A vulnerability 'Wavethrough' on media file calling in web browser can be found

Jake Archibold, a developer of Google Chrome (Developer Advocate) , has found a bug that allows web browsers to send unintended requests using behavior when reading audio and video files . The affected browsers are Firefox and Microsoft Edge, and both browsers have already finished their correspondence. Archibold named " Wavethrough " for this vulnerability.
I discovered a browser bug - JakeArchibald.com
https://jakearchibald.com/2018/i-discovered-a-browser-bug/
Google Developer Discovers a Critical Bug in Modern Web Browsers
https://thehackernews.com/2018/06/browser-cross-origin-vulnerability.html
According to Archbold, "Wavathrough" exists when a web browser handles cross-origin requests such as audio files and video files.
The current browser is designed to read only the data which is clear that security measures are strict and that it is the same as the loaded page and the source is the same. However, regarding reading audio files and video files placed in another domain, it was structured so that this restriction would not be applied.
In addition, in order to enhance convenience such as pause and resume when loading a huge media file, the browser has a mechanism that accepts only a part of the response. It can be said that it becomes one original resource if bundling responses.
Mr. Archbold discovered that by exploiting these two mechanisms, it is possible to mix malicious files that appear as media files among multiple responses and read them.
Demonstration images showing this with actual movement of the site are also released.
Firefox content-length hack - YouTube
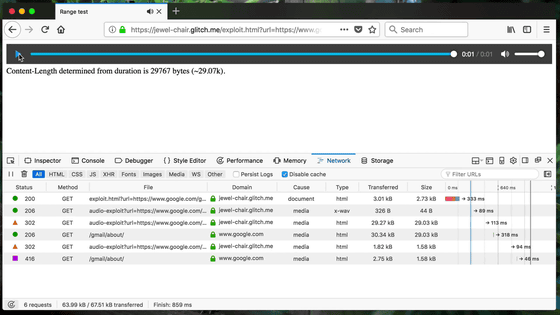
First we read the page "jewel-chair.glitch.me/exploit.html".
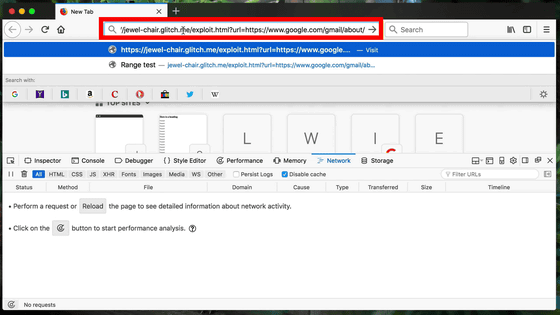
Since the audio file is embedded in this page, the corresponding WAV file (type field is x - wav) is loaded, but "google.com" which should be unrelated for some reason is displayed on lines 4 and 6 Appears on. These are transferred from the URL of the third line and the URL of the fifth line respectively.
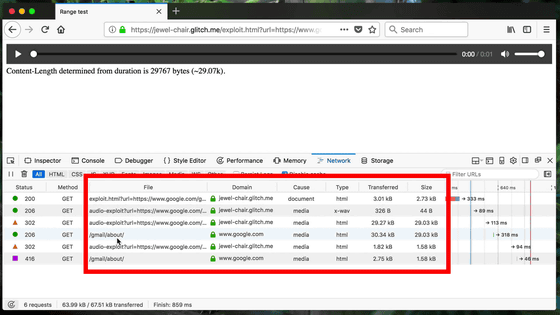
The size of the loaded file is written as "29767 bytes (29.07 KB)" in the notation on the page. Looking at the Size column, the size of the WAV file itself is 44 bytes, the rest is the fourth line, the transfer destination It was 29.03 KB from google.com which is.
According to Archbold, this type of forwarding process is already a policy to deny in Chrome and Safari, and it was Firefox and Edge that were affected. However, as Archbold got in touch, patches were applied, and both browsers have been compatible with the latest version.
Related Posts: