Intel announced that CPU will be released at the hardware level for vulnerability "Spectre" "Meltdown" in late 2018
Hardware design inherent vulnerability in CPU such as Intel "Specter"When"Meltdown"Can be a serious threat to security because it is impossible to respond completely by microcode correction. Intel announced that it is planning to release a newly designed CPU with hardware level countermeasures in the second half of 2018 to block the vulnerability of Specter · Meltdown.
Advancing Security at the Silicon Level | Intel Newsroom
https://newsroom.intel.com/editorials/advancing-security-silicon-level/
About Specter · Meltdown's newly designed CPU release, Intel made a presentation with Brian Kruzanich CEO's credit. By announcing by the CEO, it is evident how Intel emphasizes this problem.
The vulnerability of the problem is divided into three types of "Variant 1", "Variant 2", "Variant 3". Of these, Variant 1 and Variant 2 are known as Specter and Variant 3 is known as Meltdown. According to Kurzanicci, microcode updates have been released for all CPUs released in the past five years. It is important to keep the system up to date to prevent vulnerable attacks, Kruzanich said.
However, countermeasures on the software side are merely measures to mitigate risk, fundamentally it is essential to take measures at the hardware design level. So, Intel decided to release a newly designed CPU that implemented Variant 2 and Variant 3 vulnerability countermeasure in the second half of 2018. For hardware level measures, Intel has released a movie that explains Variant 2 as an example.
Understanding Specter and Meltdown - YouTube
Specter is classified as Variant 1 and Variant 2, and Meltdown is classified as Variant 3.

For both vulnerabilities, software updates have already been released, keeping the latest state is important as a basic vulnerability countermeasure.

Here, we will explain hardware level measures applied to the new CPU by taking Variant 2 as an example.

The key is the function called "Speculative Execution" which is mounted on the CPU.

In order to speed up the arithmetic processing, the CPU prepares in advance before the CPU actually requests tasks expected to be executed.
Speculative execution can be compared to "Scout (reconnaissance)".

Scout is like running ahead of the group of tasks and looking for a way (potential task processing).
By going ahead to the path (task) that may advance Scout in advance, it is possible to increase the performance as a whole by increasing the speed of the entire process.

Although Scout predicts tasks, we encounter "branches" where there is more than one possibility that a task can pass.

Here, someone with "Flag" will appear and instruct you to go through a specific road. In this case, Scout will proceed as instructed by Flag.

Specter Variant 2 is to control Flag through malware etc.

Scout guided by Flag may access personal information such as passcode.
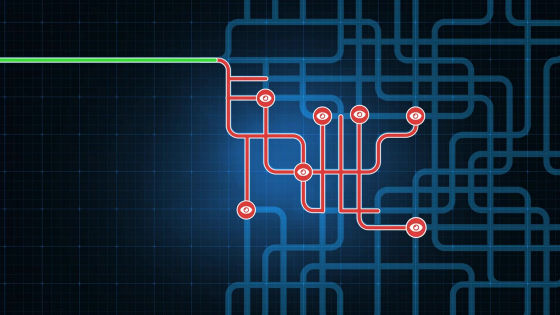
After all, Scout is aware that it is a wrong road, and we will re-search the way again, but the attacker has already collected personal information. There is a risk of highly confidential information leakage.

In order to countermeasure this vulnerability Variant 2 with hardware, Intel adds a new partition (barrier).

In the scene where a malicious person branches and instructs by Flag, Flag can be blocked by the newly provided barrier, and Scout's work will not be affected.

This partitioning prevents access to confidential information.
A newly designed CPU including Intel's partitioning function will be installed in the next Xeon Scalable processor known as the Intel 8th generation core processor and codename "Cascade Lake" and will be shipped from the second half of 2018. However, it is worth noting that Intel is still dealing with Specter Variant 1 with software updates, and it is not completely vulnerable.
Related Posts: