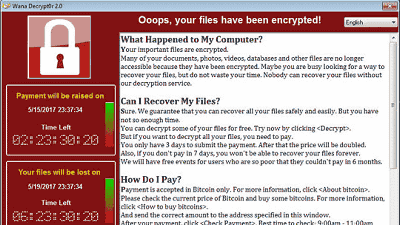
File encryption · ransom request "Wanna Cry" is a worldwide pandemic and enters an abnormal situation where urgent patch is distributed to Windows XP, current situation & countermeasure solution summary
Ransomu wearing a vulnerability in Windows "Wanna Cry"Continues to rage worldwide and Microsoft has distributed emergency security patches for old products such as Windows XP that have already discontinued security support. WannaCry has become a major epidemic worldwide as infectious terminals of medical institutions spread in the UK, and infection spreads even at Nissan / Renault manufacturing factories, and there is concern about the occurrence of damage in Japan.
Wanna Cry ransomware used in widespread attacks all over the world - Securelist
https://securelist.com/blog/incidents/78351/wannacry-ransomware-used-in-widespread-attacks-all-over-the-world/
Customer Guidance for Wanna Crypt attacks - MSRC
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Customer guidance on Ransomware WannaCrypt attack - Japan's security team
https://blogs.technet.microsoft.com/jpsecurity/2017/05/14/ransomware-wannacrypt-customer-guidance/
◆ What is WannaCry?
Ransomware wearing a worldwide popularity this time is a variant of malware called "Wanna Cryptor" and is named "Wanna Cry" "Wanna Crypt" "Wanna Cryptor" "Wanna Cryptor" "Wcry".
WannaCry is a vulnerability information inherent in the Windows OS that can be executed arbitrarily from the remote, published on March 15, 2017 "MS 17-010It infects by vulnerability "CVE - 2017 - 0144" published in "When infected, it encrypts the saved file and puts it in a state that it can not read the file. Furthermore, WannaCry makes file restoration difficult because it also deletes shadow copy at the same time as file encryption. On the desktop screen of the terminal infected with WannaCry and the file encrypted, you will see a warning screen prompting you to encrypt the file and prompt you to pay the ransom within the time limit if you want to decrypt the file.
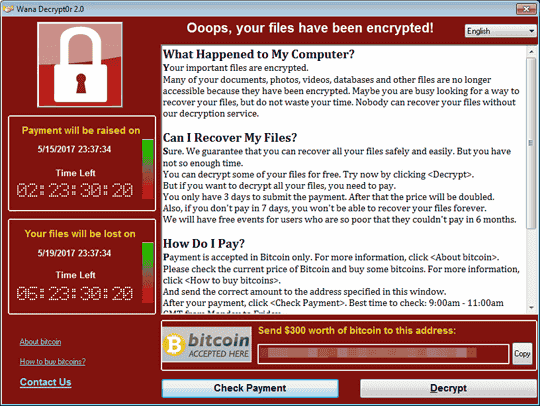
You can check how the file is encrypted by infecting WannaCry on Windows XP with the following verification movie.
WannaCry Ransomware Using Windows SMB Vulnerability - YouTube
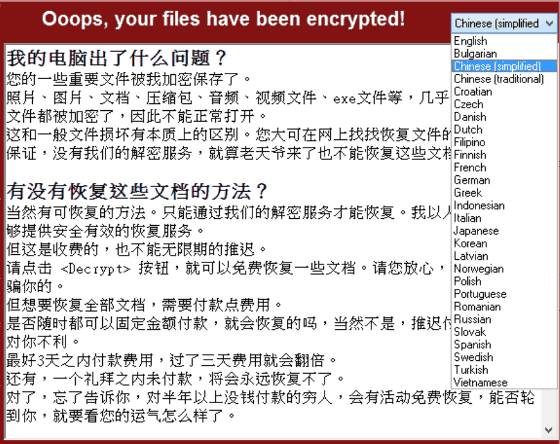
It seems that ransom claims carefully correspond to languages of various countries around the world.
The file to be encrypted has the extension ".der" ". Pfx" ". Key" ". Crt" ". Csr" ". P12" ". Pem" ". Odt" ". Ott" ". Sxw" .. Stw "". Uot "". 3 ds "". Max ". 3 dm". Ods ". Ots". Sxc ". Stc". Dif ".slk". Wb 2 ". Odp ".otp" ". Sxd" ". Std" ". Uop" ". Odg" ". Otg" ". Sxm" ". Mml" ". Lay" ". Lay6" ".asc" ".sqlite 3" " .sqlitedb "". Sql "" accdb "". Mdb ". Dbf". Odb ". Frm" .myd ".my .mib" .mdf ".ldf" .sln ".suo" ". Cpp" ". Pas" ".asm" ". Cmd" ". Bat" ". Ps1" ". Vbs" ". Dip" ". Dch" ". Sch" ".brd" " . Jsp "". Php "". Asp "". Java "". Jar "". Class "". Mp 3 "". Wav "". Swf "". Fla "". Wmv "". Mpg ". ".mpeg". "Asf" ". Avi" .mov ".mp4". 3gp ".mkv". 3g2 ".flv" .wma ".mid" .m3u " .m4u "." Djvu "". Svg "". Psd "". Nef "". Tiff "". Tif "". Cgm ". ".gif" ". Png" ". Bmp" ". Jpg" ". Jpeg" ". Vcd" ". Iso" ". Backup" ". Zip" ". Rar" ". Tgz" ". Tar" " . Bak "". Tbk ". Bz 2". PAQ ". ARC". Aes ". Gpg". Vmx ". Vmdk". Vdi ". Sldm". Sldx ". Sti ".sxi".. 602 ". Hwp".. Snt ". Onetoc 2". Dwg ". Pdf". Wk 1 ". Wks". 123 ". Rtf". Csv " .txt ". Vsdx". Vsd ". Edb" .eml ". Msg". Ost ". Pst". Potm ". Potx". Ppam ". Ppsx". Ppsm ".pps" ".pot" ". Pptm" ". Pptx" ". Ppt" ". Xltm" ". Xltx" ". Xlc" ". Xlm" ". Xlt" ". Xlw" ". Xlsb" " . Xlsm "". Xlsx "". Xls "". Dotx "". Dotm "". Dot "". Docm "". Docb "". Docx "". Doc " When encrypted, the file is changed to ".wncry" extension.

Contents of the ransom are mixed, but about 300 dollars (about 34,000 yen) can be deposited with bit coins. The deadline is 3 days. If there is no payment, the ransom will be doubled and the data will be deleted if there is no transfer within a week.
◆ Worldwide Damage
Initially it was Wanna Cry discovered as encrypted type Ransomuwari spreading by exploiting the URL of Dropbox, but in April 2017 the hacker group "Shadow Brokers" got related documents from the National Security Agency of America (NSA) It is thought that it is based on the stolen hacking tool.
Even though it has been confirmed, there are over 45,000 attacks in 74 countries. "More than 200,000 in at least 150 countries" that damage has spread all over the worldReport of the European Police AgencyThere is also.
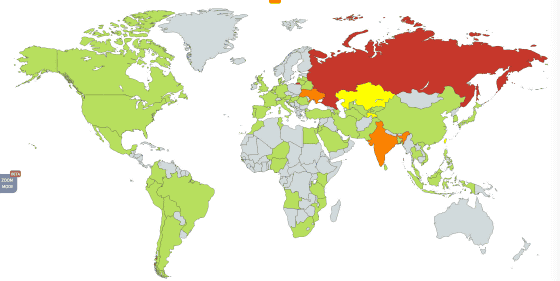
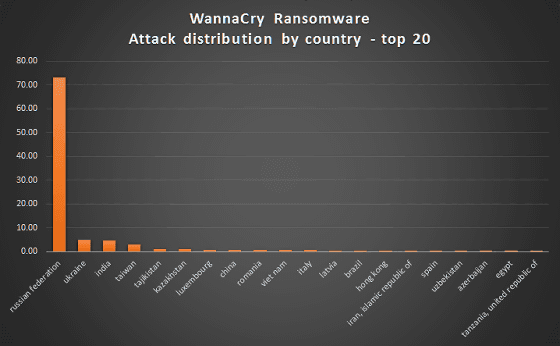
The top of attack damage in the first few hours by the Kaspersky Laboratory is in Russia. This will continue with Ukraine, India, Taiwan.
It is already confirmed that serious damage has been madeEngland, The system of national health system, national health service (NHS) suffered a massive attack, the reservation system of examination became ineffective, and the patient who was urgently carried was not accepted. Prime Minister Mei said, "Currently, the nation's Cyber Security Center and the hospital side are working together to maximize the power to protect the patient's safety while cooperating," the major damage has been confirmed.
In the middle of EnglandNissan Motor Factory in SunderlandYaRenault's subsidiary RevozDamage has been confirmed at the manufacturing site, such as the computer stopped the production line due to the damage of Wanna Cry. Inside Spain, Telefonica 's in - house PC is infected, German railway station' s electric bulletin board fails in Germany, and in Russia not only MegaFon, a leading telecom carrier but also the Interior MinistryRevealed that it was damaged by Wanna CryAnd the damage is expanding on a global scale.
However, on May 13, 2017, anonymous security experts have the role of a kill switch whose operation stops when the domain where malware attempts to connect is enabledDiscoveryThen, as a result of domain activation, it is known that infection spread pace is weakened. However, the fear of the evolutionary Wanna Cry appearing has not disappeared.
Sample I found scans SMB after dropping Wanna Crypt. Can anyone confirm it's the same thing? P2P spreading ransomware would be significant.Pic.twitter.com/zs5Td4ovvL
- MalwareTech (@MalwareTechBlog)May 12, 2017
Corrective measures
WannaCry knows that the infection from mail attachments and links is growing. For that reason, it is a major rule that you do not open the linked page of suspicious mail or do not carry out the attachment carelessly.
In addition, WannaCry has occurred on terminals that did not update security in Windows distributed in March 2017. For this reason, applying a security patch that obeys the vulnerability "CVE-2017-0144" is an effective countermeasure, and it is important to apply countermeasure patches promptly when measures are not taken. CVE-2017-0144 Countermeasure patch is available for each OS on the following page.
Microsoft Security Bulletin MS17-010 - Urgent
https://technet.microsoft.com/ja-jp/jp/library/security/ms17-010.aspx
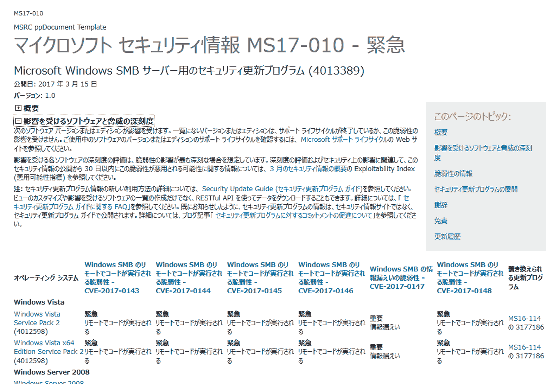
In light of the severity of the situation that the damage is occurring globally, Microsoft has also distributed security patches for old products such as Windows XP which have already ended their support. The link destination for each OS is as follows.
Security Update for Windows XP SP3 (KB 4012598) from Official Microsoft Download Center
Security Update for Windows XP SP2 for x64-Based Systems (KB 4012598)
Security Update for Windows XP SP3 for XPe (KB 4012598) - English
Security Update for Windows Server 2003 for x64-Based Systems (KB 4012598)
Security Update for Windows Server 2003 (KB 4012598)
Security Update for Windows 8 for x64-Based Systems (KB 4012598)
Security Update for Windows 8 (KB 4012598)
If concerns about stability of the system do not apply security patches, it is also important to first copy and save important files to the outside and save them.
In addition, Microsoft has also announced additional defense-in-depth measures taking into consideration the possibility that the attack method will evolve.
Customer guidance on Ransomware WannaCrypt attack - Japan's security team
https://blogs.technet.microsoft.com/jpsecurity/2017/05/14/ransomware-wannacrypt-customer-guidance/
◆ bonus
Microsoft 's Chief Legal Officer Brad Smith is posting a lesson from the Wanna Cry incident on the official blog.
The need for urgent collective action to keep people safe online: Lessons from last week's cyberattack - Microsoft on the Issues
https://blogs.microsoft.com/on-the-issues/2017/05/14/need-urgent-collective-action-keep-people-safe-online-lessons-last-weeks-cyberattack/
Among them, Microsoft distributed security patch in March of 2017, but said that the large scale damage of WannaCry this time highlighted the existence of unprotected terminals all over the world, We call for the importance of security update.
Also, WannaCry accuses that evils by government agencies will create damage on a global scale, from the fact that hacking tools developed by NSA were originally stolen by hackers. WikiLeaks wrote the CIA hacking method revealed by "Vault 7Since it is made public, the possibility of damage caused by "government-made" hacking is unlikely to continue to be zero in the future.
Related Posts: