Pointed out that Apple's malware reporting tool can be 'easily' bypassed

Patrick Wardle, who has been researching Mac security for many years at the American hacker conference ``
An Apple malware-flagging tool is “trivially” easy to bypass | Ars Technica
https://arstechnica.com/security/2023/08/researcher-finds-easy-exploits-for-apples-malware-flagging-tool/
Since the core of malicious programs is software like web browsers and chat apps, there is no foolproof way to detect malware on your computer with 100% accuracy. This is because it can be difficult to distinguish between legitimate and non-genuine software. Therefore, manufacturers such as Microsoft and Apple that develop operating systems for computers, as well as third-party security tool developers, have developed malware detection mechanisms to detect the behavior of potentially malicious software. I am applying it to create a detection tool.
There are two types of malware: those designed to operate on the device for a short period of time and those designed to continue operating until the computer is restarted. Additionally, some are designed to remain on the target device even if the computer shuts down.
Many legitimate software require 'persistence' so that all your apps, data and settings remain intact every time you turn on your device. However, if software unexpectedly establishes 'persistence', it can be considered a sign of some kind of malice. Therefore, Apple has a background task manager as a malware detection tool, which seems to focus on monitoring the 'persistence' of software.

In October 2022, Apple announced that the Background Task Manager will 'send notifications directly to both users and third-party security tools running on the system when persistence events occur.' I have updated it to be able to. This allows us to notify you that your system may have been compromised when we detect unusual behavior (persistence events) in installed software.
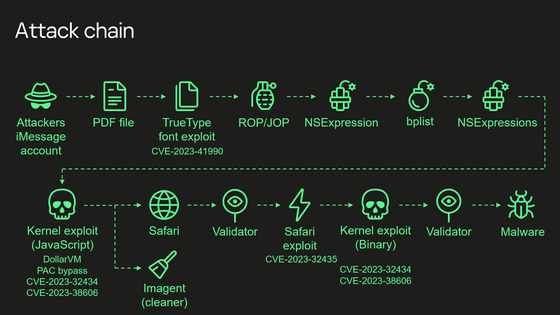
Regarding this background task manager upgrade, Wardle said, ``There should be a tool that notifies you when something becomes permanently self-installed. It's great, but it was so poorly implemented that moderately sophisticated malware could easily circumvent (bypass) this monitoring.'
As part of the activities of

One method Wardle discovered to bypass background task managers requires root privileges on the target device. This means that an attacker must gain full control of a target device before it can prevent it from receiving persistence alerts.
However, two methods have been discovered that do not require root privileges to disable persistent alerts that the background task manager is supposed to send to users and security tools. One relies on a bug in the way persistence alerts communicate with the kernel, and the other relies on a feature that allows even non-elevated users to put processes to sleep.
Wardle said he did not contact Apple about the bugs before announcing them at DEF CON. For this reason, Mr. Wardle explains that he has already notified Apple about the background task manager bug and has succeeded in improving the quality of this tool more comprehensively.
Related Posts: