"FinIntrusion Kit" which deciphers the wireless LAN in 2 minutes to 5 minutes and intercepts writing of e-mails and tweets etc.

It deciphers the passphrase of WEP (64 bits and 128 bits) of wireless LAN in 2 minutes to 5 minutes, monitors wired / wireless LAN communication encrypted by TLS / SSL, gets user name and password, gmail This "FinIntrusion Kit" is a set for breaking through webmail accounts such as Yahoo mail.
This is a new project by Wikileaks that allows companies searching for companies selling systems to monitor and tapping various people for the government, police, military and information agencies "The Spy Files"Gamma" which is one of the companies listed in the company, PDF files and movies for actual presentation are released.
The Spy Files - Tactical IT Intrusion Portfolio: FININTRUSION KIT
http://wikileaks.org/spyfiles/docs/gamma/288_tactical-it-intrusion-portfolio-finintrusion-kit.html
http://wikileaks.org/spyfiles/docs/gamma/300_tactical-it-intrusion-portfolio-finintrusion-kit.html
The main function of this product is as follows.
◆ FinIntrusion Kit

· Discover wireless LAN and Bluetooth
· Passphrase of WEP (64 bits and 128 bits) decoded in 2 to 5 minutes
· Breakthrough in WPA 1 and WPA 2 with dictionary attack
· Monitor wired / wireless LAN communication encrypted with TLS / SSL and get user name and password
· Impersonated as a wireless LAN access point
· Break through webmail account such as Gmail and Yahoo mail
This is a picture of the kit. High power wireless LAN adapter, high power Bluetooth adapter, 802.11 antenna for wireless LAN interception and so on.

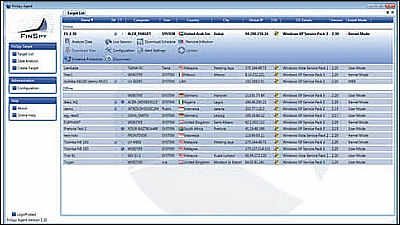
This is a screen of the software which makes it possible to automatically attack from the eavesdropped data
Software screen that fully monitors wireless LAN
A concrete example of what kind of situations you can actually use is shown in the movie

It is the stage that such a hotel

An agent with this kit kit came to the hotel lobby

Log in to the hotel's wireless LAN service

The red one visible in the upper left is the access point of the wireless LAN

I will access the wireless LAN covering the entire hotel

Then this kit gathers all the user names and passwords fully automatically, gets the contents of the mail transmission / reception of the target (all via the mail software as well as the webmail), and also various social networks such as Twitter · Facebook · mixi, blogs, forums etc. Record the write to.
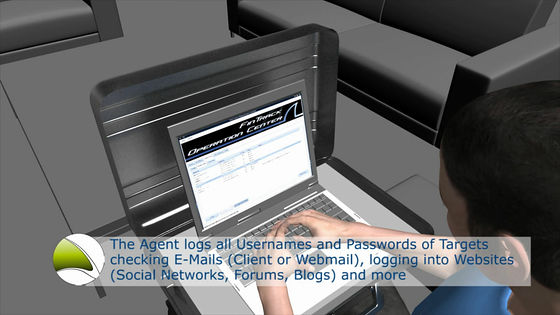
And police executives and others can use full accounts (user names and passwords) obtained from the data recorded in this manner to make full access to all targeted accounts.

Related Posts: