Android malware 'Triada' has evolved to be incorporated into pre-shipped devices according to Google measures

by
On June 6, 2019, Google updated its Security Blog to summarize the malware ' Triada ' that infects Android devices. Triada was originally the type of malware that was infected by installation, but as Google strengthened its countermeasures against Triada, Google evolved Triada as it began to be incorporated as a firmware backdoor on Android devices before shipment. Describes
Google Online Security Blog: PHA Family Highlights: Triada
https://security.googleblog.com/20019/06/pha-family-highlights-triada.html
Android malware once found a way onto phones before they even shipped-The Verge
https://www.theverge.com/2019/6/6/18655755/google-android-malware-triada-ota-rom-ads-spam-oem
The original Triada, discovered in 2016, was Trojan horse malware, which installed malicious apps on infected Android devices and displayed spam advertisements. The Web browser has also been effective, and it has been attacked such as displaying an advertising banner that benefits Triada creators by overwriting the website URL.
Of course, Google can not continue to miss Triada, and uses Google Play Protect to take measures to remove Triada from all devices. Originally targeting the old Android device, Triada was thought that it became difficult to infect the Android device newly by this measure.

by
However, in July 2017, Google noticed that a new type of Triada was emerging. It seems that Triada, which used to infect Android devices and functioned as trojan-type malware, used to be a backdoor to firmware pre-installed on Android devices before shipment.
The key to solving the mystery of why Triada was able to invade Android devices before shipment is the firmware manufacturing process of manufacturers that manufacture Android devices. Many manufacturers try to incorporate features that are not included in the open source Android project, such as face recognition device unlocking, into their Android devices. As a result, the third party software vendor is asked to develop the desired function.
Google points out that this third-party vendor is the intermediary of the Triada attack, and is tricking the Triada code into the feature code asked of the manufacturer. According to Google's analysis, vendors using the 'Yehuo' or 'Blazefire' name have infected Android devices with Triada.
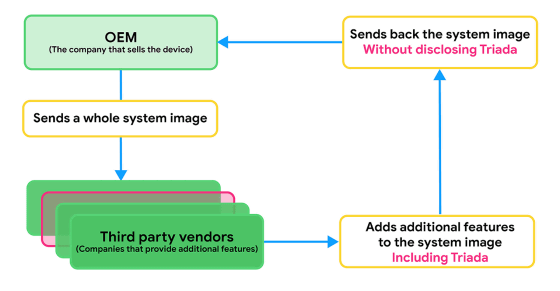
Google has worked with the affected manufacturers to provide system updates, remove Triada, and has also scanned other Android-like malware that is similar to Triada on all Android devices. Google argued that this example shows that developers of Android malware have skilled skills.
Google says that manufacturers that ask third-party vendors for software development should have a security review of all code to check if it has added anything but the functionality that it has requested.

Related Posts:







