Remote operation vulnerability on all Windows, an emergency update program "3079904" will be released
An urgent update was announced in almost all Windows OS. If it has not been updated, it means that code may be executed remotely.
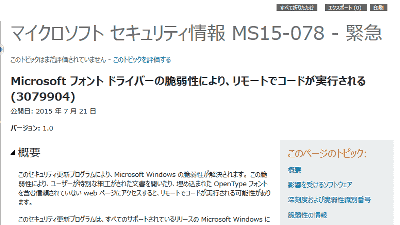
Microsoft Security Information MS 15 - 078 - emergency
https://technet.microsoft.com/library/security/MS15-078
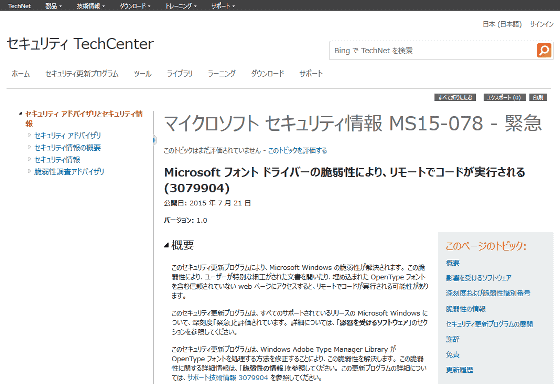
Vulnerability in Microsoft Font Driver Could Allow Remote Code Execution (3079904)
The contents of KB 3079904 are as follows.
Overall severity
emergency
The most serious vulnerability impact
Remote code execution
Necessity of restart
Restart may be necessary
Affected software
· Windows Vista
Windows Vista Service Pack 2
Windows Vista x64 Edition Service Pack 2
· Windows Server 2008
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for Itanium-based Systems Service Pack 2
· Windows 7
Windows 7 for 32-bit Systems Service Pack 1
Windows 7 for x64-based Systems Service Pack 1
· Windows Server 2008 R2
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for Itanium-based Systems Service Pack 1
· Windows 8 and Windows 8.1
Windows 8 for 32-bit Systems
Windows 8 for x64-based Systems
Windows 8.1 for 32-bit Systems
Windows 8.1 for x64-based Systems
· Windows Server 2012 and Windows Server 2012 R2
Windows Server 2012
Windows Server 2012 R2
· Windows RT and Windows RT 8.1
Windows RT
Windows RT 8.1
· Server Core installation option
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2012
Windows Server 2012 R2
It is necessary to update with most Windows OS.
Vulnerability information
If Windows Adobe Type Manager Library handles specially crafted OpenType fonts incorrectly, a remote code execution vulnerability occurs in Microsoft Windows. An attacker could exploit this vulnerability and fully control the affected computer. An attacker could then install programs, view, change, delete data, create new accounts with full user privileges.
There are several ways that an attacker can exploit this vulnerability, such as opening a specially crafted document to the user, or letting the user visit an untrusted web page containing the embedded OpenType font. This update addresses this vulnerability by modifying the way Windows Adobe Type Manager Library handles OpenType fonts.
Microsoft confirmed that this vulnerability was publicly announced when this security information was first published, but we did not receive any information indicating that the customer was being attacked. In Microsoft's analysis, it is evaluated that an exploit code is created and the attacker may stably exploit the vulnerability.
If you are using Windows OS, immediately download and install the update from Windows Update. In fact, when I tried installing on a PC with Windows 7, I had to restart my PC.
Related Posts:
in Software, Posted by darkhorse_log