It is possible that the fraudulent ad is playing back the video behind the scenes that the battery of the smartphone is decreasing quickly

by
If you're using a smartphone, you'll probably have more experience with having a lower battery level or more communication than you thought. Various factors are related to the remaining amount and traffic of the smartphone's battery, but it is new that the presence of 'Movie ad to be played behind the banner ad of the application' affects the remaining battery amount. It became clear in the survey.
An Ad Fraud Scheme Targeting Android Apps And Twitter's Ad Network Cost Advertisers Millions
https://www.buzzfeednews.com/article/craigsilverman/in-banner-video-ad-fraud
Video ad fraud has been draining phone batteries
https://mashable.com/article/video-ad-fraud-draining-phone-batteries/#j6XFwnss8gqm
We found that there was a large-scale fraudulent ad ( AdFlood ) from Protected Media and DoubleVerify of anti-adverse companies. A trick that two companies have revealed is to play a movie ad behind the image ad of the app. Fraudulent offenders, who appear to be advertising companies, bought cheap banner ad frames and played back movie ads behind the screen image adverts and to the user. Movie ads earn more than banner ads with small images. In this way, the user is not considered to have played the movie ad, but is considered as 'the movie has been played' and the revenue is increased.
This advertisement not only wastes the battery and traffic of the smartphone and causes the disadvantage for the user, but also for the app developer, the app behaves unintendedly and the ad revenue that can not be obtained can not be obtained. According to DoubleVerify's estimate, the scale of the damage is estimated to be $ 20 billion.

by
The following movie analyzes the app's banner ad using Google Chrome's developer tool, and loads the movie ad that has been hidden behind the banner of a fast food chain McDonald's or fashion brand Gucci You can see how you are doing. However, since movie posters restrict playback in embedded view, you need to browse directly on YouTube pages .
59jK66Ut8tY-YouTube
At first, McDonald's ad image which is often seen in the app's banner ad is displayed.
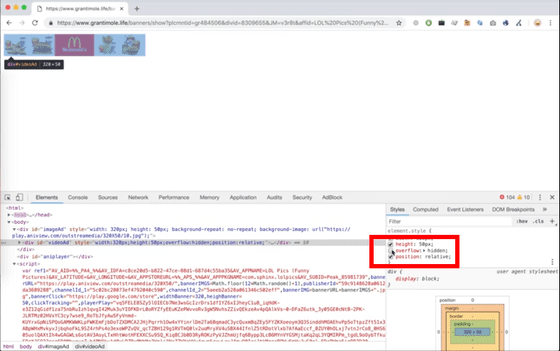
If you uncheck the 'overflow: hidden' check box on the developer tool console and turn off the hide setting ...
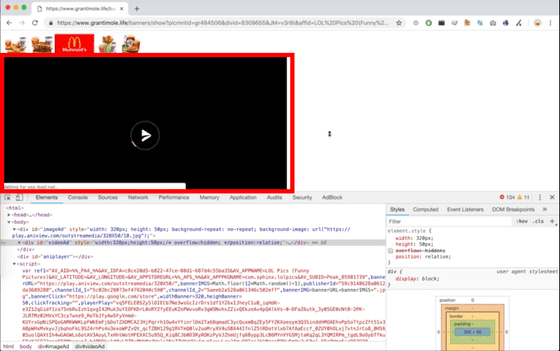
Something like a movie ad loading screen appears. The loading screen shows something like the
The ad hijacking mainly occurs on Twitter's MoPub platform, and Protect Media points out that an Israeli company specializing in movie ads is involved. Suspected Aniview denied direct involvement and announced that 'it has instructed subsidiaries and their clients who have created the banner ad code to comply with the guidelines.' However, it is discovered that the names of many employees have been deleted from the employees published on the Aniview homepage after that. Some of the employees removed from the list included employees who were core employees of a subsidiary who received guidance from Aniview.
The Protected Media has stated that advertising fraud has not started with the MoPub platform, and it is currently under investigation as of March 2019 as to when such fraud has occurred. It is also pointed out that this ad scam is unwilling to curb the occurrence of scams, as it generates some advertising revenue even for brokers and developers who are not involved in the scam at all.

Related Posts:







