"FinSpy" to record every action without being detected by antivirus software
Bypassing the detection of more than 40 types of anti-virus software, all the images are recorded via the webcam of the PC, the sound from the microphone of the PC is recorded as well, and all the character input from the keyboard is also recorded All the awesome software This "FINSPY"is.
This is a new project by Wikileaks that can search companies that sell systems that monitor and tapping various people for the government, police, military, information intelligence "The Spy Files"Gamma" which is one of the companies listed in the company, PDF files and movies for actual presentation are released.
The Spy Files - Remote Monitoring & Infection Solutions: FINSPY
http://wikileaks.org/spyfiles/docs/gamma/289_remote-monitoring-and-infection-solutions-finspy.html
The Spy Files - Remote Monitoring & Infection Solutions: FINSPY
http://wikileaks.org/spyfiles/docs/gamma/301_remote-monitoring-and-infection-solutions-finspy.html
All computers with this "FinSpy" installed will be able to remotely control. For example, it can be installed on the Internet cafe's computer, record calls by Skype, and shoot the face of the user with the webcam built in the internet cafe's personal computer. Also, by installing it on a computer of a criminal organization, it is also possible to record what country you are currently in, and what kind of conversation you are making via a microphone on your computer.
◆ FINSPY

The distinctive features are as follows.
· Not detected by more than 40 anti-virus software
· Eavesdrop on all calls, chats, file transfers, video calls and contact lists on Skype
· E-mail, chat, voice calls can be recorded all
· Record all web camera images and record all microphone sounds
· Tracking targets across countries
· Secretly copy files without being noticed from the hard disk
· A process-based keylogger that enables faster analysis (meaning it is easier to identify because you can record all the character input from the keyboard, you can also know on what software you input)
· Remotely live target systemDigital ForensicPossible (track past actions by restoring or copying files in the PC without being noticed by the other party)
· Filtering to record only important information
· Operate on Windows, Mac OS X, Linux
· Recorded data encrypted with RSA 2048 and AES 256
· Because access to a PC where all communications are tapped is via an anonymous proxy, there is no worry that this will be tracked
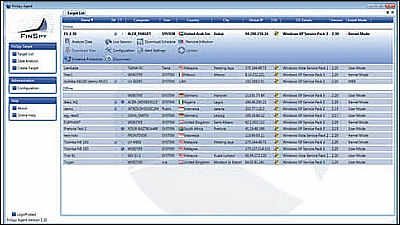
This is "FinSpy Master" and "Proxy". Full control of target system, data and connection log can be stored in secure storage.

This software is "FinSpy Agent", you can intercept, set up, and analyze data sessions of partner's PC with Live live live
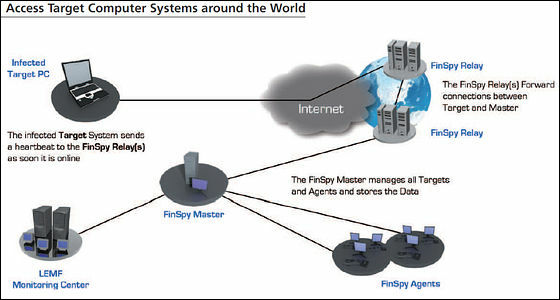
The whole system configuration diagram of FinSpy is like this. After installing FinSpy in the target PC, data is transmitted via "FinSpy Relay" via the net, all data is incorporated in "FinSpy Master", and data analyzed by "FinSpy Agents" is viewed It is a mechanism.
Easy to use interface
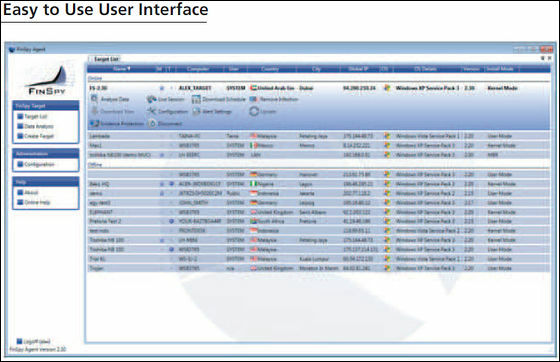
Setting screen
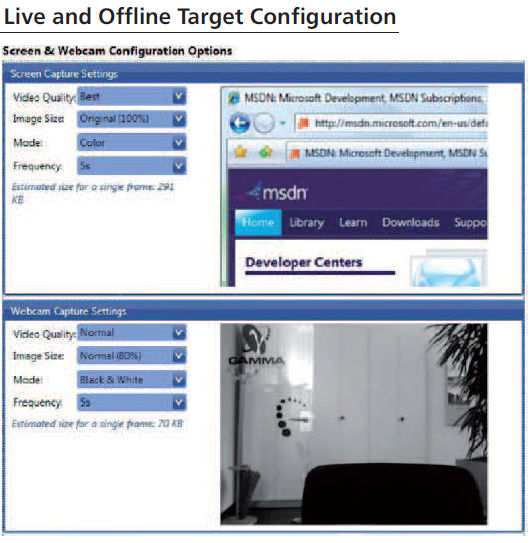
The recorded data is analyzed automatically whether it is important or not, and can be viewed by multiple data view
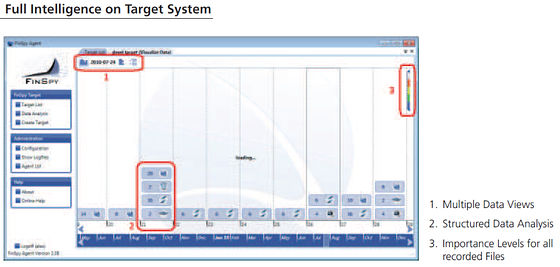
Let's see the movie of the presentation as to what kind of situation to use this

Target using the computer that installed "FinSpy"

I use webcam and microphone to talk with Skype
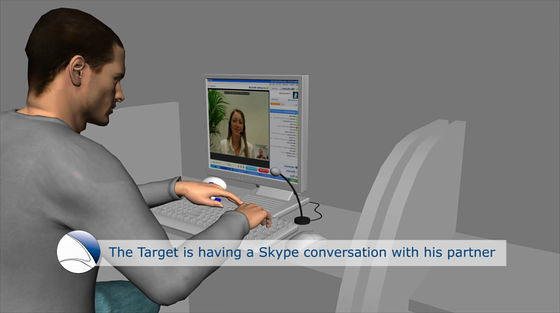
Since "FinSpy" has already been installed, it seems like this from police investigation headquarters and government agencies. The screen of the desktop, the expression of the target shown on the web camera, the speech you are talking to, and the character string you are typing on the keyboard are all visible.

Also,TruecryptSuppose you are copying a file from an encrypted area using an open source encryption software.
Copying encrypted files with this feeling

In that case, it is possible to access the encrypted file remotely

In addition, this software has actually been used by government agencies and intelligence agencies around the world for several years, has helped to gather information on target organizations and individuals, and led to the success of the strategy .
Related Posts:
in Software, Posted by darkhorse