Criticism that the password management app 'LastPass' forcing users to change their master password is a shift of responsibility

LastPass, a password management service, sent a message to users urging them to update their master password to a ``long string of 12 characters or more''. LastPass says it is ``to improve security,'' but some experts have criticized LastPass's response as ``merely for performance and has no meaning in terms of security.''
LastPass breach: The significance of these password iterations | Almost Secure
LastPass: 'Horse Gone Barn Bolted' is Strong Password – Krebs on Security
https://krebsonsecurity.com/2023/09/lastpass-horse-gone-barn-bolted-is-strong-password/
Password management services such as LastPass require you to set up a 'master password' to access a password database. In 2018, LastPass added a restriction on the number of characters in the master password, stating that ``all new master passwords created in the future must be at least 12 characters.'' In September 2023, LastPass added a restriction on the number of characters in the master password. 'Force a master password update if
LastPass's enforcement of stronger master passwords comes after it was discovered in November 2022 that hackers had accessed LastPass customer data.
It turns out that a hacker accessed customer data using source code stolen from the password management application 'LastPass' - GIGAZINE
'Changing the length of your master password is not a response to customer data breaches that have already occurred; it is a way to better protect your online databases,' said Karim Touba, CEO of LastPass. 'This is to encourage users to adhere to LastPass's 2018 default setting of 12 characters or more.'
LastPass states that it does not store this master password, and emphasizes that if you lose your master password, it will be impossible to restore the database. However, experts say that if the database can be obtained in its entirety, all that is left to do is crack the password using brute force , and theoretically it will be possible to access the database.

Therefore, LastPass increases security by encrypting your master password multiple times. The more 'iterations' this encryption takes, the longer it will take to crack the master password.
According to Mr. Pallant, users who have been using LastPass for a long time said that the number of iterations was between 1 and 500. However, since 2013, the default number of user repetitions has been 5,000 times, which was increased to 100,100 times in February 2018, and further increased to 600,000 times in recent years.
Pallant calculates the time and cost of analysis based on the number of encryption iterations. When performing analysis on a single GPU, if the number of iterations is 1, it can be analyzed at a cost of only 17 hours and $ 15 (about 2,200 yen), and if it is repeated 500 times, it will cost 1 year and 7,500 dollars (about 1,100,000 yen). , 5000 times will require 10 years and 75,000 dollars (about 11 million yen), and 100,100 times will require 200 years and 1.5 million dollars (about 220 million yen). Therefore, it can be said that repeating the encryption greatly increases the security of the database.
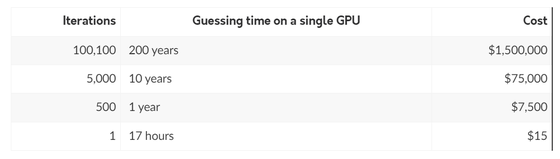
However, users affected by the 2022 customer data leak said that the encryption repeat settings on their accounts were never automatically upgraded. In other words, Pallant criticizes that long-time users were left with a low number of encryption iterations, making it less secure.
'LastPass made a big mistake by not forcing existing users to upgrade their encryption iteration count,' said Nicholas Weaver, a researcher at the International Computer Science Institute at the University of California, Berkeley. The user is not criticizing LastPass, but LastPass is criticizing the user, saying, ``You should have used a longer master password.''
Related Posts:
in Mobile, Software, Web Service, Security, Posted by log1i_yk