was criticized as "unfamiliar stupid things" on the blog.
Issue 693 - google-security-research - TrendMicro node.js HTTP server listening on localhost can execute commands - Google Security Research - Google Project Hosting
https://code.google.com/p/google-security-research/issues/detail?id=693
Google security researcher excoriates TrendMicro for critical AV defects | Ars Technica
http://arstechnica.com/security/2016/01/google-security-researcher-excoriates-trendmicro-for-critical-av-defects/
Project Zero's Tabis · Ormandy discovered that there is a vulnerability in remote command execution of arbitrary commands in Password Manager, a password management software installed as a standard in Trend Micro security software.
According to Ormandy, Password Manager was mainly written in JavaScript using Node.js, and it was designed to wait after releasing multiple HTTP RPC ports in order to receive API requests, but " It took about 30 seconds to discover commands that can execute arbitrary commands called "openUrlInDefaultBrowser" mapped to ShellExecute ().
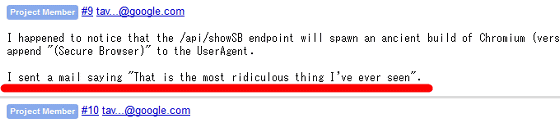
As a result of Mr. Orumandi reporting to Trend Micro about this vulnerability, Trend Micro immediately released an urgent patch, and it seems that he contacted Mr. Oremandy after the release. However, Mr. Oremandi checked that he was still able to find over 70 APIs with potential dangers that could still be executed code remotely. About the actual situation of Password Manager to be astonished Mr. Orumandi said that he told Trend Micro that it is "the most foolish thing I have ever seen".
In addition, Mr. Orumandi also succeeded in stealing passwords stored by the software about the security hole of Password Manager. In other words, "Password Manager" who entrusted the management of important passwords was a monkey, it was made by attackers to steal all passwords.
Mr. Orermandy who was astonished at making Password Manager too sloppy said in a blog "I do not know what to say, why not accept such a security check consultant, Is it provided as ... ... ".
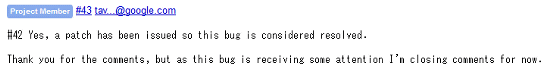
Trend Micro has already added a function to check the input destination of the command, created a whitelist that was not set up before, added "pwm.trendmicro.com" there, distributed patched patches , All Password Managers were forced to receive vulnerability-corrected updates. Despite being hurt by Mr. Ormandy, the bug seemed to have finally been resolved, and Mr. Orumandi who confirmed the situation closes the entry of the blog.
Related Posts: