1.2% of GooglePlay's applications turned out to be illegally copied "hijack apps"

By
Kristina Alexanderson Kalexanderson
It turned out that 1% or more of the applications published on Google Play are "hijack apps" which have been altered to copy maliciously other unauthorized applications.
1.2 Percent of Google Play Store is Thief-Ware, Study Shows | HOT forSecurity
http://www.hotforsecurity.com/blog/1-2-percent-of-google-play-store-is-thief-ware-study-shows-7340.html
Antivirus software companyBitdefenderHowever, as a result of investigating 424,666 applications on Google Play, it turned out that 5077 applications, which is about 1.2%, are hijack applications copying and tampering with other applications without permission. In the survey, in order to be recognized as a copied product, the library code that the developer is authorized to legally duplicate, such as advertisement SDK, of the two software codes is excluded It is said that 90% or more agreement is necessary for the part.
◆ Characteristics of hijack application
The creator of the hijack application will send the application already provided without permissionreverse engineeringAfter cloning it, duplicate it, make changes to the background color and icon design, etc., then offer it with Google Play credit. In Bitdefender's survey, there are also multiple Facebook and Twitter copy apps, exactly the same as the original app except for color and background designs, each downloading from 10,000 times to 50,000 times for users It is said that it is.
In addition, the hijack application sometimes re-releases it by incorporating its own module, and the functions that are arbitrarily added by the original module include the user's location tracking function (11.68%), the terminal information acquisition function (9.83%) Most of the functions such as connecting to Facebook and Twitter are disadvantageous to users.
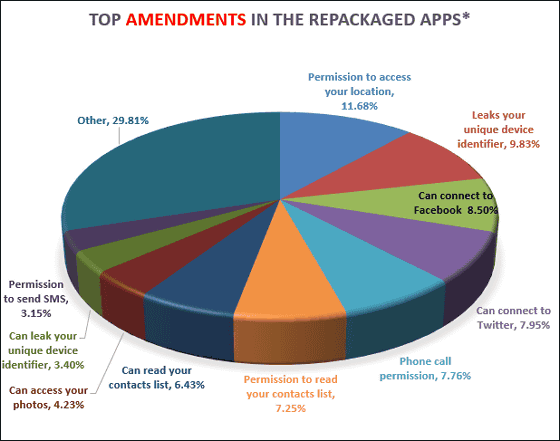
According to Bitdefender's survey, 7.76% of unauthorized tampering applications allow hijackers to make calls from users' mobile terminals, and 7.25% can steal their call logs. Some applications did not explicitly ask permission for this type of access.
In addition, many hijack apps incorporate the ability to positively display advertisements, and for advertisementsSDKBitdefender has announced that it is Airpush · Apperhand · InMobi · Leadbolt · Jumptap in descending order of use frequency.
◆ Structural problems of Android applications
Since the Android application is designed to be easily disassembled so that new functions can be added, it is relatively easy to reverse engineer an application and copy it without permission. It is much easier to duplicate and tamper with the application than to require a lot of expenses and time to develop the application from scratch, so it seems that such hijacking is unlikely.
Bitdefender, "Riptide GP 2As a result of investigating the download situation of about 3 dollars (250 yen in Japan) and 4 hijack apps, legitimate application developers found that from 3100 to 15,500 people I lost the user, and it became clear that the loss amount is 6,200 dollars (about 620,000 yen) to 31,000 dollars (about 3.1 million yen).
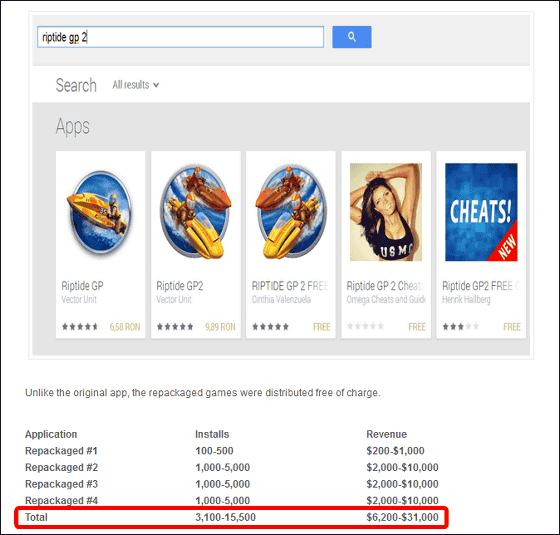
Freeride by such a hijacking act is an act of intercepting the legitimate interest to be obtained by creators who struggle to develop the application, and the motivation for the creator's development is eliminated and the appearance of an excellent application is suppressed It is concerned that it is not. Google Play prohibits the plagiarism of such an application and closing measures of accounts are done as soon as they are discovered, but hijacking does not decrease easily as it can easily make profits from legitimate application developers It seems.
·bonus
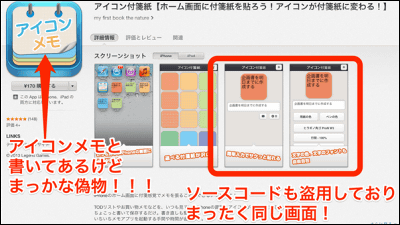
For iOS apps, developers are also making campaigns offering original apps for free for a limited time in order to "eradicate pakuri." We do not allow free rides! Although it is a hardship measure of the developer, although it is a hardship measure of the developer, providing the application free of charge also causes loss of opportunity, too, the damage suffered by the developer is also big and can not be a fundamental solution.
"Icon memo" which can be downloaded for free for a limited time, the reason is "to eradicate pakuri" - GIGAZINE
Related Posts:







