"Do not read the code to find vulnerabilities," Oracle's chief security officer deleted it in a hurry after posting the blog

Vulnerabilities of software and services are not only troublesome for users as well as for service providers, and rewards are often paid for indications about vulnerabilities. However, Oracle (Oracle) 's Chief Security Officer (CSO: Chief Security Officer) said in a blog that after "I should stop because reading code to find vulnerabilities is contrary to terms of service" I am deleting posts by hasty after receiving a storm of condemnation.
No, You Really Can not (Mary Ann Davidson Blog)
https://web.archive.org/web/20150811052336/https://blogs.oracle.com/maryanndavidson/entry/no_you_really_can_t
Oracle CSO goes against bug bounties and security researchers - Business Insider
http://www.businessinsider.com/oracle-cso-goes-against-bug-bounties-and-security-researchers-2015-8
Oracle'sMary Ann DavidsonCSO published a blog posting "No, You Really Can not (Stop it, you should not)" on 10th August 2015. The content of the contribution is "There are security consultants who direct user measures to users about security vulnerabilities of Oracle and create security patches, but these actionsreverse engineeringIt is a kind of thing, it is an act contrary to Oracle's software terms of use, so it should be stopped immediately ".

The purpose of posting by Davidson CSO consists of the following three theories. It can not parse the code to see if the user can control attacks that the scanning tool makes a fuss about. "" Users can not create patches for vulnerabilities, it is the vendor (Oracle ) "Only" "Users are almost in violation of licenses by using tools to analyze source code".

It is Davidson CSO that launched such three principles and appealed customers to stop parsing code, but behind it is the fact that every day as it is done by customers who are posted to Oracle's security counterparts There are too many reminders for vulnerabilities and remedies, and there are security consultants who give advice on security to customers, and they use checking tools and analysis tools to check vulnerabilities There seems to be something that reverse to the terms of service as reverse engineering. In other words, it is illegal to check vulnerabilities using tools that violate the Terms of Service, so we should stop it.
Q & amp; A is also published in blog postings, and from that exchange you can understand the way of thinking of Davidson CSO somehow.
Q:
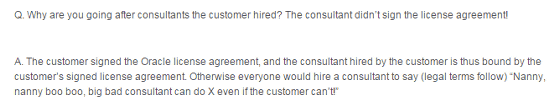
The security consultant hired by the customer does not agree with the terms of service?
A:
As the user agrees to the terms of use, consultants are also tied up. Otherwise, if you hire a consultant, you can complain like a baby and you can do whatever you want if you are a bad consultant.
Q:
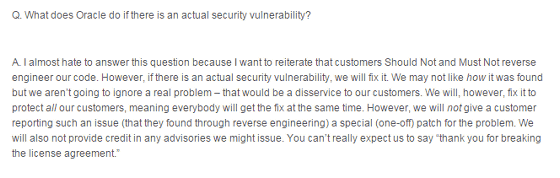
What if Oracle actually has vulnerabilities?
A:
Correct any vulnerabilities. Even if it points out vulnerability obtained by violation. We will protect all customers. That means that everyone gets fixed at the same time. Even if you point out the vulnerability, you can not receive special patches. I do not say thank you for breaking the license terms.
Q:
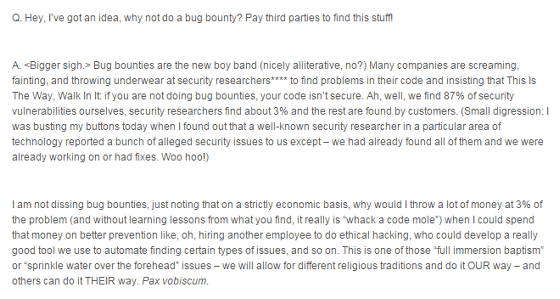
It is a suggestion. Why do not you give a bounty to your bug report?
A:
"According to a well-known security countermeasure company, security researchers report vulnerabilities to 3% of the total, but 3% of them do not have lessons learned from hacking, I would like to employ as many people as I can handle.
Q:
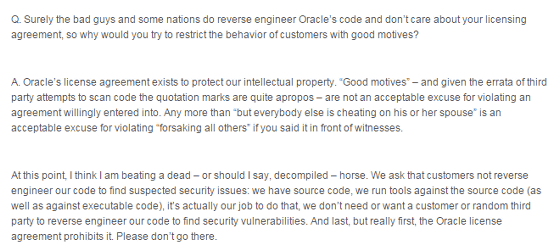
Indeed there will be some malicious reverse engineering, but why do you also restrict the behavior of reporting vulnerabilities with good intentions?
A:
Oracle's terms of use exist to protect our intellectual property rights. It is not an excuse for having a cause of a rebounding of the terms of use even if you have a cause of good faith action. We will ask you not to reverse engineer the code to find security issues. That is our job.
However, according to the idea of Davidson CSO, it can be said that taking advantage of vulnerable software can cause damage to cybercrime and that the content is unfair It is clear. Rather, the existence of a third party that discovers and notifies the existence of vulnerabilities that software developers could not avoid at the development stage is inherently a collaborator as a software developer, It seems to me that it is safe to say that Debitson CSO, who convicts the existence of security consultants and users to discover vulnerabilities as "unwilling to go against the terms of service", has received great criticism.
Davidson CSO deleted blog posts in response to condemnation. About this correspondence, Oracle says, "The security of products and services is always critical to Oracle, Oracle has a robust program to ensure product security, ensuring the security of Oracle technology We collaborate with third parties and users.Davidson CSO's posting has not been reflected in our philosophy and relationship with customers, so we have deleted the official opinion. "

Related Posts: