A hacker practices "Can you wiretaround a wireless keyboard?"

ByChristian Grunert
People who use wireless type keyboards hate dishonest cables on desktop PCs has increased very much. As wireless type keyboards transmit and receive the entered keys with wireless signals, the risk of eavesdropping on this signal and stealing the input contents has been pointed out before, Finnish self-name hacker said that the old type of radio I actually wiretapped the keyboard and published its contents on my blog.
Absorptions: Eavesdropping on a wireless keyboard
http://www.windytan.com/2013/03/eavesdropping-on-wireless-keyboard.html
Wireless keyboard often uses radio signals of frequency 2.4 GHz, but previously radio signals with lower frequency, longer wavelength were used. A Finnish lady hacker Räisänen got an old wireless keyboard at the auction and checked whether it could sniff the radio signal.
The winning bid keyboard is a wireless keyboard manufactured around the year 2000 called "iTouch" made by Logitech, using the frequency of 27 MHz band. Please note that this 27 MHz band was often used for wireless keyboard until mid 2000's.

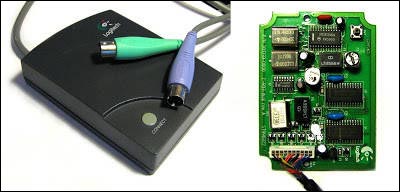
The picture below is a PS / 2 connection type receiver used in iTouch. You can see that it is a very large size compared to the current USB type dongle. Räisänen was disassembled and it was said that the Motorola FM receiver chip was loaded.
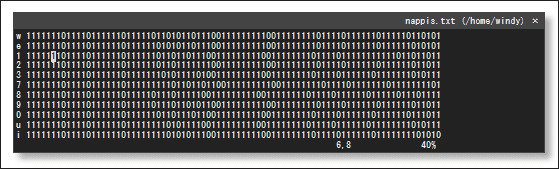
Räisänen analyzed that as soon as one key was pressed, about 85 bits of data were generated and none of them were encrypted at all. So, after mapping all key data ...
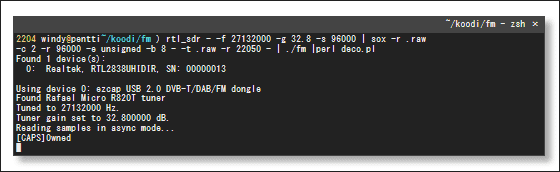
Reproducing the intercepted signal from the mapping seems to be able to reproduce the contents of the text entered by keyboard very easily.
Hacking to eavesdrop on the input contents of such a wireless keyboard is studied by a hacker who is familiar with the arm. The bottom movie is a hacking conference "DEFCON 17"This is a presentation on a method called" TEMPEST attack "that hacks wireless keyboard. TEMPEST Attack explains not only wiretapping but also hacking to send arbitrary text.
Defcon 17 - Sniff Keystrokes With Lasers / Voltmeters - Side Channel Attacks Using Optical Sampling - YouTube
Things that can suffer great damage if they are stolen from the input contents of the password. "If you use a wireless keyboard, you should also select what is not easily hacked by watching the wireless format," Räisänen says. In addition, Mr. Räisänen asked about the recommended keyboard in the question column gave a message "Logitech (Logicool in Japan)" which is AES encrypted "K 360I'm using an answer.
Related Posts: