Microsoft announces that AiTM phishing attacks that evade and hijack Office 365 accounts even by multi-factor authentication have targeted more than 10,000 organizations

Microsoft's security research team has announced that it has identified 'Adversary-in-the-Middle (AiTM),' a large-scale
From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud --Microsoft Security Blog
https://www.microsoft.com/security/blog/2022/07/12/from-cookie-theft-to-bec-attackers-use-aitm-phishing-sites-as-entry-point-to-further- financial-fraud /
According to the 2021 Microsoft Digital Defense Report , the number of reported phishing attacks that attempted to steal accounts and personal information by emailing fake sites doubled between 2019 and 2020. Therefore, it is recommended to use multi-factor authentication, which authenticates by combining not only password but also possession information and biometric information when logging in to an account.
In AiTM phishing, announced by Microsoft's security research team, attackers target emails containing malicious HTML attachments. This email disguises itself as a voice email notification, opens attachments, and redirects to a malicious Office 365 login page disguised by an attacker.
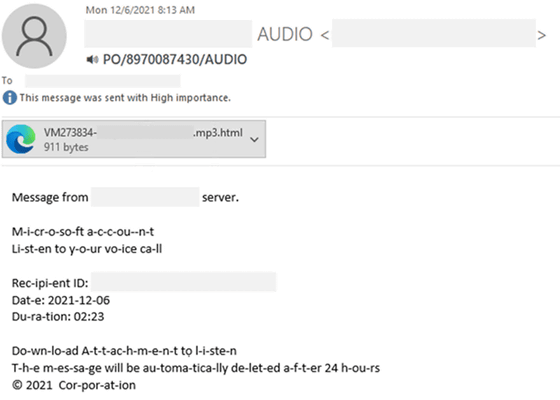
Opening malicious emails and following links is a common technique in phishing attacks, but in this AiTM phishing, the spoofed phishing website itself acts as a proxy and content from the legitimate Office 365 login page. The point is to acquire in real time. Phishing pages are HTTPS-enabled and hosted in a domain disguised as a genuine Microsoft service.
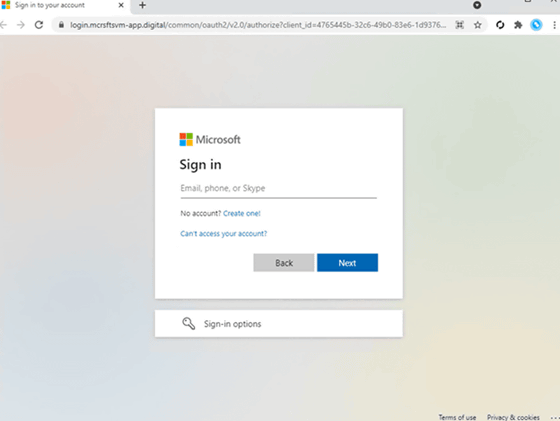
The attacker deploys HTTP packets from users accessing the spoofed site to a prepared proxy server. It looks like you are accessing a traditional site to the targeted user, but in reality, you are accessing a spoofed site and stealing data such as
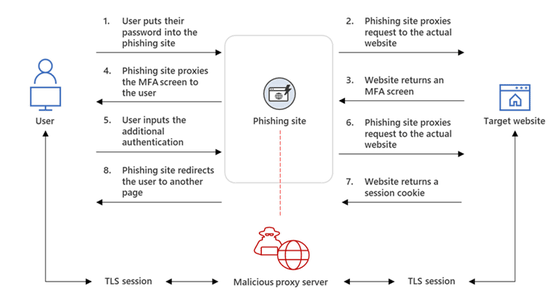
A session cookie is a server-issued cookie that allows an authenticated user to continue a session without having to re-authenticate with the website. According to Microsoft's security research team, after an actual compromised account signed in to a fraudulent site, there was evidence of successful authentication of Outlook Online using session cookies stolen by an attacker. doing. Normally, multi-factor authentication is required for Office 365 authentication, but by using authenticated session cookies, we avoided multi-factor authentication and realized unauthorized access. Open source phishing tools such as Evilginx2 , Modlishka , and Muraena were used for these AiTM phishing attacks.
However, not all multi-factor authentication is circumvented by AiTM phishing, and Microsoft states that FIDO2-compliant authentication methods that use biometric or physical security keys will not compromise session information. It is said that setting multi-factor authentication will increase the security against account theft.
We also enable conditional access policies for authentication, take advanced phishing measures to scan incoming emails and visited websites, and urge you to continuously monitor for suspicious activity and unusual sign-ins.
Related Posts:
in Web Service, Security, Posted by log1i_yk