More than 450,000 smartphones are infected with malware and are burdened with DDoS attacks of 4.5 billion requests a day

CloudFlare, which provides a wide area load distribution system, claims 4.5 billion requests a day for specific customers of its own serverDDoS attackWe received that we received. As a result of the investigation, it is thought that the malicious script was stepped on malicious scripts via the advertisement network with more than 650,000 smartphones used in China that attacked.
Mobile Ad Networks as DDoS Vectors: A Case Study
https://blog.cloudflare.com/mobile-ad-networks-as-ddos-vectors/
Chinese smartphones mount massive web attack - BBC News
http://www.bbc.com/news/technology-34379254
Originally CloudFlare is constantly subject to DDoS attacks and its content isDNS reflector attackFrom a huge botnetLayer 7 (application layer)It seems to be various to HTTP flood attack to.
Recently, however, flood attacks have been found that make a huge number of HTTP requests to specific customers. Normally, in flood attacks, Python and Ruby scripts are used, and the heading "Acecpt-Language" and "User-Agent" are often strange contents, but this attack is sent from a normal browser It was a request.
Examining from the referrer, there is nothing else besides a lot of banners lined up in lineLink farmOr "advertising site" like advertising aggregator was found. The site is written in basic HTML, and there are only a few simple JavaScript routines elsewhere. So, three JavaScripts including "count.js" containing malicious scripts were loaded.
As this attack was interesting, CloudFlare prepared a dedicated script, analyzed the log of as much as 17 MB, though only 0.4% of the entire request, and examined what kind of attack it was.
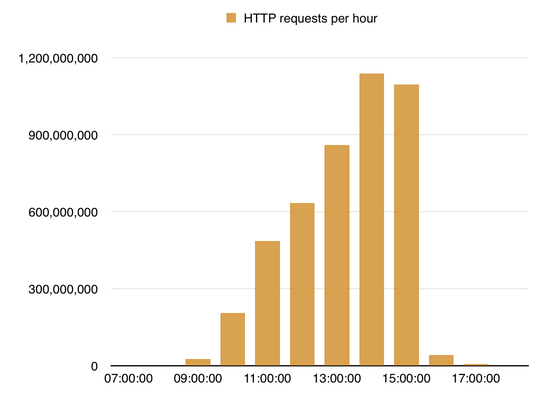
First of all, this is a graph of attack contents received by CloudFlare. The attack began around 9 o'clock and there were about 1.1 billion requests per hour around the peak of 14 o'clock. The total amounted to 4.5 billion requests, and the source was 650,000 unique IP. According to BBC, it seems that it is more than the traffic volume per month of the company 's news site.
Of the total, 99.8% were from China and the remaining 0.2% were from other countries. By type of terminal, 72% was from mobile terminal, 23% was desktop and 5% was tablet. The referrer's URL is 27% for attack site A, 10.1% for attack site B, 8.2% for attack site C, and furthermore it is known that there are many other attack sites and it is an attack from multiple sites I will.
Many "iThunder" appeared to be user agents from mobile applications. Also, "MetaSr", "F1Browser", "QQBrowser", "2345 Expres" and "UCBrowser" which are thought to be from the popular browser in China have been found.
For this attack, which seems to involve 650,000 unique IPs, or 650,000 machines, why so many devices have accessed the attack site is unknown, but probably due to the ad network, CloudFlare I am analyzing it.
In other words, there are advertisements containing malicious scripts among those displayed as in-app advertisements and site advertisements. In the advertisement network, the displayed advertisement is displayed in auction form from one of multiple advertisements, but there is an attack site in "advertiser".
Until now, browser-based seventh layer HTTP flood attacks have been told as "theoretical threats". It is not because it is difficult to create JavaScript as the source of attacks, because it is difficult to effectively spread JavaScript. This time, by effectively using the advertising network, it led to a massive attack of 275,000 requests per second.
According to CloudFlare, the investigation is still in the early stages. There are cases that malware has been delivered through advertisement networks in the past, but can not establish a mechanism to play attack sites from among registered sites as advertisers?
Related Posts:
in Security, Posted by logc_nt