It is mathematically found that simple password reuse is effective for security management

ByAlexljackson
In addition to using "123456" always contesting the top in dangerous password ranking, it is also possible to create complex passwords mixed in uppercase and lowercase letters in English and numbers and use the same password on multiple sites Password management is no longer impossible, such as no password management, but from the Microsoft laboratory, research on password management method that goes against the common sense of the world "easy password and worn-out password OK" has been announced.
(PDF) passwordPortfolios.pdf
http://research.microsoft.com/pubs/217510/passwordPortfolios.pdf
Mathematics makes strong case that "snoopy 2" can be just fine as a password | Ars Technica
http://arstechnica.com/security/2014/07/mathematics-makes-strong-case-that-snoopy2-can-be-just-fine-as-a-password/
Microsoft tells internet users that they are 'better off' reusing old passwords than creating new ones - News - Gadgets and Tech - The Independent
http://www.independent.co.uk/life-style/gadgets-and-tech/news/microsoft-tells-internet-users-that-they-are-better-off-reusing-old-passwords-than-creating-new-ones-9610324.html
Mr. Dinne Followschio and Coomac Haley of Microsoft Laboratories and Paul Oshot of Carlton University of Canada, in his published paper on the management of passwords necessary for using the Internet site, Although two points are required, "Passwords must be random and complicated (A1)" "Passwords can not be used on multiple sites (A2)", but practicing this is realistic It is pointed out that it is impossible.
In addition, although there are software and services that centrally manage passwords, there is a danger of receiving online attacks when managing on the cloud in order to effectively utilize password information on the Internet, and in the case of not being a cloud base It has a disadvantage that it takes time to set for each terminal, and it is still not practical.

ByCyberHades
As a result of being forced to manage these inexperienced passwords, the strategy adopted by many users is to relax the conditions of A1 or A2. In other words, loosening A2 to "use it on multiple sites that make complex passwords" or loosening A1 to prepare a different password for each site though it is a simple password, The possibility of hacking being damaged and the damage in that case is great.
Therefore, in research papers, we propose a method called "effective use of simple passwords" as a more practical password management method rather than forcing these "irrational games". In this method, we first select whether or not it is a highly sensitive site, and use a password that meets the conventional A1 · A2 only when judged to be sensitive. However, it is said that even if it is not so sensitive it is OK to use a worn out simple password.

ByVictor Bayon
For example, as for use in the online bank bank account information management screen, if hacking should be done in the unlikely event of hacking, you should use complex passwords specific to that site as before. However, if it is hacked such as the password for writing on the bulletin board, it is good that you can use a simple password for those that do not suffer much damage.
In this research, if you strive according to the usual password management method, the password management is often hindered, and in that case the probability of being damaged and the magnitude of the damage are the new management that allows "easy password use" It is mathematically calculated that it is larger than the damage caused by the method.
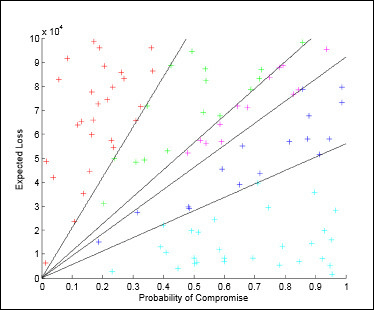
In other words, it is important to make a sharp tendency towards efforts in password management, and in many cases where the damage caused by password leakage is small, it is more risky and easier to allow people to use simple worn-out passwords It is accepted as a practical and effective password management method.
"Easy password reuse", which was traditionally dismissed as a proverbial thing, can be an effective tool to successfully balance the distribution that distinguishes important information from non-essential information and tries to respond accordingly It seems to be said that this research is quite suggestive.
Related Posts:
in Note, Posted by darkhorse_log