A new crimeware "Atrax" for sending instructions via Tor to infected computers to digit Bitcoin

It is an anonymous communication systemTorSecretly usingC & C serverFromBotnetYou can send a command to the computer infected with virus, extract Bitcoin, extract data from the browser, can also launch DDoS attackClimeware"AtraxAppears, details of thisCSIS blogIt is open to the public.
CSIS: Why Crimekit Atrax will attract attention
https://www.csis.dk/en/csis/blog/4103/
Atrax Kit Boasts Tor Connectivity, Bitcoin Extraction | Threatpost | The First Stop For Security News
http://threatpost.com/new-exploit-kit-atrax-boasts-tor-connectivity-bitcoin-extraction/103027
Although Tor-based crimeware existed in the past, this new attention "Atrax" can be purchased as a crimeware kit, extracting browser data, mining Bitcoin,DDoS AttackIt is also possible to put on. The name Atrax seems to have been named from an Australian spider, and if you pay $ 250 (about 25,000 yen) it will be available at a relatively affordable price. Payment can be made only at Bitcoin.
Atrax has several add-ons available, including plugin stealer ($ 11,000), Bitcoin mining add-on for $ 140 (14,000 yen), form grabber (form robber) 300 dollars (about 30,000 yen), DDoS attack add-on will be available for $ 90 (about 9000 yen). With plugin stealer, it becomes possible to steal information from browsers such as Chrome, Firefox, Safari, Internet Explorer, Opera, etc. In the Bitcoin mining add-on, information is sent from Bitcoin's online wallet such as Armory · Bitcoin-Qt · Electrum · Multibit Stealing, mining Bitcoin, and evenLitecoinIt seems to be able to do similar things to. Also, Atrax has free updates and support.
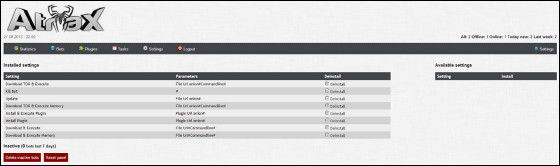
When extracting information from the infected computer it seems to be displayed like this.
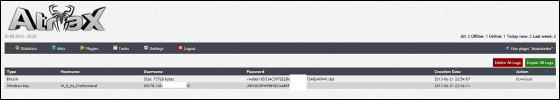
Since Atrax communicates with Tor, special encryption is not performed besides Tor, and the size of Atrax is 1.2 MB. Considering that the possibility that Bitcoin's information is stolen at low price is easily increased, users need to devise their own self-defense measures firmly.
Related Posts:
in Software, Posted by logu_ii






