Danger that can not be detected with security software by hiding malware on 'SGX' security mechanism of Intel CPU, program for proof of concept has been released

Intel has adopted the security mechanism "SGX (Software Guard Extensions)" which isolates and executes sensitive information from Skylake generation CPU so as not to be read by malicious persons. However, security experts point out that even security software can not detect threats by putting malware on SGX that creates "enclaves" that isolate data and execution processes within the CPU.
Practical Enclave Malware with Intel SGX
(PDF file) https://arxiv.org/pdf/1902.03256.pdf
Researchers hide malware in Intel SGX enclaves | ZDNet
https://www.zdnet.com/article/researchers-hide-malware-in-intel-sgx-enclaves/
Researchers Implant "Protected" Malware On Intel SGX Enclaves
https://thehackernews.com/2019/02/intel-sgx-malware-hacking.html
The following movie describes the security mechanism "Intel SGX" first adopted in the Intel 6th generation Core processor "Skylake" series.
Intel® Software Guard Extensions (SGX) | Intel Software - YouTube
With Intel SGX, it is possible to create an isolated space called "enclave" in the CPU, hold sensitive data in it and execute the processing. As a result, important data is not executed by OS or software, so data can not be read and security can be improved.
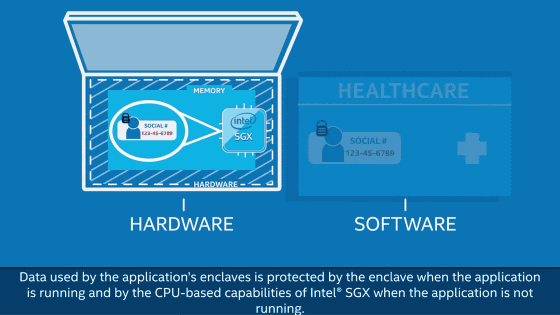
With SGX, the program can establish a protected enclave for code and data. Since enclave can not steal or tamper with programs on the system, safety is kept. In SGX, execution of malicious programs is prevented by permitting only processes with whitelisted signature keys.
On the other hand, research teams such as Samuel Weiser of the Technical University of Graz have succeeded in giving enclave access to a wider range of command sets than usual by utilizing return oriented programming (ROP) Thing.
A program for proof of concept has already been released on GitHub.
GitHub - sgxrop / sgxrop: The code to the SGX - ROP paper
https://github.com/sgxrop/sgxrop
According to researchers, it is theoretically impossible to detect malware etc with security countermeasures software etc. because it can not check inside because SGX confidentiality if you hide malware inside SGX's enclave. As SGX's confidentiality makes security check impossible, there seems to be a danger that SGX will be exploited as a great place to hide malware.
Related Posts: