Tesla is hacked and the virtual currency is dug

It was revealed that Tesla hacked the cloud platform operated by Tesla for providing in-vehicle service, not only stolen Tesla's driving data, but also mining the virtual currency.
Lessons from the Cryptojacking Attack at Tesla
https://blog.redlock.io/cryptojacking-tesla
Tesla cloud resources are hacked to run cryptocurrency-mining malware | Ars Technica
https://arstechnica.com/information-technology/2018/02/tesla-cloud-resources-are-hacked-to-run-cryptocurrency-mining-malware/
RedLock, which provides cloud security services, has been investigating hacking damage to corporate cloud platform since 2017. Many companies are exploiting the management console of the Google design Kubernetes platform externally, and it seems that damages such as Aviva of the UK insurance company and Gemalto of the SIM card maker are confirmed so far.
RedLock security experts in January 2018 found that Tesla's Kubernetes console is not password protected and is accessible externally to Tesla's AWS credentials. In a certain Kubernetes pod, it was possible to view traveling data such as telemetry of Tesla cars.
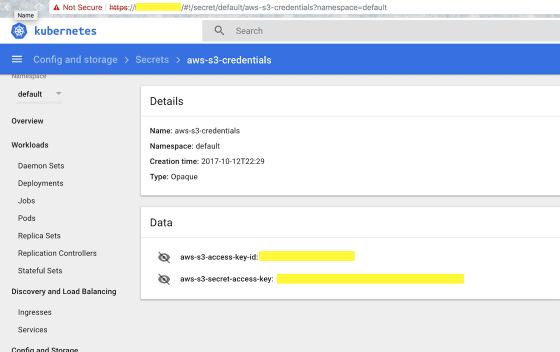
As a result of further investigation, it was discovered that a script for mining the virtual currency was embedded in Tesla's AWS. According to RedLock, Tesla's virtual currency mining hacking is similar to the attack method of Aviva and Gemalto, which had been confirmed to have been damaged by being able to minerize the virtual currency Monero, but there was a big difference.
First of all, it is said that unlike the virtual currency mining hacking so far, the attacker installed the mining software without using the published mining pool and was set to connect to the private or unlisted endpoint . By doing this, RedLock says that attack activities based on IP / domain threat information were less likely to be detected.

And the attacker hid the real IP address of the mining pool server via the free CDN service "Cloudflare". In addition, elaborate ingenuity that virtual mining hacking can not be found, such as mining software is likely to be mining with lower CPU utilization, using standard unsupported port It seems that it was given.
RedLock which confirmed hacking damage was immediately reported to Tesla and the problem was solved promptly. Tesla's public relations say, "Tesla has implemented a bug incentive program that encourages research on this type of vulnerability, and we addressed this vulnerability within hours as well, from the initial investigation, Is known to be limited to test cars used internally and there are no signs that customer privacy and vehicle safety or security are being compromised in any way. doing.
Related Posts:
in Software, Web Service, Ride, Security, Posted by darkhorse_log