Ultra-lightweight Twitter client "Momota" Consumer secret key Obfuscation Last challenge

A consumer key such as Twitter official client turned outA super lightweight Twitter client that works even after Windows 95 with the objective of pointing out how Twitter's official attitude is not good, as various kinds of damage started falling into a security dangerous situation due toHakodateThe following entry by the author has been released.
March 11, 2013
More hurting than we expected after hacking TweetDeck - Windows 2000 Blog
http://blog.livedoor.jp/blackwingcat/archives/1760823.html
"As a result, I tried to test whether consumer keys and consumer secret keys can be extracted with Tweet Deck" and tried various things, as a result of opening up the executable file itself in a text editor, eg Windows standard "notepad" It turns out that it can be confirmed.
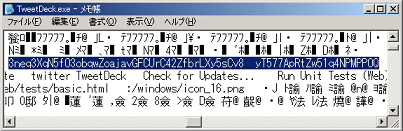
At the end of the entry we will summarize as follows.
However, since it says that we should acquire a new one if it leaks out, we ought to make it as difficult as possible to leak, so I think that it is not easy for official apps to become a sample to be outdated → go back to the start
Supporters so many people are misunderstanding if you see Twitter's timeline.
× Do not use Tweet Deck as it is dangerous
◎ TweetDeck and other malicious software that has unlocked keys are fraudulent official clients asking for authentication, so it seems that they are getting caught so do not believe it carelessly & you have a responsibility for TweetDeck that leaked out with an easy implementation Are not you?
Do not turn on, go down.
But one week later, it was also targeted by himself, "Even the Few authors were criticizing that TweetDeck has Consumer key and Consumer secret in plaintext, I tried to find out what's going on with Fuji "and it was done in various ways.
2013-03-18
Also hacking Fuu you were more severe than you expected - diary of kusano_k
http://d.hatena.ne.jp/kusano_k/20130318/1363640368
"About a few minutes. Futo is also firmer than TweetDeck, but still find it if you feel like that, can you save it in plain text separately? Using special cat Neuman No. 57, I think that there is no big difference in using Immunity Debugger ", so that it is discovered as follows.
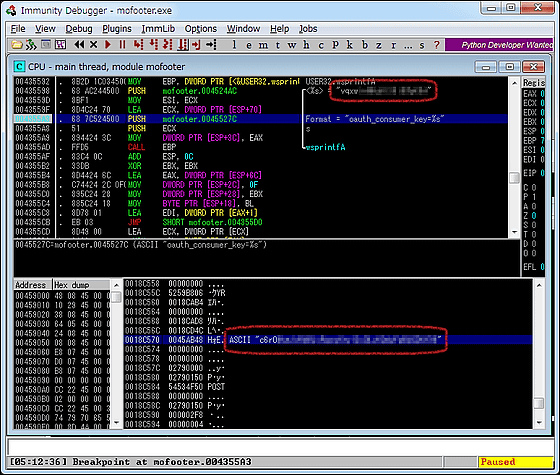
But the next day, too, the author responds with haste.
March 19, 2013
Since Fuu was also hacked, I seriously tried protecting - Windows 2000 Blog
http://blog.livedoor.jp/blackwingcat/archives/1762970.html
Even before there is one case of TweetDeck, since it only took a simple hash, it will be analyzed after memory dump, so I was talking about implementing protected consumer keys in the official version However, as it was hacked as expected, we decided to replace the version of the algorithm that implemented the protected algorithm with a schedule ahead of schedule.
At least, I made it impossible to understand by analyzing about memory dump · · ω ·
, But this time it will be analyzed again four days later.
2013-03-23
A case that was even more severe than expected after adding protection (with additional notes)
http://anond.hatelabo.jp/20130323004725
It is humanity that I want to see if it is really "protected" when it is said that "replacing the protected algorithm with an implemented version". So, I tried out consumer secret out from Fuu (v 0.9.6b) even after reinforcing protection. In conclusion, I could get it out without any problems. The procedure is described below.
Then, the author responded to the above-mentioned matter by haste during the day.
23rd March 2013
The debugging process remaining intact though it was serious - Windows 2000 Blog
http://blog.livedoor.jp/blackwingcat/archives/1763951.html

There are three branches of encryption when applying hash with Twitter's HMAC processing, but the first process was obfuscated, but the loss of being forgotten to remove the debugging process of later processing.
Yes, this is really terrible ....
I have confirmed that the consumer key does not remain in the debugger, but there is no way that the contents of XOR will be rounded up ....
This is a level that I must thank the person who analyzed me.
That's why I corrected it properly.
Thank you · ω ·
That is why it seemed as if it was calibrated properly so that it seemed to be calm, but also the following postscript appeared during the day as well.
3/23 18:45 additional note
もふったーの作者から反応があった。「本気だったつもりのもふったーのデバッグ処理が残ってた」らしい(http://blog.livedoor.jp/blackwingcat/archives/1763951.html)。修正したとのことなので最新版(v0.9.6e)を見てみた。確かに若干変更されているが何の問題もない。SHA-1の呼び出しに中断点を設置して渡されているバイト列を見るだけ。
So, again, it was broken by a haste and it also shook at 1 am the next day - the author responded to this.
3/24 1: 00 postscript Although it was broken by much obfuscation, it is planned to respond properly as it is impossible to do fine work even if it is a code of a burning blade which has been reshuffed a bit in a day. (If it is diverted once, Because it will be followed ...)
· Ω · Please wait for a while
And on March 25 (Monday), "Last Challenge" was finally released.
25th March 2013
Well - Consumer Secret Key Obfuscation Last Challenge · ω · - Windows 2000 Blog
http://blog.livedoor.jp/blackwingcat/archives/1764533.html

For this tearing hacker I tried to take measures other than online authentication.
I have no regrets · ω ·
Will it really end up being scolded by this, or ...?
Related Posts:
in Note, Software, Web Service, Posted by darkhorse