A new PowerPoint attachment attack that infects malware "Tinba" stealing bank account information without macro execution is found
A hacking technique (Macro Malware) that steals bank account information by exploiting macro functions of Microsoft Office products such as Word had been raging a couple of years ago, but executing a PowerShell command from a newly attached PowerPoint file A hacking method to infect malware was discovered. This new hacking method has the feature that it is executed only by "moving the mouse cursor" without requesting an operation such as link clicking.
Beware! This Microsoft PowerPoint Hack Installs Malware Without Requiring Macros
http://thehackernews.com/2017/06/microsoft-powerpoint-malware.html
According to SentinelOne, a security countermeasure company, malware sent to a terminal by PowerShell included in a PowerPoint file is malware that steals bank account information that has been known for a long time under the name of "Zusy" or "Tinba (Tiny Banker)". The initial attack method was to open an attachment such as ".doc" extension, to install the malware by running the macro loaded in the document. However, since then, Microsoft has improved the Office software so as to issue a warning indication when a macro is included in the attached file, and in recent years the attack was bad.
However, the attack method discovered this time does not require work of opening a file and executing a macro. When opening a PowerPoint file attached to spam mail, a hyperlink "Loading ... Please Wait (loading, please wait a while)" will be displayed. At this time, even if the user does not click on the link, it will trigger just by moving the mouse cursor, and the PowerShell code will be executed. In addition, in Office 2013 and Office 2010, a warning indication is issued by the security protection function, but if you ignore this warning or click "Enable", malware will be installed.
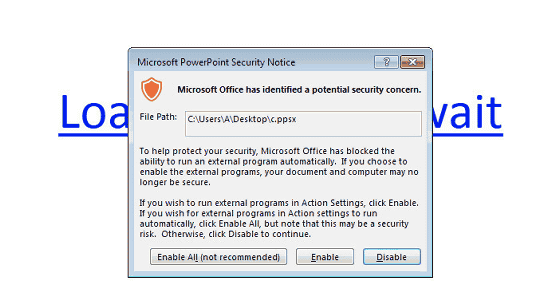
Sentinel One says, "Some users are using the macro malware blocking function, but there are lazy people who do not read the warning display impatiently," warns that malware damage can occur. Since it is said that PowerShell code will not be executed if you use the "PowerPoint Viewer" function that refuses program execution, so it seems safe to browse PowerPoint files with PowerPoint Viewer if you are wary of unauthorized installation of malware .
Related Posts: