Takagi Hirokiru's indignant speech "privacy protection in the game industry" is amazing

"Hiroki Takagi @ home diary - T point says "Please be forewarned""Point point toolbar points out that it is" induction of cheat fullness "by the entry"Stop T point toolbar download temporarilyIt is done, and also "Download Penalization makes it possible to pick out dreams and eliminate them"It is necessary to prepare to throw out friends to go out with Lawson"Mayor Takeo, angry at the press conference "Why is this personal information!" Spitting up"Personal information protection ordinance of Takeo city which was still a defect"And has continued to have a huge impact on security one after anotherNational Institute of Advanced Industrial Science and TechnologyofHiroki Takagi(Common name:Hiromichu) ByCEDEC 2012Lecture is very excellent content, not limited to games, including even smartphones What is "personal information" in the first place? So from now on, we are talking about the current handling of personal information, privacy and the way we should go in the future.
Privacy protection in the game industry | CEDEC 2012 | Computer Entertainment Development Developers Conference
http://cedec.cesa.or.jp/2012/program/NW/C12_I0294.html
This time, Takagi's office is vacation on forced summer vacation, so it is said that he is talked as an individual Takagi, not a job.
Hiroki Takagi (Takagi):
I tried thinking about the subject of wanting to talk about privacy in the game industry and security, but what about privacy if you are talking about security in the game industry? Regarding individuals' games, it is about 30 years ago, but in high school daysDig dugAndXeviusI was doing something, the game industry has nothing to do with it, I do not know it at all. However, only game machines will buy when they get new. So, if you say what you are doing, there is no hole.

participant:
(Lol)
Takagi:
It is said that it ends only by searching for a hole. It is such a feeling. I thought what kind of story is about privacy in the game. First of all, it is natural to take measures against information leakage. There was a big incident in foreign countries that actually the Japanese network was actually destroyed last year. As for this, I think that I will skip the security measures normally properly, now it is supposed to be omitted as I have nothing to say from this.

Takagi:
Four other items are said to say that there is something else, first of all, it is a story to make it possible for users to control their own information. Under the lawSelf-information control rightThere is the word saying, is there really the right to control self-information? There is something like story. In other words, it is about the issue of whether I have the right to stop my rumor. But what I want to say here is not that kind of story, for example on a social network, there are people who do not know what will happen as a result of doing this now when using the service . Speaking brieflyFacebookIf you write something on it, you will be in an open state or you do not know such a thing. When I write a review at Amazon, it seems that the real name actually makes the review public, but I did not notice such a thing. Because such things happen because you can not control your information yourself, that kind of service is not good. I think that there is a topic / topic of such a case.
Another thing is what is personal information. This became a problem especially last year, but there are quite a few who make misunderstanding that the address name is personal information. For example, some people say that the browsing history of the web is personal information, that such information is not personal information. There is one story that it is different.
And the other is a smartphone application. Although smartphones are spreading at a stretch from last year, since the game industry is likely to compete with smartphone applications in many cases, I think that the talk about that is one concern of all of you.
Finally, analyze the user's behavior. Mining or somethingbig dataI have been told that it is. I think whether there is a topic of how much privacy this can be done, but I am not getting down on this as well and I hope to be able to ask all of you the troubles of flames etc. .
It is the first topic immediately, but in November of last yearStoryhad.Playstation NetworkThe trophy information of the outside was able to be browsed from the outside and it became a stirring, did it burn up? FinallySonyThe apology apologized.

Takagi:
News from ITmediaHowever, it is "An apology as insufficient explanation and announcement of correspondence such as revision of regulations". As to how to describe the terms of use, "As a part of the service on PSN, we may provide information related to customer's game play to other PSN users." It is a story that I understand the meaning. The cause of the commotion is that IthisBecause I wrote.
participant:
(Lol)
Takagi:
Originally it was noticed that there was a problem in August. And when you listen to everyone on Twitter and look it up, you can hear the overseas situation like Xbox can change it properly by setting. Then it is bad that only Sony is not doing, it is bad in many ways. Perhaps because I was suddenly beaten abroad, I thought that Japan might also hurt the national interest, so I wonder if I have to say something. Just about that time, as I said earlier, it is misunderstood that what personal information is like "address name is personal information". It was a time when the erroneous idea of legally protecting even the name and address of personal information, which should be protected, wished to spread, I thought that it is necessary to cast one stone. So in November, I wrote such a thing. To tell me what I mean, actually I use a PlayStation network for a bit, and I have an account for a Nekama character with the story. I wrote it on the 14th August diary, but at that time I was revealing my PSN's user name.
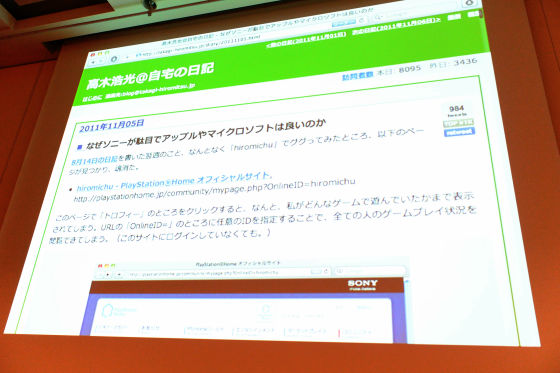
Takagi:
When I searched for that user ID on Google, something called Play Station Home's official site came out, and when I accessed this URL, my information came out. There are profiles, 8 trophies, like level 1. And there is a list next to what list of games you started. I did not know this at all. Personally, by chance, it does not matter as to the games that are lined up here, when I told you that it is a problem that everyone is in a state to understand that I am playing such a game after all. I think that I wish I had done a little moe game or something. I do not do it.
participant:
(Lol)
Takagi:
Although it is the feeling that it is the touch saying, it is actually to ask it on Twitter, since it was disgusting and disgusting from the front, I wanted Sony to be stopped by phone, and I asked a person to go out with a few people It was. "But it did not change" I was feeling. So, although Microsoft introduced it to make it changeable by setting properly, or Apple introduced such a thing, but then, there was a strong opposition there. I have gone lately recently, but the summary siteGaehaFrom people who hang out, I got an attack on Twitter and it was in a war state. The aftermath is also quite troublesome, some people calling protests at work are also appearing, there are some people trying to name them, the game industry is quite a difficult place Come on, (laugh)

Takagi:
It is about going through various investigations, someone who intensely attacks using multiple Twitter accounts in such a place, I thought that it was a woman from the sales of some sort of game software company (lol) It was pretty tough. Everyone is fighting behind the scenes, it's an incredible industry. I wonder if it was a misfortune to have a place of the form like ah in 2 ch. Today I did not talk about such a story, but (laugh) I got a lot of resistance. It is only a matter of trying to be able to choose it myself, why can not you? Of course I do not know what Sony thought. So anonymous people have been resisting a lot. "Is it a privacy to protect like a trophy?" Or "You know that it is made public", or "You can not identify an individual from an ID, you are wrong about how to use IDs" , "It is written in various conventions", or it can escape.

Takagi:
In terms of privacy this is a typical pattern. As with a trophy, say, but basically it depends on whether people dislike it or not. That is what the user should decide. No matter how trivial it is, the disclosure of functions and information that some people may not like will be made so that users can choose. It is sometimes made from the beginning in such way. If you told me to fix it later, since it may take a lot of time, I ignore it, because I do not like it, or there may be things like arranging appropriate excuses and responding to the phone, I think.Privacy by designThere is a word. If you say that you can not select it you mean you stop using it. It is OK to move to another hardware, but I do not want it, so someone told me that it is because I like it. That's the story.
As far as I was told, "I know everything is open to the public", there were actually many people I did not know about. If I do not know, I can not deal with it, I can not raise my voice, so I thought that as long as I did not make a noise, I could not do anything. And I say that I can not identify individuals from ID, but today there are various SNS services. Twitter, Hatena, mixi, Facebook may be different, but if you decide your ID yourself, you are using the same ID with various SNS, you know that way. What is it "that person?" This is the problem. So, there is actually a profile of a bakera who I am acquainted with, but this person got the same ID even though it was a hatena, so to those who know that "he did this game You know what I mean "is not it? Another problem here was that it was not only a simple game,TorneI also thought that it is one point because it has trophy function and it is made public. It is like this, Torune said, "This person is up to 47%."
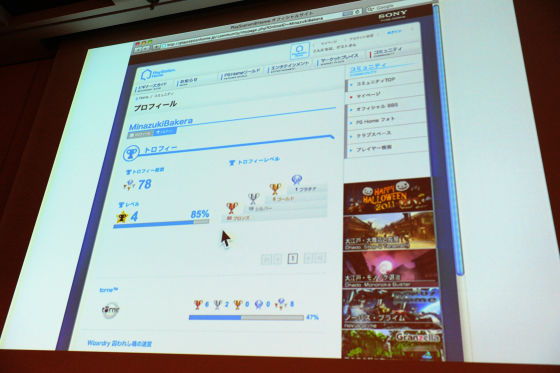
The name of the trophy is "???" and I do not know which trophy, but this is not a separate consideration of privacy, but in the case of a hidden trophy it would not be funny to reveal it from the beginning so dare to hide It is only there.
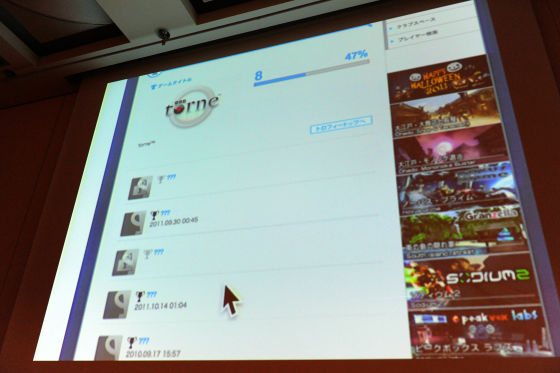
This is because the order of arrangement is constant, so if you actually have all the screens you got, you know what the trophy is. This is the voice of the person himself bakera, but this person is quite a bit of the IT industry ...... It is a so-called professional, but even if you have a professional, you did not notice what this is open to you.

I do not remember seeing the explanation, I said that this is called open to the person who registered the friend, I knew that it was disclosed, but I did not think that it was open to the public widely. In the case of this person, it is due to Torune, it seems that the fact that you are watching anime is getting bald. Moreover, if you look closely, the worst thing comes out until the date and time you acquired this trophy.

Although it may be good to have dates, why is there meaning to display acquisition time in minutes? In some cases, privacy may be a big problem. In other words, I think that it may be a disgusting feeling for himself. Perhaps the person who is developing does not think about anything, and it seems like you tried to display whatever you can display, like thought. I think that it is necessary to incorporate from the design stage some way of thinking "not to go out so far" there.
On the other hand, this is the case of Xbox Live. There is the current privacy setting in this way, it is understood that it is possible to disclose the profile to the friend, release the game record, release the state of the online state, the state of the online ... ... that is whether it is doing now or not. I have to allow such rules with this setting.
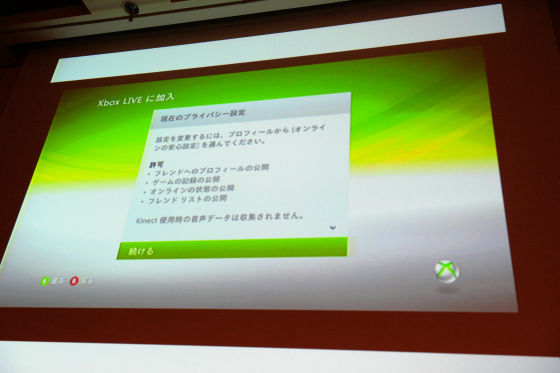
About these things, it is about each setting individually on the screen, you can choose from three such as "everyone", "only friends", "prohibited", and which one you choose Well it is written that it will happen.
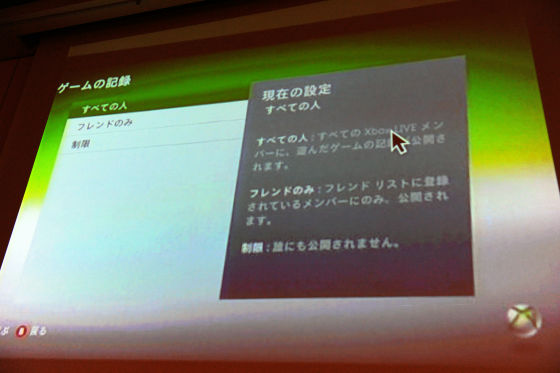
I think that Microsoft is doing it properly. For a decade ago, Microsoft had a history of being struck with security in a stabbing manner, and from around 2002 and 2003, Microsoft suddenly changed direction, came up with publicity that cherish security and privacy You have it. I am wondering how hard it is for companies in Japan. From my opinion that security and privacy have come to date, it seems that companies in Japan are really bad. It really is no use anywhere. Why is that? That is what I think.
This problem is, it is not news unless it makes a big noise on Twitter. I think if the net media is more secure. That is, from a time when the voice came up a little, written an article saying "Oh, yea, that is logically speaking," there is such a problem, Sonny how about you , I hope that an article of such suggestion type should appear, but I have not seen it. An article that comes out in general is a lantern article, which says "funny funny, wonderful, nice" or something made a mistake and apologized, "hit the horror" and hit it from above . If such a press release does not come out, there will be no press release until it comes out, and that will not come out until we announce any information. Is not it manageable? For example, thisEngadgetIt is about reading an article,Written somewhat ironicallyWe do. It is good to write sarcasmically, but I feel like writing more quickly. To this point, it is written eventually that if you do not want to use it, before you use it, before you use it, you do not have the opportunity to be aware of whether you do not like it or not, and you did not write even if you read the terms.
Finally Sony says what he did, like thisNoticeIs out.
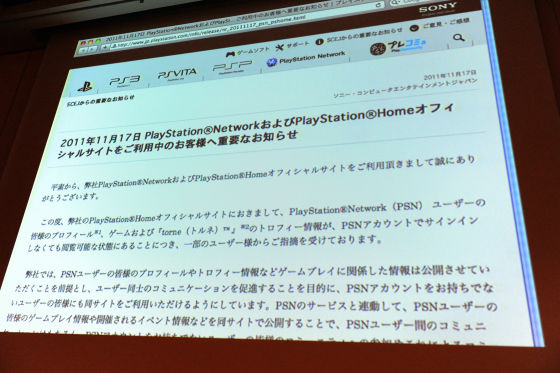
I will briefly introduce what you are talking about, "It is written that some troubles are being accepted and that we are going to publish trophies etc." Right. But if you think that Tornell is just a television recorder, there are people who do not have any games, but some are purchasing with a set only for Torne, just a TV recorder I think that it was a considerable problem that it was a machine that disclosed to the Internet what kind of program you are watching.
I do not think much of the problem with that is being written here, but after all I said what I did was to rewrite the convention.

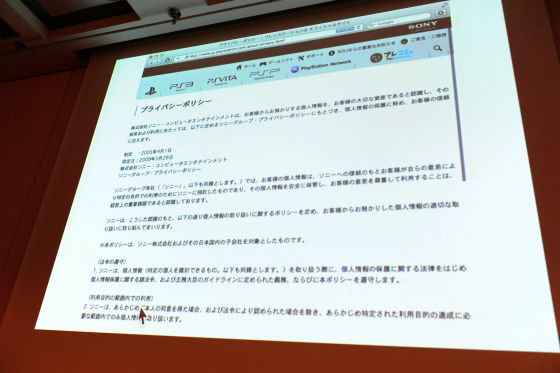
Since I have not written it in the contract, I can not escape anymore, so I will change the convention. I got into the means to write that "it will be published to the contract." Everyone was disappointed to do that.Hatena Bookmark CommentIf you look at it, there are some comments like something like Sony did like it. I wonder if it has fallen. It says that we will consider improving through update in the future. I think that I do not correspond as far as I know. I am just looking into it. This seems to be amended in July of this year with its terms of service. Where it is written is "10". It seems to be written in this.
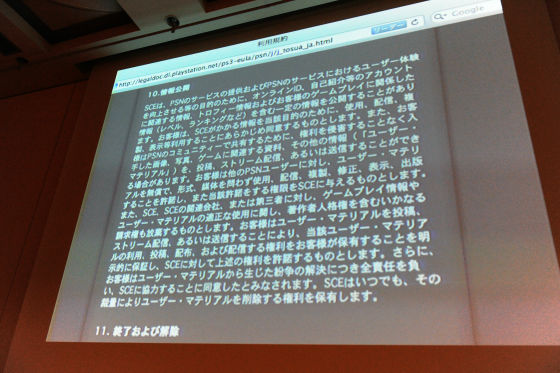
For the purpose such as improving the user experience, it is possible to disclose certain information including online ID, information related to account such as self-introduction, trophy information and information related to game play (level, ranking, etc.) There is written, there is. If it says what is written from the next, since the information will be released, it will be awkward for customers to claim copyright. I am saying that there is a right to publish information here. The term of use is one that you do not mind at all if ordinary ordinary people are playing normally. However, some of the strange people come out, "What do you think is copyright of cracking!"User Generated ContentSince it is troubled by copyright claims from those who are publishing, it is the terms of service to put a legal defense line in advance so that we can deal with it in such a case What I mean is that it is inherently impossible to write in the terms of service. In fact, it may be better for the explanation that this service is such a service to be separate from the terms of service. Instead of reading sentences, I think that it is ideal and ideal to make it natural to know the setting, the process of registering users and the process of playing naturally to see what is happening I will. By the way, I do not know well how to write in the "1" chapter, where is it written? I do not know where it says to be published. I can not help being surprised that we deal with this. There is another privacy policy, but the Japanese privacy policy is written only that it works hard to deal with, there is no need to look inside, there is no point in any meaning Thing. I will comply with laws and regulations, I only write that it will be used within the purpose of use, then what is its purpose of use? Writing things is supposed to be the original privacy policy, but I do not write purpose of use. It is very funny.
That was the case last year, just after that half month or a month laterPlayStation®VitaSince it was on sale, I bought it. I bought it, but I have not played it at all. Then, there was a privacy setting screen properly, and I was able to make sure how much to disclose the activity, how much to disclose the friend list, and so on.

I guess it can not be made in half a month, so I guess I was originally making it. Or, I wonder how you made it quickly. Although I feel like I can do it if I do it. That is such a story.
I think I will go to the next topic. The current story is also a bit related, but what is personal information. At that time, it was a relationship which became a considerable war, the discussion deepened variously. I understood well what it is and what kind of disclosure it is doing. What is personal information is misunderstood. Recently I have understood a lot, but at last year there was a trend that I could do anything without personal identity.

However, whether it is an application of a smartphone that acquires history or the like without specifying an individual, or spyware, whether an individual is specified or not,Virus creation sinThere is a possibility of hitting. First of all, you have a question on the word itself of individual identity. In Japan's Personal Information Protection Law, it is defined as "a person who will identify a specific individual", that is, his name, address, etc. Specifically, who said that is specified is said to be personal distinctiveness, but when I think carefully, I have not identified individuals, but someone who is a mysterious ID like Mr. B There is a person in a state distinguished by, and it is the present condition that it is not protected by the law of personal information protection. Then, if it is a company that has a legal affair if you keep even the law, you will be talking about spooky things and doing spyware wearing things. That was just the same time last year. One thing I'd like to talk about in a terrible episode, but there was an information leak accident in the library in Gifu Prefecture at the beginning of the year.

It is a very big problem in terms of privacy because the database of dunning information of late books of books leaked. Because there was no information on who is reading what books. The text that the library announced at that time was like this. The contents of the information that leaked was part of the information of the user registered in the library, and the content of the data was the name of the user (Kanji / Katakana), address, date of birth, zip code etc Shin. Anyway, why do not you write a dunning letter, although the title of the book should have been leaked? By the time I tried checking by telephone interview, it was that the title was leaked out. When asked why I did not write why, I was told that the address and name are personal information. This is a typical misunderstanding. In the case of a municipality, it is defined by the ordinance of each municipality, but the definition of personal information is information about an individual, and it can be identified as a specific individual. This is roughly the same as the private information protection law of private companies, and there is information about individuals first. The way of this ordinance is limited to such specific ones as those identified by address and name. Yet, the idea such as an incorrect commentary has circulated.
This is a commentary on last year's stage, but there is a system called privacy mark.

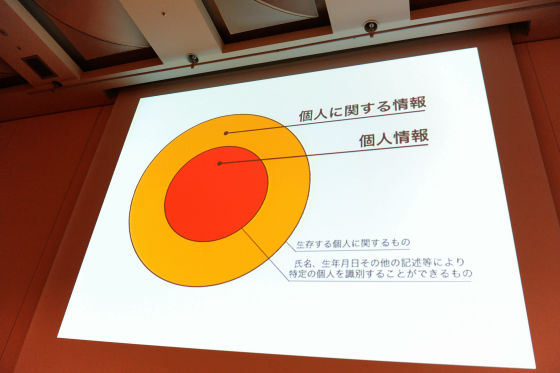
I am doing pre-emption of the privacy markJIPDECThere is a content privacy mark system that is well-known and I am writing the difference between personal information and privacy, but as I have learned so far personal information is an individual (name, date of birth, address etc.) individual It is said that it is the information that specifies. This is a mistake. It is a terrible thing to look at the lower person, saying "The envelope's address is personal information and the contents of the envelope is privacy if you can say it". If it says how strange this is, it is personal information including the contents of the envelope. I will illustrate this by a diagram.

Personal information that is written in the explanation of this incorrect privacy mark means that when there is a database in which the name, address, browsing history, etc. are recorded as one report, the term "personal information" The red part, the part of information to identify individuals, the browsing history etc. are not personal information. I am misunderstanding that it is privacy, but not personal information, that it is not subject to law protection. However, the personal information referred to by the Personal Information Protection Act is information about individuals, individuals are identified, specific individuals are indicated, so all information based on individuals is everything. . It's all. Information about where you are, where you are on the site, what site you browsed, and what kind of detail it is, such as the playstation network trophies, for example, information about individuals.
It is awesome and businesses are troubled if it says that all information about individuals is protected by law. I do not know what information I am protecting what information. Therefore, it is impossible for the personal information protection law to be protected indeed so that it is impossible to protect the information about the individual indeed, so it is impossible to identify individuals, specific individuals are identified, specific individuals are identified by address name, etc. It is the purpose of the law to define only the red part as personal information, and first let me describe it properly. If it gets misunderstood and it does not even have the name and address of the address, it means that the individual is identified and it is not personal information because the specific individual is not identified. Because of that, it is because merely whether there is an address name or not is noticed, it seems that misunderstanding as if only address name is personal information has spread. What I would like to say here is that only individuals are identified as law subjects, but in reality, the orange part of the yen, information about individuals is regarded as privacy, protect it by law It is the original meaning. However, it was not possible to do so. So, if it is a serious business person who respects the purpose of the law, it is important to manage properly even if there is no address name.
 I mentioned about this in this area, but after all I think whether identification and identification should be considered separately. Also, I think there is something that identifies but does not identify individuals.
I mentioned about this in this area, but after all I think whether identification and identification should be considered separately. Also, I think there is something that identifies but does not identify individuals.

It is such a thing that you are using a web browser or identifying a mobile phone terminal, in other words, using cookies or using a terminal ID. Even if this does not directly identify individuals, it is an ID / identification number attached to the same person all the time, so I think whether protection should be considered originally as it corresponds to the part of the previous Orange. I think that it is okay because it only identifies by anonymous ID at this time, but there are various things even if it is said ID, for example as shown in the left figure for each service If you use discrete IDs. The same person has several IDs. In terms of cards, it is like a case where cards and point cards are used separately for each store. The right is to process the service with one common ID.
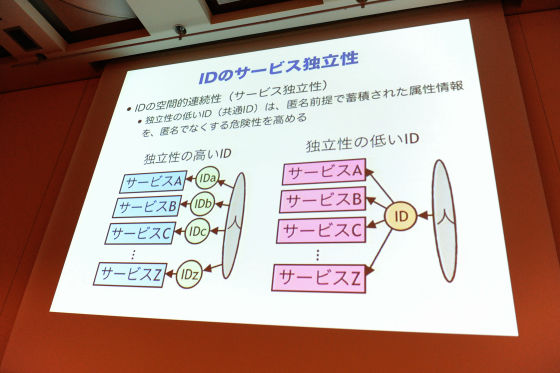
T point by saying a point cardPONTACommon point system such as such as the hit this, but the privacy on the right seems to be more risky. It is for himself. The right side has the risk that what you are doing is being analyzed by being brought together by sideways skewers. Actually, even if the ID was anonymous at a certain point, when the information passed to someone else, there are cases where the individual is identified as who the person is with that ID. I will illustrate it briefly.
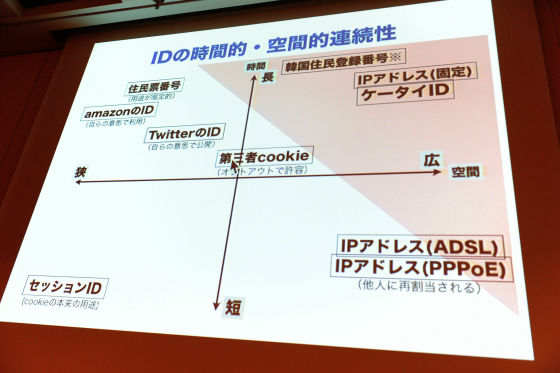
In the end, IDs are cases where the effective range is wide and narrow, and on the other hand, on the vertical axis the ID is almost extinguished and the time to substitute for the new one is short, for example, the IP address changes frequently That's right. On the contrary it is also on the upper side that numbers that will not change for the rest of my life. In this figure long and wide are the risks of the trader market, so if you are watching an argument by English-speaking engineers, IDs in these areas are risky so do not use them Is the discussion going on frequently? Looking at Japanese law, the secret of communication is quite strict about how privacy is protected in Japan. Is it no matter whether an individual is eavesdropped by eavesdropping on the phone or not, you are arrested immediately.

Meanwhile, as explained earlier, if we treat information that is identified as a specific individual among information on individuals, we will not identify individuals, such as information identified by terminal ID etc. How to protect it is very difficult because there is no law. With that kind of relationship, there is movement this year, it is a problem of smartphone application.

I think that the application of the smartphone was around New Year of this year, but it was being reported on television that a lot of things that have various privacy problem movements came out. Based on this, the General Affairs Minister considered the viewpoint of the userICTThere is a research group on various problems related to the service, as a working group of various research institutes, I have been doing working group on handling user information via smartphone from January to this month, the final summary It came out on August 7th.Smartphone · Privacy · Initiative. I do not know well, but when I look at the subtitle, I think that it is a name that takes into consideration various aspects, "innovation through appropriate handling of user information and improvement of literacy", but regulating what everyone should do properly I think that you should do it voluntarily, not by all. Actually, this workshop has once made a recommendation two years ago. At this time, on behalf of the web's behavioral targeting advertisement, it promoted voluntary guidelines by the industry. Actually Internet Advertisement Promotion Council "JIAABehavioral targetingAdvertisement guidelinesWe revised it in 2011, and since the behavior targeting of that web is done with the ID of cookie, we do not identify individuals. I do not know. Because it is only distinguishing by the number of the random number shaken in the browser, someone does not know. In that sense, I do not mention the law of personal information protection, but still I did that to ensure that transparency was secured and to provide a means to opt out and refuse.

When asked why such a thing was done, before that two years ago in the United States the AmericanFTC, The Federal Trade Commission is taking over and letting the industry create these guidelines. Internet service will spread internationally in Japan too, so I think it was possible to do it in Japan together. Today, if you are watching the web, if you go to the privacy policy, it will be linked with "This site uses the ad network there, in detail here". While I am lagging behind the United States, I am finally getting to be explained. On the other hand, the working group of user information on smartphones this year has advanced one step and is regarded as an opt-in method rather than an opt-out.

Although it can not be called anything opt-in, here we are recommending that it be an opt-in method of acquiring consent on individual information about information on phone book, GPS position information, call history history . Another one is, the terminal ID that came out earlier. Since the terminal ID is an identification number that everyone can use in common, as we said in the previous figure, it becomes a common number for the service, and in the 2D diagram, it is a dangerous ID that corresponds to the upper right side There is. The Ministry of Internal Affairs and Communications defines that it is appropriate to deal with such ID in the form of personal information. There are trends in the US as to why this has happened. in AmericaConsumer Privacy Rights Bill of RightsAlthough I could do this year, I definitely said "Personal data such as smartphone ID etc" as the definition of the term personal data in it. It is becoming also in Japan as a way of thinking that this will become an international standard in the future. Then it seems that various problems will arise for everyone who develops smartphone applications. Actually, this slide was used by another slide show, it takes one hour to speak as it is. So I will tell you a little omitting it. Some businesses ask the working group why it is opt-in, "It is troubled that discussion is taking place as all opt-in". Opinions such as "Please forgive with opt-out" are also coming out.

The Milog Company's third party committee in December 2011 insisted that it was strange that it would not be permitted to admit information without consent at the time of collection or because it was opted out But when such a thing is said, such cases will come out as well. last monthSymantecAlthough it is what the company announced, it seems that a false app called "something of a miracle battery saved" is circulating, it is an application saying that the battery lasts long.
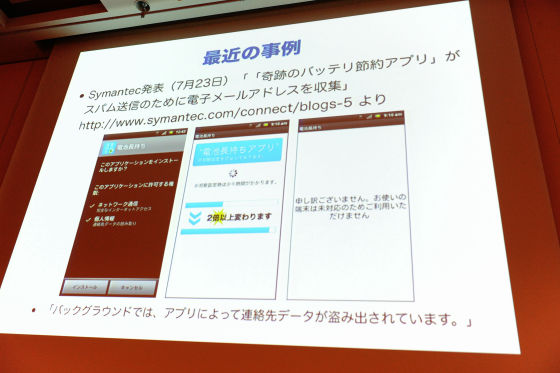
If you look closely, you are requesting the reading of personal information. It is an application that steals all phone books while saying "I am sorry, it can not be used because it is unsupported" when I start up this, it will change more than twice. A similar application came to me as well. You come by spam mail. An electric wave improvement application. After clicking the link, I downloaded suddenly. Normally it is blocked because it is set by default so that only applications on the market can be opened, but those who set it not blocking have been killed. It is very scary.
This is a very clear application, so last year the criminal law was amendedCrime related to electromagnetic recordingIt is said to be the criminal law 168 2 and it is a grim level of asking crime.

But what can you say that is malignant? I do not think there is such a thing, but maybe they might have tried to collect phone books and use it for marketing or provide useful services. I do not have a slide when I give an example, but in JapanLINEAlthough this application is popular, this application was supposed to upload the phone book without first without permission. As this was criticized soon, it was improved by the developer to fix it, not to upload unless you agree with opt-in. That kind of thing comes out one after another, so what is the way we go about disciplining it is an issue today. About the maintenance of opt-in or opt-out, this is a good example, but in the case of Facebook application, I use the phone book with the function to search for friends, but when the timing to use properly comes, "I will do this kind of things from now Is it OK to confirm? "Is not it? It is not enough to write something in the terms of service, or because users are requesting a phone book with the permission of Android, users should understand that it is not such an idea of technicians, It is the recommendation of the Ministry of Internal Affairs and Communications that it should be properly built so that you can know what to do.
I guess this is difficult to understand easily. This is a very bad example, but here it says "By sending" AppLog, (terminal application information, etc.) to Milog, it helps to improve the user experience etc. "
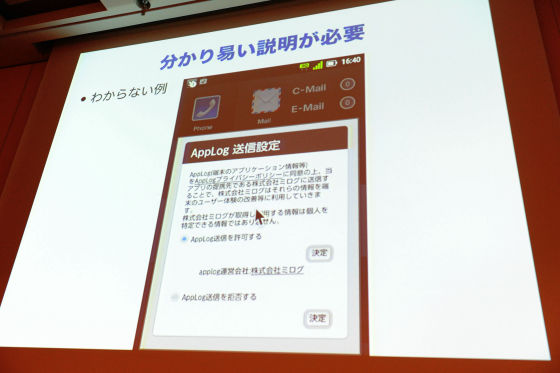
First of all, I do not know what application information on the terminal is. In fact, what this was actually, this person says what kind of application you are installing, the list of installed applications list and the list of recently launched applications are sent, meaning to collect I do not know, is not it? From the making side, it can be common sense that pointing at the application information of the terminal within the company is common sense, but it is not understood by ordinary people. However, if you do not explain it so that people can understand it, it may be handled as virus. Of course, I think that natural applications are not such a thing. Speaking of the same example, in fact there was also a service that introduces smartphone applications according to your taste at that time. In searching for your favorite app, please upload the list of applications on your smartphone, look at it and associate it with other people's data and recommend this one. In this case, I do not have to explain it separately, I understand intuitively what you do and what kind of benefit it will be for you, or it will not be used outside purpose. Actually, however, this is exactly the purpose of marketing, even an application of completely irrelevant game etc., insideSDKIf you upload an embedded one, the installation situation of the user's application will be gathered and taken over. Even though the user tried to play the game, he / she would become spyware if he did not describe it so well that he should not misunderstand that he / she should have history.
In the case of the smartphone application, since the way to use the SDK said earlier has become very widespread, there are times when some people come here may not be making applications by incorporating an SDK that we do not know well I think so. If you do not investigate what the SDK is then at that time, it will take responsibility for those who develop and incorporate the application, so it is not a different person. On the other hand, there might be someone who develops SDK, but in that case, how to ensure that end users do not get misunderstood regardless of how they are used securely I would like you to think carefully about what is good. I will omit this part a bit.
I briefly mentioned the terminal ID earlier. In the English-speaking countries such as the United States, privacy information leakage has been said for a long time, in the old days go back to 1999,IntelofPentium IIIThere is a problem with the processor serial number problem. I tried to embed a serial number in Pentium III so that it could be used from the program so that Intel said that it would identify the user and realize easy login of the EC site and so I bathed in a big bashing. We have reached the boycott campaign as having problems with privacy. Eventually Intel will break and disable its function, it will be turned off. Exactly the same thing is repeated by the spread of smartphone. The terminal ID is essentially the same as the processor serial number. To make matters worse, Apple prepared the unique ID of UDID, but a lot of people diverted it.

That is, even if there is no ID / password at the terminal, there are many services that you can log in with the terminal ID. Especially in games. Originally it is said that it was the first time in the game to use UDID when recording high scores. That way you can register a high score suddenly without preparing your ID / password. This means that the danger of impersonation is obvious. When UDID goes to the hands of others and there are many lists of others' UDIDs, there is a list of UDIDs for those who are doing something. I can spoof it by accessing a high score server using it. Do you register a fake score? It is not a problem because it is OK to register a fake score whether it is altered if it is a high score, but if it becomes a service of a use related to privacy, it will be. Last summer in the United States a member of the Congress sent a questionnaire to Apple, so Apple is moving, I am forecasting that we will abolish UDID in August. In May of this year, applications that actually use UDID are being rejected. Here comes the story saying "Why should I use the terminal ID, why not use it?", But it's not that easy. For example, trying to do something like behavioral targeting ads here, but when trying to use ID commonly among multiple applications among applications, there is a third party cookie in case of web, sand Thanks to the unique mechanism called Party Cookie on the web, it worked well, there is a troubling problem that it can not be done with smartphone. I think that I have not concluded yet because I have no other choice than to resolve this at the OS level. This neighborhood is the current hot topic. Perhaps you are talking about which sides are related to everyone here, talk about using a local ID without using UDID, or using ID collaboration, using something like an open ID I wonder if there is no choice but to do it.
Because the time is now 6 · 7 minutes. This is what I am doing now. Although the Ministry of Internal Affairs and Communications issued a proposal, the recommendation is only a recommendation, not a regulation. So it is expected that the business entities will voluntarily work on it, but even if it is so, I think that it will not be getting better if we do not have an effective policy. I am planning to continue with that as well in the future, so that is what I should look at. I would like to prepare the time to ask you a question at the end. Perhaps it was originally thought that they wanted to hear such stories, but it is an analysis of the behavior of users.

To be honest, I think that it would be nice to do it without permission in the world of the game, I think that there is something to say. If this is the medical field, for example, it is a very difficult problem. If you analyze medical information, there may be groundbreaking discoveries in how to cure sickness, but on the other hand it is a human rights issue that you must use information with proper consent. However, even if it considers taking agreement, it is a difficult problem whether the person himself / herself or the patient understands and uses it in the real sense. Compared to that, I like the game because I do not like how much information can be exploited and analyzed, I honestly feel like stopping if I do not care whether it is OK or not (lol)
For example, what kind of game it is analysis, I would like you to tell everyone, but this customer is a very good turtle, or a good duck that pays money for as much as you want, that kind of thing Do you find mining big data? I do not know it well, but (laugh) I wonder how far I can do it.Complete GachaOr, it was a problem. If we go further, analyze the use of such customers and fuel something for that person, is not it better to do something to suck up if you take money more than it? It may be selfish of the person who does it in the sense that it is not a game including it. In the end that such regulation entered for complete gacha in the end, there must be somewhere a line that should not be done somewhat. I do not understand well because I'm not studying at all. However, I tried to write that there is something common in other fields.

The narrower the scope of information to analyze, the better the problem is. However, when you start analyzing people about games, privacy problems arise. The problem of privacy is not necessarily meaning that it will be an infringement of privacy if it never leaks, there is also the idea that analyzing the figure of a person itself is an infringement of certain kind of privacy I'd like you to keep it in the corner of my head. We have expanded further and crossed services to cooperate with other companies, analyze and portray people's figures like the common point system on the side, or even more simply like blacklists I think there is. This customer is a very bad customer, so if you start making blacklists in the terminal ID and sharing it in the industry, it may be an infringement of privacy. I do not know if it is lawful, but I think that such ethical issues are lying. And the other question is whether you know that users are doing that kind of thing. I think that it is better to explain as much as possible, but since the customer may be scared and run away, the idea of trying not to explain as much as possible is to conceive the customer as a result is. Some kind of "UnwillingnessSince it corresponds to something like "I do not have such a bad idea, I think that it is a good company's way to explain the true things properly and increase transparency. After that I said a bit, but what is said to be anonymous analysis is really anonymous. I think whether there is such a topic such as whether it can not be said that it is an anonymous ID if analyzing with the terminal ID. I talked about four topics five times, but since it is two or three minutes ago, if you have any questions or something like "Is this what you are analyzing?" I would like to do it, but how do you do?
Questioner A:
I'm sorry, I am not a business operator. I think that the game itself is exactly a duck, and that money is gotten from that person, which is a bad way of speaking, but I think that it is going to develop into such a way as to take up as much as possible, Should I withdraw? If you have any comments.
Takagi:
If you think about it (lol)
All together
(Lol)
Questioner A:
If the administration judges such things, what can be done?
Takagi:
There may be something when a very severe situation arises, but in the end, I think that what you can do first is to raise transparency, and you can only say something like that. Because pachinko would be doing in a certain transparency, I wonder whether we will have to do similar regulations and voluntary efforts.
Questioner A:
Thank you very much.
Questioner B:
As was the case with LINE in the past, when we collect phone books we confirm with them, but they are still handed off to those who are registered in the phone book . Is there no way to prevent it?
Takagi:
There is nothing I can do about this. This kind of way has spread, so it can not be said to stop it now. It has been used at last. The businesses that are doing just are not getting raw data as they are but convert it to a hash value and get it. Since it only matches, it should be matched by hash value. It is said that it is good because it can not return to the original data. If the phone number is something, it will be restored. Well, what is the problem of being uploading my phone number or e-mail address to someone else? In fact, it is actually more problematic to upload something like a phone number or e-mail address without permission It is a problem that information is uploaded and partially combined without permission, whether you know a social graph, who you are friends with, who you are, and who you are. It is not the number itself. Therefore, even if the business side says it protects with such rules, it is not settled. There is nothing I can do. One thing that can be considered is deleting my information, requesting such a service beforehand such as not to register again, may be applied. Although there is a talk of whether to request based on the personal information protection law, I think that a good service provider should prepare such a way by themselves without thinking so much. In that sense, a company that is doing LINE,NHNBecause he seems to be working seriously. Everyone also thinks that "I can not improve this kind of thing" and I think that I have to gradually improve often.
Questioner C:
There is one question, but now, in the work that I am engaged in, there is a social type, but when individuals register for membership, it is public order and morals or works There is a task of registering a member in the form of registering once using a mobile phone so that no selfish writing, vandalism etc. related to the right is done. Unfortunately when someone starts to operate, there are some people who become problematic as a management side, register UDID as blacklist as a management side, once BAN correspondence, so-called compulsory member withdrawal, so do not re-register There is a thing saying that it was taking the registration process of saying that UDID keeps the information to be treated in the same row as personal information as a black list as it is now. I think that it is useless to operate, but is it really a good thing?
Takagi:
If you answer briefly, it is not a good thing, so I think that you should give up. Looking back at the world of the web of the general PC, there was no such mechanism. Whatever you do, people who pass by will slip through. UDID can also be camouflaged. It is that it was said from the time of the boycott campaign in 1999 that it is impossible to completely prevent completely and people are invading privacy, on the other hand, that such things are not good. So in the past 12 years, in the world of PC, there is no such thing, so how to eliminate such a malicious person or to do something that is okay even if it can not be excluded , I think that the service of regular internet web has grown. When I was in the past Garakais, I could have done that kind of thing, so I developed in a different way. What will happen when this becomes a smart phone with the trend? As easily conceived conclusion will be in the same world as PC, we can not absolutely do it globally even if we look international, so we give up early and take measures in the same way as other PCs. For example, to prevent multiple IDs, and the robot comes to pick up an accountCAPTCHA (capture)We are preventing it by the mechanism that is not it? I do a lot of things on google. I think that there is no other choice but to finally come to the wind. I think that it will be good to consider how to want to do in the long term in advance. that's all.
Questioner C:
Thank you very much.
Takagi:
I'm sorry I have over the time. It is over, thank you very much for your attention.
Related Posts:







