It turned out that Cisco routers had backdoors in at least four countries

ByLeonardo Rizzi
Computer network equipment development companyCisco(Cisco) switch hub productsThe network settings are resetAlthough the possibility has been clarified, this time a vulnerability on the system was discovered in a Cisco network router.
SYNful Knock - A Cisco router implant - Part I «Threat Research | FireEye Inc
https://www.fireeye.com/blog/threat-research/2015/09/synful_knock_-_acis.html
SYNful Knock: Detecting and Mitigating Cisco IOS Software Attacks
http://blogs.cisco.com/security/synful-knock
Cisco routers in at least 4 countries infected by highly stealthy backdoor | Ars Technica
http://arstechnica.com/security/2015/09/attackers-install-highly-stealthy-backdoors-in-cisco-routers/
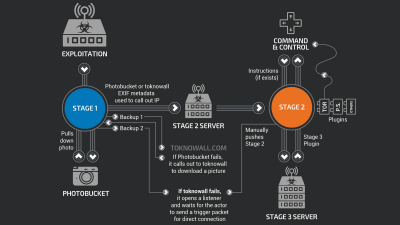
According to FireEye, a security-related company, the malware found was called "SYNful knock" and was found in 14 routers in total in four countries, Ukraine, the Philippines, Mexico and India. The infected routers are three models "Cisco 1841", "Cisco 2811" and "Cisco 3825". In addition, a back door has been constructed that permits an attacker to permanently enter the network, "If a SYNful knock is found in the network, there is a possibility that a backdoor is also set up, via the backdoor There is a high possibility that an attacker will also enter other networks and it is very dangerous, "says an investigator at FireEye.
According to Cisco 's announcement, SYNful knock is thought to widen the range of infection by using a machine whose router password has not been changed from initial setting, or an aircraft whose password is known in some way, With malware attacked routerROM MonitorAnd ROMMON firmware instead of operating.
The malware contains the IOS image of the Cisco router, allowing an attacker to read the modules used by anonymous users on the Internet. In addition, when infected with malware, a backdoor with password is built, and unlimited access to the router becomes possible. By using TCP packets sent to the router's interface, each module can be used via the HTTP protocol. Since TCP packets are special specifications and sequences are different and correspond to approval numbers, the modules appear independently in the IOS image of the router as executable codes and hooks, and by performing the same function as the backdoor password, It is a mechanism that makes it possible to access routers via console and Telnet.
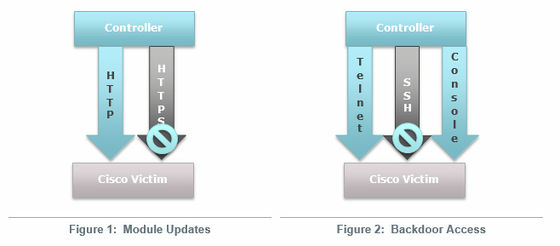
Article creation Currently, we do not know who owns the infected device or who the attacker is. Cisco has a way to detect if the router is infected with SYNful knockReleaseAlthough Cisco has occupied more than 30% of the routers that companies are using in JapanInvestigation resultThere is also considerable influence if Japan's domestic aircraft is infected with SYNful knock.
Related Posts: