"HDCP used for copyright protection of HDMI and DVI is completely collapsed," experts point out

ByHome Cinema Pictures
Used for projector and display connection etc.DVI"Used for connecting digital home appliances"HDMI"HDCP copy guard format is used. However, this master key that encrypts HDCP was leaked as of September 2010, and Intel, the developer, also acknowledged that it was a master key.
Regardless of why the HDCP is still in use despite being a hacker living in London, a security related consultancy companyAperture LabsAdam Laurie says that he is managing his doubts on his blog.
Obviously a Major Malfunction ...: HDCP is dead. Long live HDCP. A peek into the curious world of HDMI copy protection ...
http://adamsblog.aperturelabs.com/2013/02/hdcp-is-dead-long-live-hdcp-peek-into.html
Laurie asserts that HDCP is not at the level of "slightly" and is breaking through at an unrecoverable level, and despite that, why just rent a movie on iTunes, "PC Does it comply with HDCP? "" Does the amplifier of the home theater compatible with HDCP? "" Is HDMI switcher compatible with HDCP? "Can not be understood.
"If something is broken, especially if it is related to security, at least it should try to replace it with something that works properly," Laurie is a wireless network security algorithmWEPHas been deciphered easily and is obsolete as an example.
In the cryptosystem, the most important thing is the "encryption key" used at the time of encryption, and protecting the encryption key should be given priority over that system within that system. However, as of 2001, it was pointed out that HDCP has weak points in this respect. The following PDF is from Scott Crosby of Carnegie Mellon University, Ian Goldberg of Zero Knowledge Systems, Robert Johnson of the University of California Berkeley, Dawn Song, and David Wagner.
A Cryptanalysis of the High-bandwidth Digital Content Protection System
(PDF file)http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.70.184&rep=rep1&type=pdf
Initially, HDCP is a mechanism developed by Intel, and device manufacturers are "reliable institutions"DCP (Digital Content Protection) LLCWe will license HDCP from the licensing organization. The license contains the public key (also called vA, KSV) and secret key (uA) for Device A. This means that for device B, it is vB and uB.
Devices A and B exchange vA and vB when communicating with each other. Calculations using uA and vB for device A and uB and vA for device B are performed so that the calculation results are the same based on confidential information in the key. This method is used for communication between devices (downstream), communication between HDCP-enabled devices on computers and software (upstream).
It is pointed out by Crosby et al. That there is a mistake in encryption design of HDCP here. Since the key generation is completely linear and the HDCP compliant device always opens the public key, the attacker can use 40 pairs of keys (public key And the secret key), it is possible to know what the master key (encryption key) is. This procedure is possible in a matter of seconds with the desktop PC, and the attacker can impersonate as an arbitrary terminal afterwards, and it is possible to generate a new key pair instead of "trusted institution" Become. In DCP LLC, leaked HDCP keys can be blacklisted, but an attacker can avoid this blacklist.

By(UB) Sean R
Mr. Crosby "We abandoned HDCP's cryptographic system and it is standardCryptographic primitives"It is well known that HDCP continues to be used even now. As a result, according to concerns of Crosby et al., In September 2010"Master key" which can create infinite key for HDCP leaksI have done it.
Nevertheless, it was thought that it is not easy to extract the key of a certain terminal, but Laurie says, "Is it possible to extract the key without destroying the device with only the knowledge gained from the nearest tool and the net Thinking "?", I actually tried it.
"HDMI screw terminal" produced by Laurie
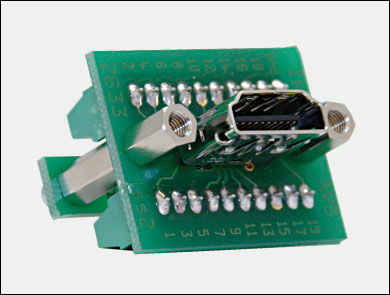
Insert one of the HDMI cables into this homebrew terminal, cut the other end with the terminal, expose the internal cable, and reconnect it so that each will form a loop. This completes the cable which is also expressed as "HDMI breakthrough cable" or "HDMI jailbroken cable". We will monitor the communication in the cable in real time with this.
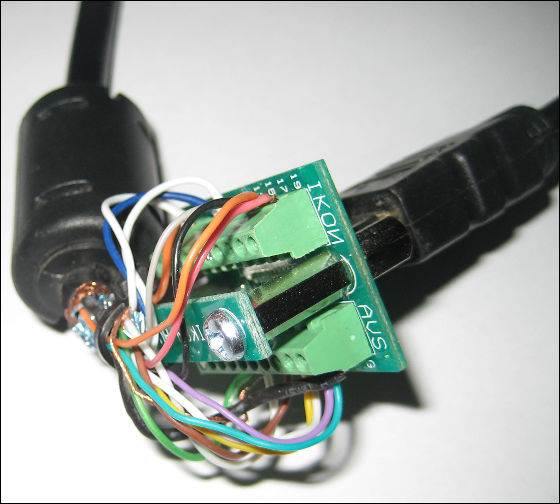
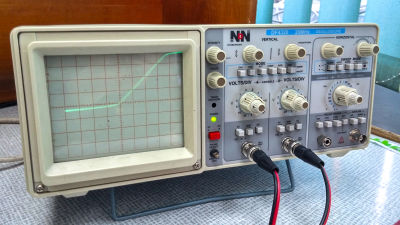
BelowI 2 COf the RAW data in the case of monitoring the communication of "
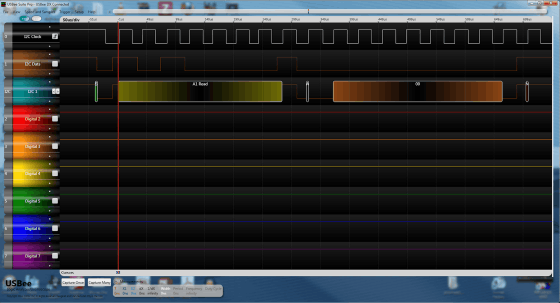
When you zoom out, you can see that the current part is only the beginning part of a long dialogue to the last.
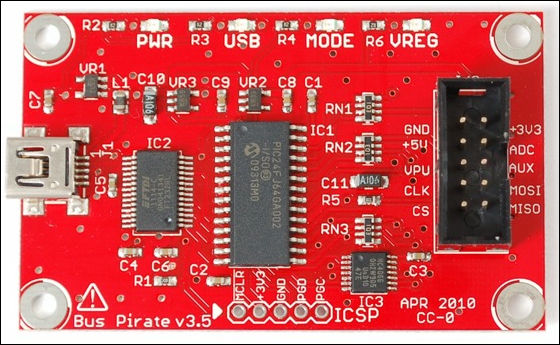
For this monitoring, "Bus Pirate"use.
By checking whether HDCP key exchange is done or not, it turned out that the packet is flowing faster than the corresponding speed of Bus Pirate. However, by hitting the latest firmware, Laurie was able to reach the situation where you can freely create the key as described above.
"That's why I said, HDCP is already collapsing," Laurie said. Some comments say that "This is a wonderful article" in the comment section, "HDCP is not abolished because not everyone can break the general public.HDCP is like a padlock attached to a store so,Bolt cutterThere is no comment to reply that there is not even one, but honesty people and the general public who does not bother to purposely lock out the locks can be kept away from the storeroom. "
As a matter of fact, Intel is taking a stance to consider legal measures in the event that a tool that breaks HDCP comes out,Automatic decryption tool of WEP is on sale for freeOn the other hand, because tools on HDCP are not on the market, it may be because Laurie's thought is too much ....
Related Posts:
in Note, Posted by logc_nt