In Chrome 51 it was clear that 42 bugs were crushed and a total of 7.2 million yen of reward was paid
ByTsahi Levent-Levi
Version 51 stable version, which is the latest version of Google's web browser "Google Chrome" which is repeatedly updated on a regular basis, has been released on May 25, 2016. Google made 42 bugfixes for this version's release, 23 of which received reports from external collaborators, and the rewards (rewards) paid at that time total It has reached 65,000 dollars (about 7.2 million yen), and I know that about the same person received the same person.
Chrome Releases: Stable updates
http://googlechromereleases.blogspot.jp/search/label/Stable%20updates
Google pays $ 65k to shutter 23 Chrome bugs • The Register
http://www.theregister.co.uk/2016/05/30/google_pays_65k_to_shutter_23_chrome_bugs/
In developing software, we are recruiting bugs from external investigators, and we are implementing a program that pays incentives according to the contents of the bugs we have found. Nine of the 23 external reminders received regarding the version 51 stable issue have security holes with a high risk, followed by 10 in middle and 4 in low risk of bugs It was revealed that it was.
In the blog, details of the bug that was fixed, the amount of the reward, and the name of the collaborator are listed, but it is about 30 thousand dollars (about 330 dollars), which is about half of the actual reimbursement of 65,000 dollars Ten thousand yen) was also paid to the person called Mariusz Mlynski. He has reported 4 security holes with high risk and received payment of 7,500 dollars (about 830,000 yen) per case.
Following this is Rob Wu and Guang Gong, who both have $ 8,500 and $ 4,000 (about 440,000 yen) respectively.
In the blog, the contents of the bug, the name of the reporter, and the amount of the reward are listed as follows.
[$ 7500] [590118] High CVE-2016-1672: Cross-origin bypass in extension bindings. Credit to Mariusz Mlynski.
[$ 7500] [597532] High CVE-2016-1673: Cross-origin bypass in Blink. Credit to Mariusz Mlynski.
[$ 7500] [598165] High CVE-2016-1674: Cross-origin bypass in extensions. Credit to Mariusz Mlynski.
[$ 7500] [600182] High CVE - 2016 - 1675: Cross - origin bypass in Blink. Credit to Mariusz Mlynski.
[$ 7500] [604901] High CVE-2016-1676: Cross-origin bypass in extension bindings. Credit to Rob Wu.
[$ 4000] [602970] Medium CVE - 2016 - 1677: Type confusion in V8. Credit to Guang Gong of Qihoo 360.
[$ 3500] [595259] High CVE - 2016 - 1678: Heap overflow in V8. Credit to Christian Holler.
[$ 3500] [606390] High CVE - 2016 - 1679: Heap use - after - free in V8 bindings. Credit to Rob Wu.
Credit to Atte Kettunen of OUSPG.
[$ 3000] [613160] High CVE-2016-1681: Heap overflow in PDFium. Credit to Aleksandar Nikolic of Cisco Talos.
[$ 1000] [579801] Medium CVE-2016-1682: CSP bypass for ServiceWorker. Credit to KingstonTime.
[$ 1000] [583156] Medium CVE - 2016 - 1683: Out - of - bounds access in libxslt. Credit to Nicolas Gregoire.
[$ 1000] [583171] Medium CVE-2016-1684: Integer overflow in libxslt. Credit to Nicolas Gregoire.
[$ 1000] [601362] Medium CVE-2016-1685: Out-of-bounds read in PDFium. Credit to Ke Liu of Tencent's Xuanwu LAB.
[$ 1000] [603518] Medium CVE-2016-1686: Out-of-bounds read in PDFium. Credit to Ke Liu of Tencent's Xuanwu LAB.
[$ 1000] [603748] Medium CVE-2016-1687: Information leak in extensions. Credit to Rob Wu.
[$ 1000] [604897] Medium CVE - 2016 - 1688: Out - of - bounds read in V8. Credit to Max Korenko.
[$ 1000] [606185] Medium CVE-2016-1689: Heap buffer overflow in media. Credit to Atte Kettunen of OUSPG.
[$ 1000] [608100] Medium CVE - 2016 - 1690: Heap use - after - free in Autofill. Credit to Rob Wu.
[$ 500] [597926] Low CVE - 2016 - 1691: Heap buffer - overflow in Skia. Credit to Atte Kettunen of OUSPG.
[$ 500] [598077] Low CVE-2016-1692: Limited cross-origin bypass in ServiceWorker. Credit to Til Jasper Ullrich.
[$ 500] [598752] Low CVE - 2016 - 1693: HTTP Download of Software Removal Tool. Credit to Khalil Zhani.
[$ 500] [603682] Low CVE - 2016 - 1694: HPKP pins removed on cache clearance. Credit to Ryan Lester and Bryant Zadegan.
As mentioned earlier, Google is pleased to announce the program "Vulnerability Reward Program"Is deployed. Information on target bug types, sites, etc. are described on the following Google sites.
Chrome Rewards - Application Security - Google
https://www.google.com/about/appsecurity/chrome-rewards/index.html#rewards
The amount of the incentive is set from about 500 dollars (about 55,000 yen) to a maximum of $ 15,000 (about 1.65 million yen) depending on the content.
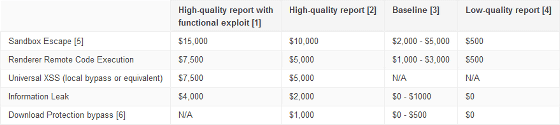
In addition, a reward program for Google's entire service, such as Google and YouTube, has also been implemented, for example, up to 2 for discovering serious bugs such as "Enable hijacking of Google Accounts" It is also becoming to pay the reward of ten thousand dollars (about 2.2 million yen).
Program Rules - Application Security - Google
https://www.google.com/about/appsecurity/reward-program/index.html
Most of the bugs found in Google Chrome this time,AddressSanitizerYaMemorySanitizer,Control Flow Integrity,LibFuzzerIt is discovered by tools such as. People who think "It is" is a good idea to challenge at once.
Related Posts: