A way to decipher the WEP of the wireless LAN in the blink of an eye will finally appear, and the schedule program will be released soon
CSS 2008 (Computer Security Symposium 2008), It is said that Professor Masakatsu Morii of Kobe University announced an algorithm to instantly decipher WEP which is the encryption method of wireless LAN. Above all, the point that it is not a method requiring a special environment already known, but it is easy to break through in a normal environment. Moreover, despite the openness of the decoding program due to various circumstances, it is scheduled to be released soon.
Because Nintendo DS which is a handheld game machine currently supports WEP in encryption, there are possibilities of various problems in the future.
The outline is as follows from what method is what it is.
We proposed a method to decipher WEP instantaneously in CSS 2008. - Morikita Morii Profile of Kobe University
How to decipher WEP in a moment. . . "Realistic Method of Cryptanalysis of WEP" announced at CSS 2008 | Kobe University Literary Education "Information World" Lecture (Professor Masakatsu Morii Graduate School of Engineering)
Method of deciphering WEP (encryption method of wireless LAN) in a moment 【Supplement】 | Kobe University Educational Principle of Liberal Arts "Information World" Lecture (Professor Masakatsu Morii Graduate School of Engineering)
Method of deciphering WEP (encryption method of wireless LAN) in a moment 【Part 2】 | Kobe University Liberal art theory "world of information" lecture (Professor Masakatsu Morii Graduate School of Engineering)
First of all, it was said that "WEP can be broken down in 1 minute" before, but since it is actually a method using ARP rejection, it can not be deciphered in a normal environment .
Slashdot · Japan | 104-bit WEP can be torn if it is 1 minute
"Break 104-bit WEP in less than 60 seconds" Published thesis - @ IT
The method described in the paper strengthens the attack against the RC4 algorithm which is the basis of WEP. As a result, cracking time is greatly shortened, and it is said that the 104-bit WEP key could be cracked with a probability of 50% within 54-58 seconds.
Encryption technology WEP, will this be the last time - @ IT
Thanks to this discovery, Mr. Bito says that if one button is pressed, a tool that can break WEP in less than 10 minutes is expected. In other words, whether it is a conference room compatible with wireless LAN or a coffee shop in the neighborhood, it becomes a tool that can be devastated hacking.
However, as this method of collecting 40,000 packets of ARP packets was extremely special,More than half of the companies, 59%, use WEP, It seems that the current situation is that the transition to more robust encryption such as WPA has not progressed.
And the method announced this time is not an ARP packet but "It is possible to calculate WEP key from arbitrary IP packet". It is said that WEP key can be derived from communication observation of 20 MB or less. This is to decrypt without making unauthorized access and assuming a special environment in the usual WEP wireless LAN environment.
The flow of the proposed method is as follows.

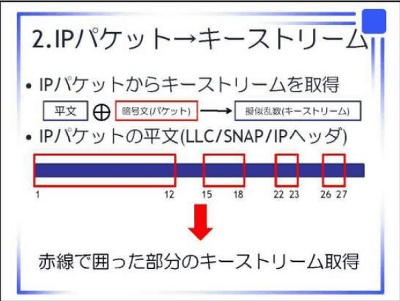

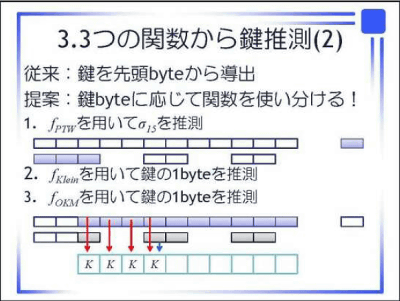
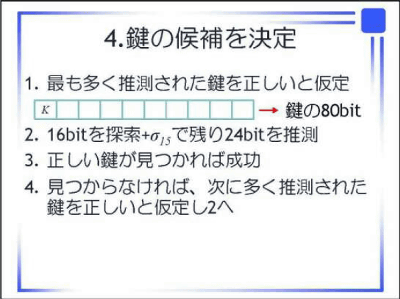
I do not quite understand what it is, but it's probably its implementation environment.
OS: Windows XP SP 2
CPU: Athlon 64 X2 4600+ 2.41 GHz
Memory: 1 GB
Language used: C
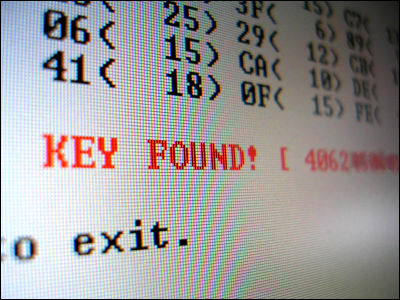
As a result of eavesdropping and attacking the normal WEP wireless LAN without actually performing the ARP re-injection etc., the wiretapping and decoding time of the 20 MB eavesdroppers is only 10 seconds and it is decided to decrypt the 104 bit WEP key success. In other words, it seems to have proven that WEP key can be instantaneously derived from arbitrary IP packet in ordinary WEP wireless LAN environment.
As features, it is compatible with ordinary WEP wireless LAN, that it is fast, that it can decode with very little communication volume. In other words, if only a tool that can automate these series of operations comes out, anyone can easily decipher WEP with a single click.
And it is announced at the site of Professor Masakatsu Morii of Kobe University that the decoding system (program) is open soon.
In short, WEP does not make sense as encryption system as it is, and it is necessary to shift to WPA and WPA 2 at an early stageCall Sophos in the official blogis.
Related Posts:
in Note, Posted by darkhorse