A commentary on how anonymous communication "Tor" works
ByLa inventoría
Normally, when you access the website or send mail, the IP address of the access source remains on the server. Based on this, it is possible to specify "Who accessed the website?" And "Who sent the mail?", But it is possible to completely communicate anonymously without leaving any such information the system"Tor(Tora) "is. Security researcher's how Tor is operatingJordanExplained in an easy-to-understand manner.
How Tor Works: Part One - jordan-wright
http://jordan-wright.com/blog/2015/02/28/how-tor-works-part-one/
◆ History of Tor
Encrypted communication method which should also be said to be Tor's creator "Onion routingThe concept of "A proposalIt was in 1995 that it was done. this isOffice of Naval Research(ONR), which started development with the investment, in 1997National Defense Advanced Research Projects Bureau(DARPA) is also receiving assistance. Tor project is born in such a project led by the US government. Tor has so farMany sponsorsWe are continuing development while being supported by the 2015Donation from redditI am also receiving.
Tor related software is now widely known but in October 2003 it was released as open source software for the first time and it was the third one made as onion routing based software It was said that it was.
Briefly explaining the idea of onion routing, it is "to protect the data exchanged over the Internet and to hide the traffic with an encrypted layer to protect the anonymity of the sender and receiver".
◆ Basic information on Tor
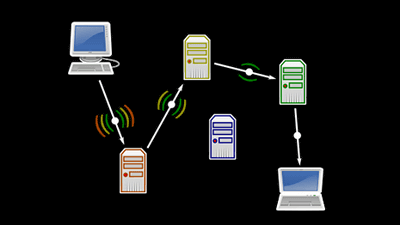
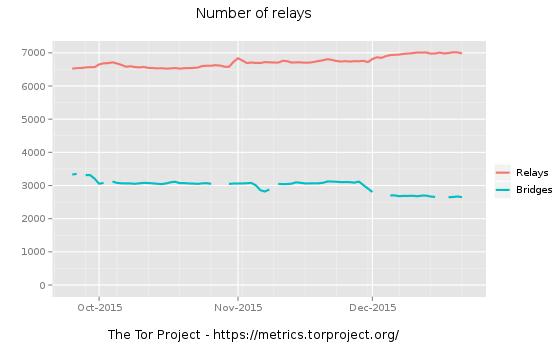
The mechanism of Tor is to add a relay point (relay agent) of another computer etc. to the communication route from the computer to the destination (for example, a web page such as google.com). In communication, many relays are made to go through, logs are not left in the relay, and all but the exit of the access route are encrypted, so the source is unknown and anonymity is maintained. In addition, currently Tor networkMore than 6000 relays existdoing.
"Relay" which is the key of Tor's anonymous communication exists all around the world, and its identity refers to the computer on which the relay function of Tor software operates. These are operated by volunteers who say "some bandwidth can be sacrificed", which means Tor network is preserved. Also, most relays are not running special hardware or software, it is only important to just operate Tor software.
Speaking of Tor communication speed and anonymity, the more the number of relays, the faster the speed, the more anonymity seems to be higher. In other words, when all the relays are combined, it becomes possible to use a large bandwidth, so the communication speed will be faster and the anonymity will also be higher as it will go around multiple points. So, if more relays exist and you can choose which to use, tracking a single user becomes more difficult.
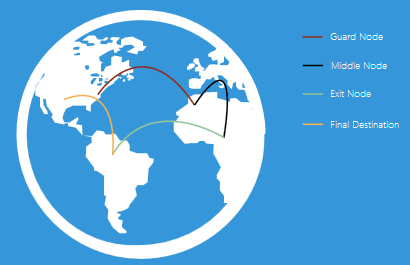
◆ Relay type
Tor is supposed to go through three relays by default. Each of these three relays has a specific role.
· Guard Relay (Guard Relay)
The relay at the entrance part of the Tor network is "Entry / Guard Relay". A relay that is stably shown as having a high band is selected as a guard relay.
Intermediate relay (Middle Relay)
"Intermediate relay" is a relay that relays traffic from the guard relay to the egress relay. By arranging this relay, it is making sure that the guard relay and the exit relay can not obtain mutual information.
· Exit relay (Exit Relay)
"Exit relay" is at the end of the Tor network and is the part which becomes the exit of communication as its name implies. The egress relay will send traffic to its final destination.
The following figure is a brief description of the route in the Tor network. The user (Client) arrives at the exit relay from the guard relay which becomes the entrance of the Tor network via the intermediate relay and arrives at the website etc. which becomes the final destination. Of course, this route is a combination of multiple relays, so it will be changed every certain time.
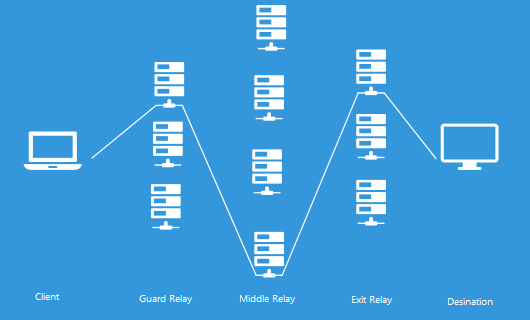
Generally, guard relays and intermediate relaysDigitalOceanYaEC 2likeVPSOr they are built on a shared server, all safe as server operators monitor for malicious encrypted communication. However, when exit relays are operated, special responsibility is applied separately from them. Since the exit relay sends the traffic directly to the destination, it communicates in an unencrypted state so you can see the contents of the communication. By this, it seems that exit relays are subject to attack in rare cases. So, the operator who operates the exit relay seems to have a particularly hard time.
◆ Why onion?
I understand how communication is done in the Tor network, but how can we know the reliability of these relays? "Tor is networked so as not to put trust in each relay," so it is encryption that makes it possible. From the viewpoint of higher level, what kind of encryption is done when users connect to Tor network is as follows.
1:
If the user uses Tor, the original data is encrypted. This encryption is decrypted at the egress relay.
2:
The data encrypted in step 1 is encrypted again. Only intermediate relays can decrypt the encryption of step 2.
3:
Finally, the doubly encrypted data is encrypted again. It is only the guard relay that can decipher this encryption.
That is, in Tor, the original data transmitted on the network is encrypted in triplicate, and each of the encryptions can be canceled by three in the communication route: guard, intermediate, and exit relays . Illustration of this encryption structure is as follows, and it is called "onion routing" because the figure that the layer of encryption covers the original data seems to be "onion".
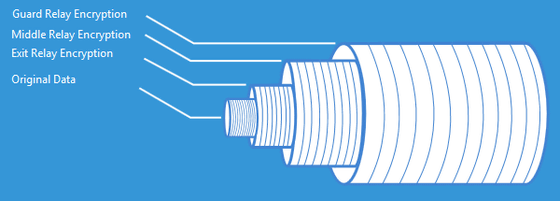
Therefore, each relay only has information about where encrypted data comes from and where it is sent. That's why "Tor is network designed so as not to put trust in each relay." This encryption network design is "beneficial for both users and relay operators," Jordan says. In other words, there is no worry that users can see the transmitted data from the user side, there is no way to view the data from the relay operation side, so it can not assume the responsibility for the data passed through the relay That's it.
In the exit relay, all encryption is released and original data can be seen, so if you pass the HTTP, FTP or other clear text protocol confidence you can check the contents of the data.
In addition, JordanDifference between relays and bridgesYaconsensusIt also explains.
Related Posts:
in Software, Posted by logu_ii