Targeted attacks using the PC optimization tool "CCleaner" as a stepping stone reveal malware contamination routes
Bydownload.net.pl
From August to September 2017, an incident occurred in which target malware was distributed to large enterprises such as Intel, Microsoft, Sony and Fujitsu distributed with malware mixed in the PC optimization tool "CCleaner" Occurred. About this matter, Avast, a security-related company that acquired CClearner's developer, released the findings on April 17, 2018, and hackers used the remote login service "TeamViewer" to send them to the server five months before the incident I made it clear that I had made a backdoor by invading.
Recent findings from CCleaner APT investigation reveal that attackers entered the Piriform network via TeamViewer | Avast
https://blog.avast.com/update-ccleaner-attackers-entered-via-teamviewer
The first approach from the attacker was done at 5:00 am on March 11, 2017 in local time. This is 4 months ago when Avast bought CClearner's developer, "Piriform". Attackers intruded from TeamViewer into Piriform's internal workstation with a single sign-in. It means that the authentication at that time was done normally, which means that the attacker had obtained the correct authentication information beforehand.
According to the remaining not analysis of log files, the attacker for the PC, but tried the two types of installation of rogue DLL in TeamViewer via at 5 am running unattended state, there was no management authority 2 Degree failure. He said that he finally succeeded at the third try using VBScript.
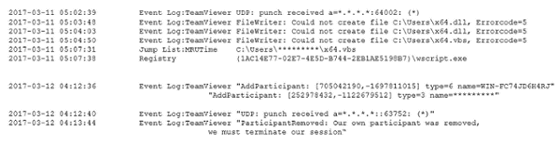
The next day, at 4 am on March 12, the attacker began to expand the range of invasion and succeeded in setting a backdoor to another PC via Microsoft 's Remote Desktop Service.
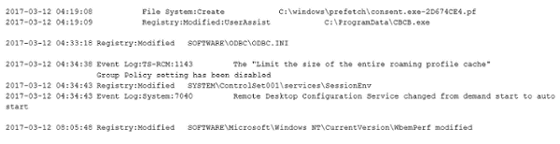
Furthermore, on March 14, I re-accessed the workstation that first penetrated and infected malware.
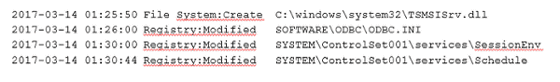
For several weeks thereafter, the attacker said there was no outstanding action, and Avast saw the attacker stealing information such as administrator authority from Piriform's internal system through the backdoor during this period. In addition, at this stage, to prepare for the attack of the next stage, we know that hacker had sneaked back door "ShadowPad" known as a cyber attack tool into internal company system.
An attacker who acquired various kinds of information and means in this way installed a ShadowPad that looked like an authorized "mscoree.dll" library to four computers including CCleaner's build server. At this stage the environment for executing attacks is in place, but on July 19th Piriform will be acquired by Avast with no attacks running. Later on August 2, CCleaner, the first version after the acquisition, was released. During this period, the attacker was waiting for all of the attacks, but in September we finally started attacking.
According to Avast, a similar attack using ShadowPad was executed in Korea and Russia before this one, and that the oldest ShadowPad was developed in 2014. As a matter of fact, the targeted attack using CCleaner is actually not a new one, it may have been an attack method deployed around 2014.
As a summary of the survey this time, Avast is in the process of M & amp; A (mergers / acquisitions)Due diligenceIn addition to investigating financial and legal aspects of the company, it is said that the same priority should be placed on cyber security and should be investigated. Also, in this attack, since malware was distributed on an authorized download server and it was "supply chain attack" against Piriform, the distributor, each company also carries out security measures for supply chains not only within the company itself We need it.
Related Posts:
in Security, Posted by darkhorse_log







