Malware "VPNFilter" malware infecting more than 500,000 network devices in 54 countries, suspected that the state is involved in the creation
CiscoIt is the security department ofTalosMore than 500,000 routers and NAS in 54 countries worldwide "VPN FilterWe reported that it is infected with malware called "malware." This malware has advanced functions such as "information gathering", "interference with communication", "cyber attack", etc. It is pointed out that the state may be involved in the creation of malware.
Cisco's Talos Intelligence Group Blog: New VPNFilter malware targets at least 500K networking devices worldwide
https://blog.talosintelligence.com/2018/05/VPNFilter.html
VPNFilter is a malware that infects devices such as Linksys, MikroTik, NETGEAR, TP-Link, Small office routers with Linux-based firmware and storage devices such as Internet connection. According to the survey, over 500,000 devices are infected by VPN Filter in 54 countries worldwide.
This VPN Filter has the following four functions, and it has features with very advanced functions.
· Ability to communicate with outside using Tor's anonymous network
· Ability to obtain authentication information of Web site
· It is one of industrial control systemsSCADAFunction to monitor
· Stop network equipmentKill switchFunction of
Talos analyzed the code of VPNFilter and found that there are many things in common with "BlackEnergy" which was used when Russia made a massive attack on Ukraine in the past, , It was confirmed that advanced implementation was applied. Therefore, Talos points out that there is a possibility that the state may be involved in the creation of malware.

Bythisisbossi
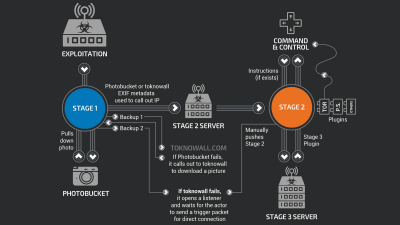
Among them, the biggest feature is that VPN Filter has three stages. In the first stage, after VPNFilter infects Linux-based firmware, it adds a setting to run itself to crontab which executes a specific command at regular time intervals. This will allow malware activity to be maintained even if the network equipment is restarted.
And at the second stage, collecting files and device information, adding a system kill switch and externalC & amp; C serverWe will install a function to accept and execute commands from.
In the final third stage, we monitor the network traffic and send authentication information of the acquired user to the outside using the Tor network, and the SCADAModbusWe have prepared a module to monitor protocols and prepare for attack at any time.
Although the infection route of VPN Filter is not specified, Talos is known to be vulnerable because it is confirmed that all the infected devices have known vulnerabilities in common. It is said that it will not be infected if it is.
However, Talos pointed out that even with this fact, it is difficult to suppress infection with malware. This is because the target device is directly connected to the Internet, applying an anti-malware tool or patch to this device may cause a network failure due to reduced throughput or unknown malfunction . For this reason, many technicians tend to avoid applying patches as much as possible while considering avoiding putting these network equipment as much as possible, and as many malware as normal malware countermeasures should not have problems with normal vulnerability countermeasures Talos says it has been infected.

ByDmitry Grigoriev
Therefore, in order to prevent the damage of VPN Filter, Talos recommends the following two correspondence to the equipment infected with VPN Filter.
· Reset equipment infected with VPN Filter to factory default state and delete malware of 2nd stage and 3rd stage
· Apply the latest patch
Related Posts: