It turned out that anyone had pretending to be President Donald Trump and a bug that pretending to be misrepresented existed on Twitter

Twitter has a "bug incentive system" that pays incentives to those who reported bugs or vulnerabilities depending on the severity of the content. Two engineers who declared bugs on Twitter and gained rewards made it public on the blog the contents of the bug and even if you do not know the password of others account, delete the images and movies you upload without permission It has become obvious that there were bugs that you can tweet freely on behalf of others.
How I took control of your Twitter account (tweeting, viewing / deleting photos and other media)
http://www.anandpraka.sh/2017/05/how-i-took-control-of-your-twitter.html
Publish tweets by any other user - Kedrisec security blog
http://kedrisec.com/twitter-publish-by-any-user/
Twitter Bug Allowed Hackers To Tweet From Any Account - Motherboard
https://motherboard.vice.com/en_us/article/twitter-bug-allowed-hackers-to-tweet-from-any-account
Twitter is a media submission form "Media StudioReleased in August 2016. On the day that this Media Studio was released, Anand Prakash, a technician participating in the Twitter bug reward program, checked the new service for vulnerabilities. And Prakash discovered that there was a loophole that you could tweet with someone else's account without knowing the password of another's Twitter account on that day.
According to Prakash, because the authorization check was not working, it was possible to tweet without accessing the password management screen by replacing the ID of the target Twitter account with the code of Studio. In fact, Mr. Prakash experiments with the consent of a friend, confirmed that he can mumble at a friend's account, delete pictures and images, and view images and movies uploaded with other accounts.
You can check how you tweet without permission by other people's accounts in the following movie.
Tweet from victim's account. - YouTube
It seems like deleting media files without permission from other people's tweets.
Delete media from victim's tweets - YouTube
Prakash said on August 29, 2016, the results reported vulnerability in Twitter, as soon as possible of the bug has been fixed. And Prakash Mr. has received the payment of bounties 5040 dollars (about 55 million) as consideration was reported discovered a bug from Twitter on September 3. It should be noted that, at the time that Mr. Prakash has discovered a vulnerability, Media Studio is for only part of the media that has been registered in advance was limited public which can be used, Twitter has reported that there was no damage that the account has been compromised .
However, in addition to Mr. Prakash, there are engineers who discovered Media Studio bugs. Security researcher'sKedr(Kedrisch) seems to have discovered a similar vulnerability to exploit the bug in Media Studio and manipulate other people's Twitter account. According to Kedrisch, after sharing the media file with the target user, it seems that we tweeted from another Twitter account by modifying the ID on the code when requesting a post.
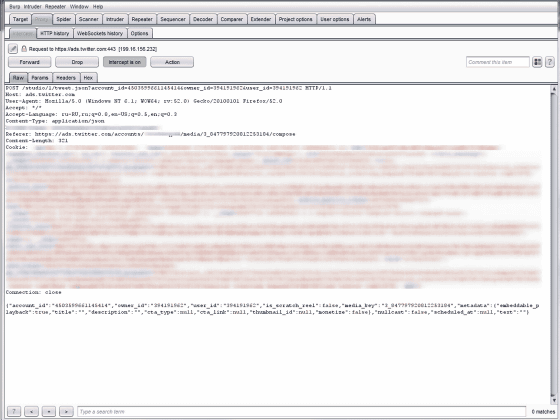
Kedrisch seems to have discovered this bug a few days after searching for vulnerabilities, and on February 25, 2017 it reports vulnerability to Twitter. Twitter fixed the bug after 3 days and Mr. Kedrisch received a reward of $ 7560 (about 830,000 yen).
Twitter does not disclose whether any damage has occurred due to a bug discovered by Mr. Kedrisch. However, if the bug was present from the service beginning, it will be several months it was possible to tweet pretending to be someone else. Among there are Twitter loves authorities such as the United States of Donald Trump President, since it could lead to a heavy important to give a political and economically significant impact if Tsubuyake without permission on behalf of the person, Twitter It seems that it can be said that it is a serious problem that can not be completed with a single word "mere bug".
Related Posts: