"HummingBad" made in China that infects 85 million Android phones and makes 30 million yen a month

ByUncalno Tekno
Develop security related softwareCheck PointIs infected with about 85 million Android phones all over the world and makes a lot of money of 30 million yen per month by advertisement fraud Made in China "HummingBadIt is revealing the existence of.
From Humming Bad to Worse
(PDF)https://blog.checkpoint.com/wp-content/uploads/2016/07/HummingBad-Research-report_FINAL-62916.pdf
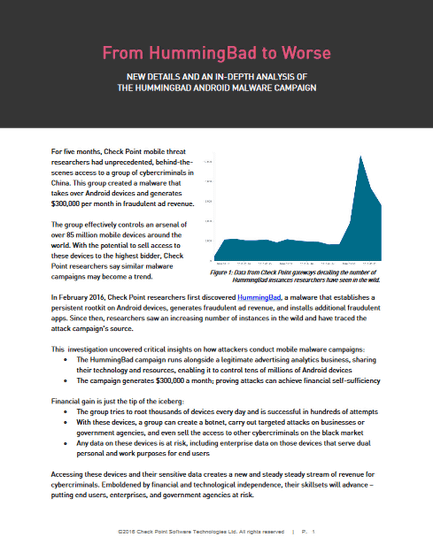
Check Point has been tracking phenomenal server crime that has been unprecedented so far from China for about five months. It is clear that this group has taken over Android terminals using malware, illegally increases the number of accesses to mobile advertisements, and earns 300 thousand dollars (about 30 million yen) in a month . It seems that the number of Android terminals that the cyber criminal group hijacked is over 85 million in the world, it seems that they operate funds efficiently and generate funds through advertisement fraud. Check Point's security analyst said, "These kinds of cyber crime may become popular in the future."
In February 2016, Check Point analysts encountered malware for the first time called "HummingBad". The malware is installed in the installed Android terminalRoot kitIt is likely to generate revenue by providing advertisement fraud or illegally installing the application. Since February, Check Point seems to have monitored malware distribution sources, and the number is explodingly increasing over time.
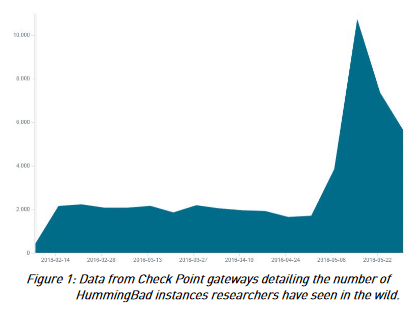
The transition of the number of malware "HummingBad" observed by Check Point is shown in the graph below. The horizontal axis shows time and the vertical axis shows the number of HummingBads observed.
According to Check Point, it not only infects tens of thousands of Android devices, makes money by advertisement fraud, but also creates botnets on infected terminals to attack companies and government agencies, It seems that they are selling tens of thousands of Android's accesses.
By analyzing HummingBad's command and control server, Check Point finds that the attacker's repository is a company called "Yingmob" that operates a mobile advertisement server in China. Together with information from other research organizations, this Yingmob company is the developer of malware targeted for iOS "Yispecter" and found to be also the developer of HummingBad. In addition, Yingmob has a development department in which a total of 25 employees belong to the four groups "Development Team for Overseas Platform", and Malware such as HummingBad is considered to have been developed by this department .
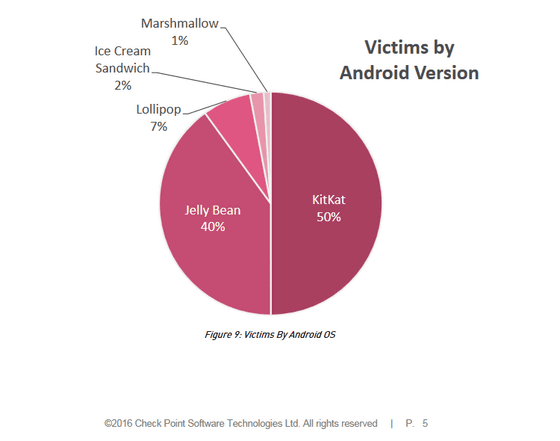
The breakdown of the Android terminal infected with HummingBad is as follows. About half of the 85 million units are Android 4.4 KitKat, 40% are Android 4.1 Jelly Bean, others, Android 5.0 Lollipop 7%, Android 4.0 Ice Cream Sandwich 2%, Android 6.0 Marshmallow 1%.
HummingBad creates a lot of money by abusing some advertisement server SDKs. HummingBad is targeting a variety of display advertisements and click advertisements for mobile advertisements. According to Check Point, HummingBad displays 20 million advertisements in one day and clicks 12.5% of them. Therefore, the number of clicks on advertisements per day is over 2.5 million. Because you earn $ 0.00125 (about 0.125 yen) per ad click, if you calculate from the number of clicks per day, you get more than $ 3000 (about 300,000 yen) from the ad clicks of the day.
In addition, HummingBad seems to perform 50,000 application installations per day, so you can earn $ 0.15 (about 15 yen) income by installing one application, so you can install $ 7500 ( About 750,000 yen) I earn over. By summing up these, you can infer that Yingmob has earned $ 10,000 a day (about 1 million yen) and 300,000 a month in one month. Also, Yingmob is planning a new business development using 85 million Android terminals infected with HummingBad.
Check Point says that "Yingmob is highly organized and may be the first criminal group to maintain independent profitability." Also, other cybercriminals adopt Yingmob's model and are concerned about the appearance of an outstanding criminal group of economic base.
Related Posts: