Discovery of the risk that the road signal system in town will be taken over via Wi-Fi

ByBristol RE 2007
In the Internet society where computers are connected by a networkHacking planes via in-flight Wi-FiThere is a possibility to be able to hack the TV's radio waves to attack the smart TV "Red button attackAlthough the risk of security such as the risk of inevitably increases, in the United States it is obvious that there is the danger that hacking the signal system of the road via Wi-Fi and there is a risk that the signal of the whole city can be freely manipulated became.
Researchers find it's terrifyingly easy to hack traffic lights | Ars Technica
http://arstechnica.com/security/2014/08/researchers-find-its-terrifyingly-easy-to-hack-traffic-lights/
(PDF file: 2.7 MB)Traffic-woot14.pdf
https://jhalderm.com/pub/papers/traffic-woot14.pdf
It became clear to the state of Michigan in the United States that the danger that the scene like a gang movie that "take over the signal and operate freely, help get the criminal who runs in the car and helps it guru" reality becomes reality Although it is a town that exists, details are not disclosed for security reasons.
The research team made publicreport(PDF: 2.7 MB), the security of the signaling system used in one city is very weak, and it has been clarified that it is possible to take over the system easily and in a short time. If this is done, it will be possible to control more than 100 signals over the city in a way that it can not be used as desired, and that method is also installed on ordinary notebook PCs It was amazing that it could be realized by using Wi - Fi being done.
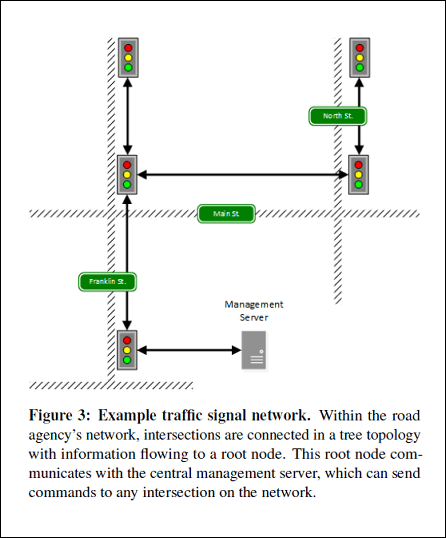
◆ Structure of signal system actually being operated
Upon verification, under the cooperation of the Michigan state authorities, the signaling system that existed in one city was used. The structure of the signal system isTree structure topologyThe signal emitted from the control center is first input to the first traffic light and the signal is distributed to the entire network connected to the first traffic light. The IP protocol is used for communication between devices (nodes), and all nodes are arranged on a single subnetwork. It is said that this mechanism is often used commonly in other areas as well.
And as a result of considering the cost on the installation side, wireless communication using radio waves is used for communication of each node, but this is one of the core problems.
◆ Low security of wireless communication
Two types of radio waves, 5.8 GHz band and 900 MHz band, are used for communication between nodes, and the best one is selected and used according to the difference in the surrounding environment. In the environment with a straight line of sight, the 5.8 GHz band with strong rectilinearity is used, and in the case of a node hidden behind the building shadow, radio waves of the 900 MHz band are used, but for communication in the 900 MHz bandFrequency hopping methodWas usedProprietaryProtocol, the protocol used in the 5.8 GHz band is found to be almost the same as the 802.11 n of the Wi-Fi standard also used in general homes It is.

ByMiguel Ángel
In fact, the investigation team succeeded in reading the SSID of each traffic signal using a very common notebook PC and smartphone. Entering the network of the system itself could not be done because of different protocols, but if that comes to mindreverse engineeringIt was possible to analyze the protocol by the method of. However, in order to escape the dishonesty of unauthorized access at the time of verification, the survey team seems to be connected to the system via the transceiver which is the same as that used for the actual signaling system and which is not available in general.
After trying this method, I succeeded in connecting to the network. And it turned out that no password or encryption was done for the communication in the 5.8 GHz band, and it became clear that it can easily enter the network easily if having the above transceiver.
◆ takeover of the system
When the connection passes, next time try to communicate with the control box which controls each signal. And this attempt will be easily cleared. In the control box, the embedded OSVxWorksVersion 5.5 was running, but this version was developed from the source code with the debugging port for testing. The investigation team succeeded in locating that this port is open at once. Then it was possible to touch the contents of the equipped memory and even reboot the device itself.
And, of course, it investigates the state of communication with each signal device and signal camera system. We were able to locate the details immediately, but the contents were not obfuscated, it was easy to grasp the contents and it was in a state where it was possible to take over. As for the actual situation, the investigation team analyzed the packet flowing in the network, as the communication was not encrypted, authentication was not necessary and it was easy to replace it with another one. It was easy to decipher if it was a person with the intention of attacking because the last byte was different only, "he said in the report that he was able to actually operate the traffic lights It is.

Successful "hijacking" with even one unit leads to being able to operate all moving devices with the same mechanism. If this is exploited, it makes it possible to make all traffic lights blue throughout the city, causing traffic to be greatly disturbed or, conversely, making all traffic lights red and causing heavy congestion. And, of course, you can manipulate the signal according to the car escaping like a gang movie, and also to control the traffic so as to prevent the pursuit of the pursuers.
◆ How to deal with problem solving and what is the real problem
Based on the above situation, the report presents countermeasures that can solve the problem. First of all, 5.8 GHz band communication is supported as a method for enhancing wireless communication securityWPA 2Advocacy of encryption advocated. While the 900 MHz band is supposed to have a high degree of security because general notebook PCs and smartphones are not compatible,WEPOrWPAIt is necessary to encrypt it. And advocate further multiplexing of security. We are requesting that a firewall be installed in the IP network used in the system to make it more stringent.
The surprising fact is revealed to the fact that the signaling system that protects the traffic safety is moving with such vulnerability, and the investigation team has asked the vendor who actually built the administration and the system to manage the system We are seeking urgent action. However, in the report, the word "according to the specifications of the industry standards, it is the standard itself that does not include the security point of view is the standard itself" as a response by the vendor, as an example, the sense of responsibility at each level The low level of security consciousness is the biggest problem.

ByEthan Prater
Related Posts: