Construction of "Quantized Internet" making eavesdropping completely impossible is ongoing in full swing

ByCarlos Lee
Government agencies such as the US National Security Agency (NSA) and the Federal Bureau of Investigation (FBI) in 2013 secretlyProblems that people were collecting information onIt became clear that the secrecy of the Internet became a big topic. The core of the technology that enhances the confidentiality of communication is encryption, but it is also called "ultimate encryption technology"Quantum InternetInitiatives towards the construction of "America and China are underway.
Building a globe - spanning quantum internet | The Verge
http://www.theverge.com/2014/11/18/7214483/quantum-networks-expand-across-three-continents
According to information leaked by Mr. Edward Snowden, former CIA official, the government agency "PRISMIt was discovered that eavesdropping of communication contents was carried out using a secret monitoring system called "The privacy problem of the Internet was deemed to be a big problem. Washington PostReported in October 2013According to the site, NSA connects between Yahoo and Google data centersPrivate networkIt was revealed that it had entered into and intercepted the data being sent and received.
In addition, Yahoo and Google at that time knows that communication between this data center was done without encrypting it. Both of them adopted correspondence to encrypt communication immediately, but as data communication itself is a mechanism that depends on existing infrastructure, in order to fundamentally solve the problem realize communication with a completely new mechanism It is required.

ByChristian Dembowski
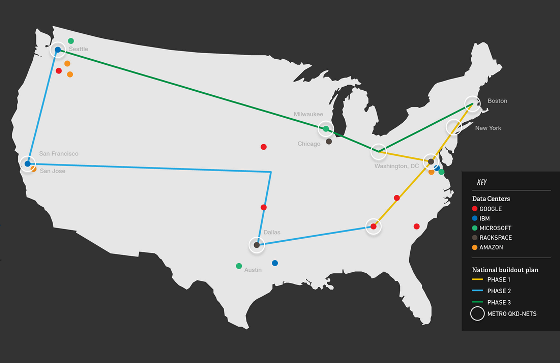
One year since the discovery of the problem, several organizations are working on realizing such a new communication method. He is an independent research institute in the United States, involved in various fields such as advanced materials, medical equipment, etc. from nuclear powerBatel Memorial InstituteAims to realize a route extending from the east coast Boston to the southeastern part of Georgia, and furthermore to the California on the west coast, with the construction of a network that crosses the United States in the "quantum internet" using quantum network technology I will.
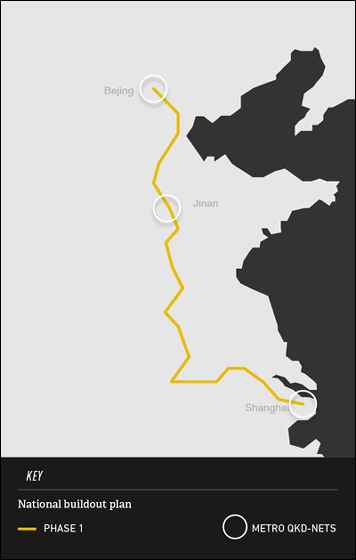
Furthermore, similar technology has already been introduced in China, and it is clear that the route from Shanghai to Beijing is tied by quantum internet.
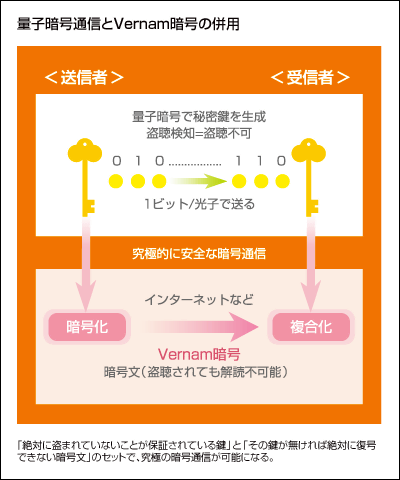
What is most important for the encryption technology currently widely used is that "Cryptographic keyHow do you deliver safely to your opponent? To analyze and decrypt the encryption key requires a very long time of thousands of years level if it is a general computer, but it is said to be very difficult to decipher, but for some reason the encryption key is in the process of communication If it is intercepted, all contents will be grasped by third parties. For this reason, although it can be said that the current encryption technology realizes a considerably high level of security, it can be said that the state of "completely safe" has not been reached.
In the technique of one quantum network, the state of photons (particles of light) is used for transmission of an encryption keyQuantum cryptographyIt is a big feature to use. The encrypted data itself is transmitted to the other party via the general Internet, but quantum encryption is used to generate the encryption key necessary for decrypting the encryption. This quantum cryptography is transmitted to the other party via optical fiber and used for decompression, but at that time, the quantum itself possessesQuantum duplication impossible theorem(The unobservability of quantum) will play an important role in the secrecy of cryptography.
ByTDK
If there is a person who intercepts a photon in the middle and eavesdropping is performed, photons received by the receiver will change from the original state, so eavesdropping by a third party was done in the middle of the route You can know that. In that case, it is a rough concept of quantum cryptography technology to discard cryptographic keys and enable safe information transmission by redoing communication again.

ByKevin Dooley
Existing cryptographic techniques have greatly increased the difficulty of deciphering to increase the decryption to the "virtual impossible state", but quantum cryptography makes it impossible in principle to intercept and decrypt cryptography It is regarded as the ultimate encryption technology because it is one. However, it is also fact that weak points still exist in such quantum cryptography.
In order to transmit quantum cryptography, it is necessary to connect two sites directly with an optical fiber cable, but with the current technology, "relay point" that refreshes the transmitted signal every 60 miles (about 97 km) There is a danger that it becomes the biggest attack point for eavesdroppers. Furthermore, even if the encryption between the two bases is perfected, since communication lines such as ordinary LANs are used from the data point transmitting and receiving data to the actual office, both sides of the communication are subject to the same risk It is also a fact that it is hiding. How to eliminate these problems seems to be an essential point for the realization of completely secure communication in the true sense.

ByEli Brody
In this way, the structure of quantum cryptography is a field where further development is desired in the future. As for the mechanism, it seems that you can understand well by referring to the following site.
The 71st secret key is put on light - the structure of quantum cryptography - | Tecnomy of science | TDK Techno Magazine
http://www.tdk.co.jp/techmag/knowledge/200706/index.htm
Nikon | The story of light and people | Encryption of unbreakable light ~ Quantum computers and quantum cryptography ~
http://www.nikon.co.jp/channel/light/chap04/sec01/index.htm
Related Posts:
in Web Service, Science, Posted by darkhorse_log